Computer viruses are really similar to real-life ones. They can infect thousands of PCs in just one hour, so we can call it an epidemic. Agreed, it is exciting to look at how each virus works and how antivirus programs have become necessary for anyone with an electronic device. So, we have made a list of the top 10 most dangerous viruses in history.
-
CIH, 1998
This virus was created by a student from Taiwan whose initials were CIH. It had spread across the network on April 26 – the date of the Chernobyl accident, so many users call it simply – Chernobyl. This virus is dangerous because it not only overwrites data on the host PC’s hard drive, making it unusable, but it is also capable of overwriting the BIOS of the host. After this, the PC can’t boot up. For the time being, CHI or Chernobyl has infected nearly half a million PCs worldwide.
-
Morris worm (1998)
The first ‘Worm’ virus. It gained a huge amount of attention via the press, and the creator was the first person convicted in the USA under Computer Fraud and Abuse Act. November 1998 was the month when one virus paralyzed the entire Internet’s work, resulting in direct and indirect losses totaling $96 million. It crashed a lot of PCs because of a minor mistake in its’ code – it continued installing on one PC an unlimited number of times, causing the total death of the system.
-
Melissa (1999)
On Friday, March 26, 1999, a new problem appeared– Melissa. It’s an email-based virus. You received an e-mail that contained just one sentence, “Here is that document you asked for…don’t show anyone else. ;-),” with an attached Word document. Nowadays, we understand that it is a virus, but in 1999, it was something new. Those who opened the DOC file (thousands did so) allowed the virus to infect their system and send this e-mail to all the contacts in your e-mail account using your name. Even worse, this virus modified users’ Word documents with quotes from the TV show “The Simpsons. The cybercriminal responsible was caught and sentenced to twenty months’ imprisonment.
-
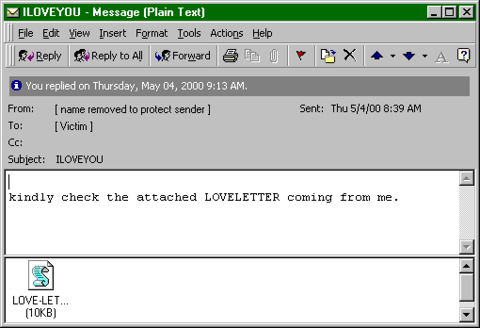
ILOVEYOU (2000)
The most romantic one on our list of dangerous viruses is the ILOVEYOU virus. Maybe because of its lovely name or insidious strategy, it infected 45 million users for two days! The CHI virus would have taken about two years. So how did it work? A person receives an e-mail with a ” LOVE-LETTER-FOR-YOU ” file with a VBS extension (Visual Basics script). When entered into the system, it would replace all your files, images, and music and then spread itself to all your contacts. The damage was enormous – no one had expected this type of virus. And do you know what? The creator was found but wasn’t charged for this crime because the Philippines had no laws against cyber criminals then.
-
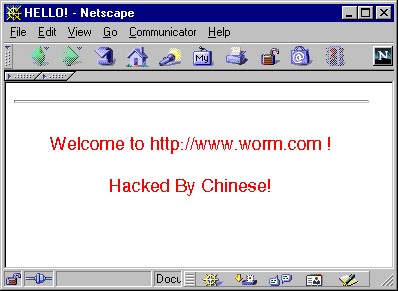
Code Red (2001)
July 13, 2001 – The day when another virus infected the Web. This time, you didn’t need to install a malicious file or even open the e-mail. Code Red or Bady virus just needed an Internet connection that changed the Web page you opened by displaying the text “Hacked by Chinese!”. It spread quickly, and it took less than a week to infect almost 400 000 servers and nearly one million damaged computers.
-
MyDoom (2004)
My Doom appeared in the malware world on January 26, 2004. Not for days, but for hours it infected nearly 2 million PCs! So how did it work? It came as an attachment to an e-mail with an error message containing the text “Mail Transaction Failed.” When you clicked on the attachment, it duplicated this e-mail to all addresses found in your address books. To stop this invasion was tough because the virus blocked access to the sites of antivirus software developers and Microsoft update services.
-
Sasser (2004)
This virus impressed the world because it managed to shut down the satellite communications for French news agencies and even led to the cancellation of several Delta airline flights. Impressive, isn’t it? Instead of e-mail, this virus used a security flaw in non-updated Windows 2000 and Windows XP systems to break into the system. Once the virus infected a computer, it looked for other vulnerable systems. Infected systems were experiencing repeated crashes and instability. Interestingly, this virus was written by a student who released the virus on his 18th birthday. He was fortunate because he wrote the code when he was a minor, so he just got a suspended sentence.
-
Bagle (2004)
At the beginning of 2004 new virus appeared – The Bagle worm. It has a classic method of infection – via e-mails. Why have we put it on the list? Because this virus is the first one created to make a profit by gaining access to financial, personal, and other information. Since then, a malware-for-profit movement has appeared and is currently a huge problem for many users and antivirus companies.
-
Conficker (2008)
Worm Win32 Conficker or just Conficker is a very insidious virus written to attack the Microsoft Windows systems. Using OS vulnerabilities, “Conficker” slipped unnoticed by antivirus programs, and even worse, it blocked access to their databases and updates for the OS. The names of all services were substituted, and the virus was registering in different parts of the system, so it was almost impossible to find and destroy all its fragments. There were more than 12 million infected computers worldwide, and it taught antivirus companies and OS providers a harsh lesson to improve their security.
-
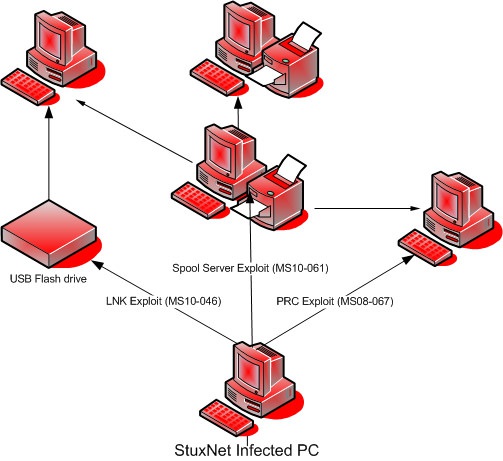
Stuxnet
Last but not least was the worm called Stuxnet. It was discovered in 2010, and you’ve probably already heard about it. It targeted industrial control systems that monitor and control large-scale industrial facilities, including power plants, dams, waste processing systems, and chemical and nuclear operations. It allows the hackers to take control of every important system control without being noticed. This is the first-ever attack that allows cybercriminals to manipulate real-world equipment and bring huge damage to world security. Iran has suffered the most damaging effects of Stuxnet (nearly 60 percent of all the damage caused)..
So, as we can see, it took less than 20 years to develop viruses from the commonplace spam e-mail to a massive threat to the world. What will be next? Will antivirus programs be capable of protecting us in the future? And what about world peace? There are a lot of questions, and there are no definite answers. Leave a comment below. What do you think awaits us in the future of viral progression?