I think you’ve already heard about this virus. For the past few days, it spread to computers in 74 counties! The biggest impact we can see is in China, Russia, Peru, France, and Canada. In only one day it infected German rail stations, Chinese Universities, the Russian Interior Ministry, British hospitals, and other government institutions. Impressive, isn’t it?
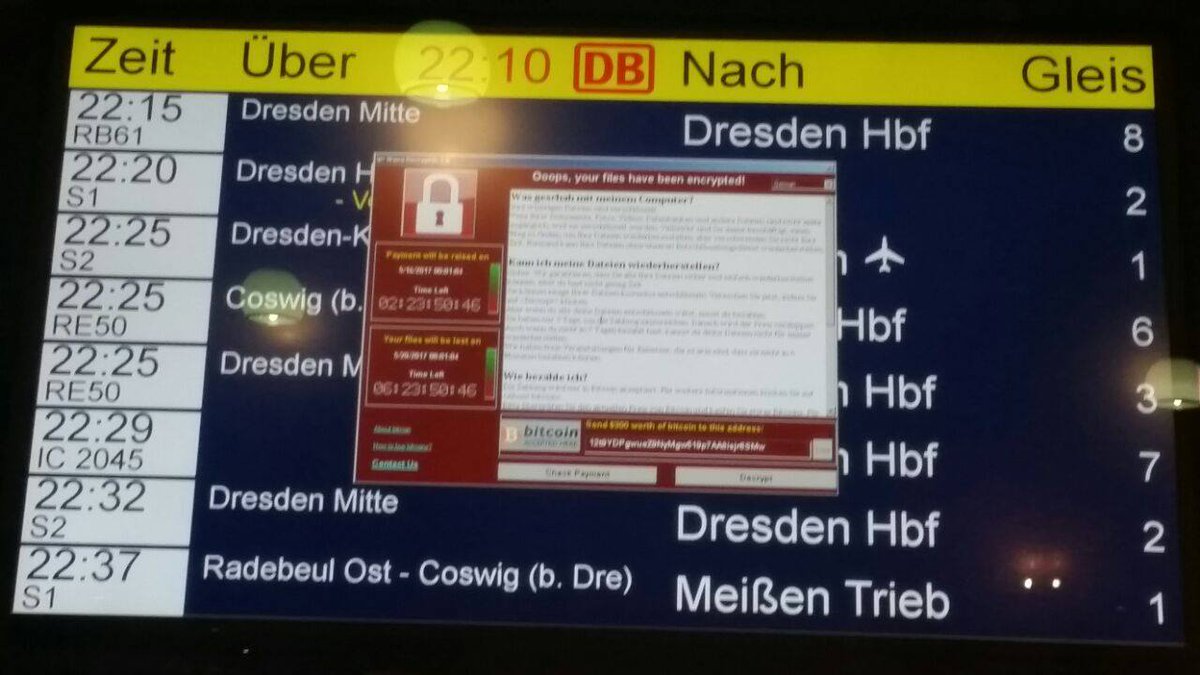
How WannaCry (or Wanna Decrypt0r 2.0) is spreading and what is it capable of?
You can infect a PC by downloading some pirate programs, clicking on suspicious pop-ups with fake “update” links, and via emails. Be careful before clicking on some attachments and running programs from an unknown source.

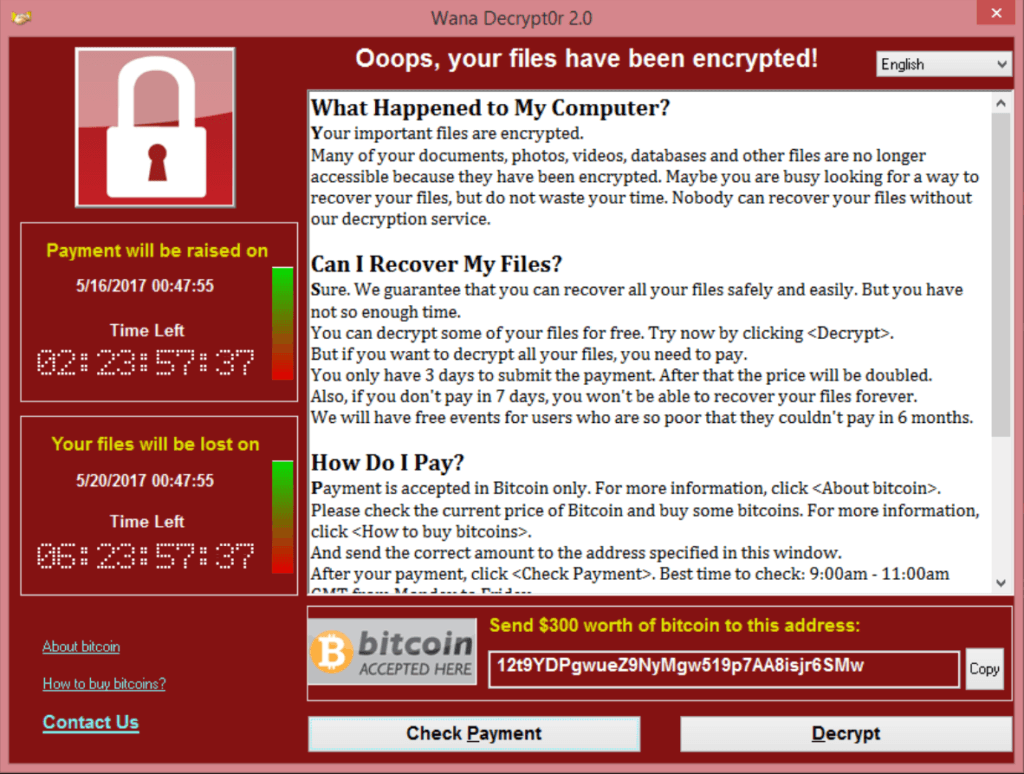
When it infects your PC it will scan all files and encrypt them with WNCRY extension. Access is blocked to images, documents, music, and system files. After that, you will see the message on the screen “Oops, your files have been encrypted” and demand to pay $300 in Bitcoins to decrypt your files. However, no one guarantees that after paying the ransom the files will be decrypted.
To ensure that this epidemic bypasses you immediately need to install the patch MS17-010 from Microsoft. After installation, restart the computer. You need to scan your PC and in the case of detection of malicious attacks (Trojan.Win64.EquationDrug.gen) – reboot the system again and make sure that the patch MS17-010 is installed.
If you are already infected follow the steps below to eliminate the virus.
- It is necessary to enable the safe mode with the network drivers loaded.
- Then you need to scan the system with a strong antivirus program and remove all detected files
The final step for the user is to restore the encrypted files, you can only do this after Wannacry is uninstalled. Otherwise, system files and the registry can be damaged. For this, you can try different decryption programs, but they don’t guarantee to restore files.
So as we can see viruses don’t sleep and are evolving every day. WannaCry will be on our next list of the top 10 viruses.