Have you been noticing strange decelerations or even freezings in the work of your computer lately? Has it become noisier, as if it struggles, loaded with tasks when you know you gave it none? If this sounds familiar, you need to find a reason for such slow PC trouble. It is unlikely that your PC has a hardware problem since you didn’t see it receiving any physical damage. It might be an HDD problem, yes, but there are still many software issues that might have occurred, so the best thing you can do is to make sure they are not the cause.
Reboot your PC
Start with a restart. Even if you’ve done it several times already, just as a matter of procedure, do it again. Nothing? Ok, let’s try other things.
Check background tasks
Some of the programs on your PC work in the background, often without even communicating with you. And that is OK. Antivirus programs, for example, ought to turn on automatically upon system booting. But there is software for which there is no need to work in the background. However, despite slowing down the computer, some programs automatically put themselves on a startup list which means the system will launch them once it boots.
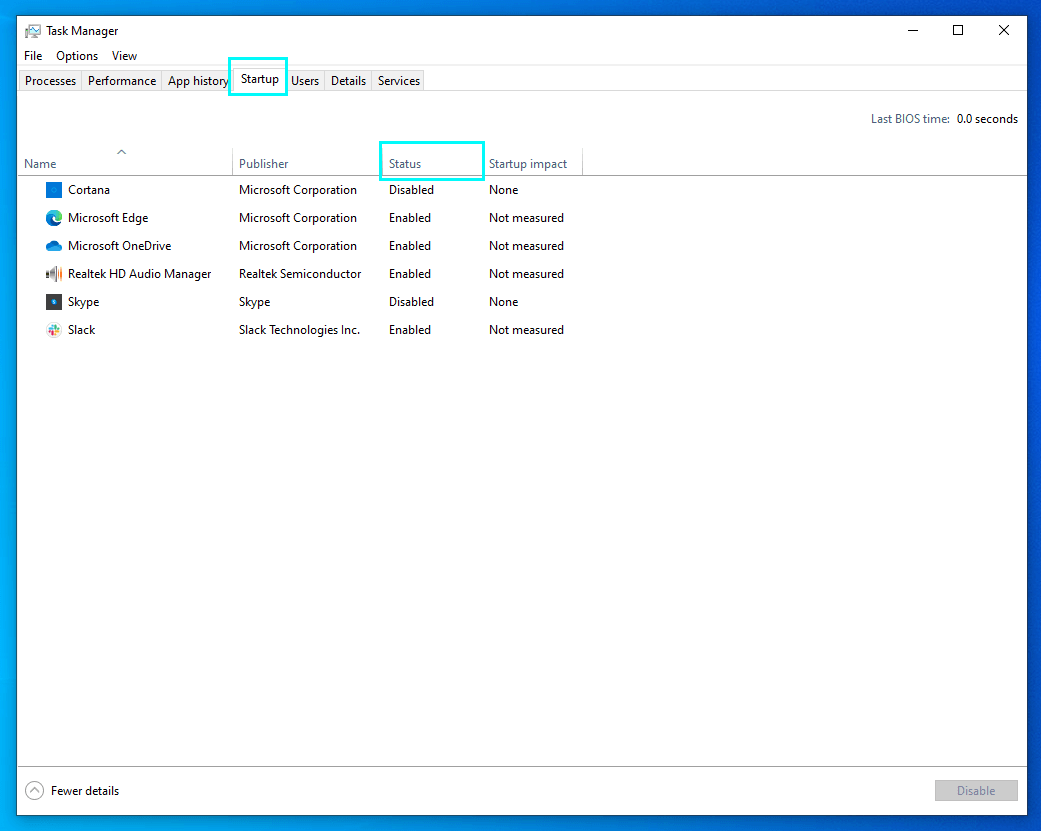
Here is Windows 10 instruction on how to check the programs listed for startup launch:
- Press Ctrl+Shift+Esc to access the Task Manager.
- Go to the Startup tab. You will see the list of programs that start at once after Windows boots. In the Status column, you will see “enabled” and “disabled” values. The former means that Windows will launch this program upon startup.
You can disable any program from this list, or even all of them, to check whether background tasks cause the deceleration of your PC. You will be able to enable them back again whenever you like. If you’re not up to that, you can disable only the programs about which you are suspicious. - You can click any entry in the list with the right mouse button and choose Properties in the dropdown menu. In the properties window, you can see the exact name of the program by googling, which you can learn what exactly this program does.
- To disable the startup launch of the program, right-click the entry right in the list and select Disable.
NOTA BENE! If your antivirus software is performing a scan, this takes a lot of resources. Giving the CPU other tasks at the same time may result in low performance. Let the scan complete, and then see how quick your PC is. If the problem remains, proceed to the next possible anomaly source.
Update the OS and drivers
Your computer might be working slowly because of the outdated hardware drivers conflicting with the latest system software or vice versa. If it is so, the best solution is to update everything. Windows 10 updates automatically, but users can postpone updates or specify a date to install them. It is unlikely but possible that your hardware drivers were designed to work on the system update you haven’t yet installed. However, the opposite situation is pretty much possible. Windows 10 only adds the latest device drivers to its significant updates. But the latter hardly include drivers for rare and specific devices. Therefore, it is reasonable to manually check for device drivers on the manufacturers’ official websites.
Or you can use special applications provided by hardware manufacturers to update drivers automatically as graphic cards and printer producers do. But not always there is such support.
Use Start Menu search and seek Windows Update, where you will see whether any updates are waiting for installation.
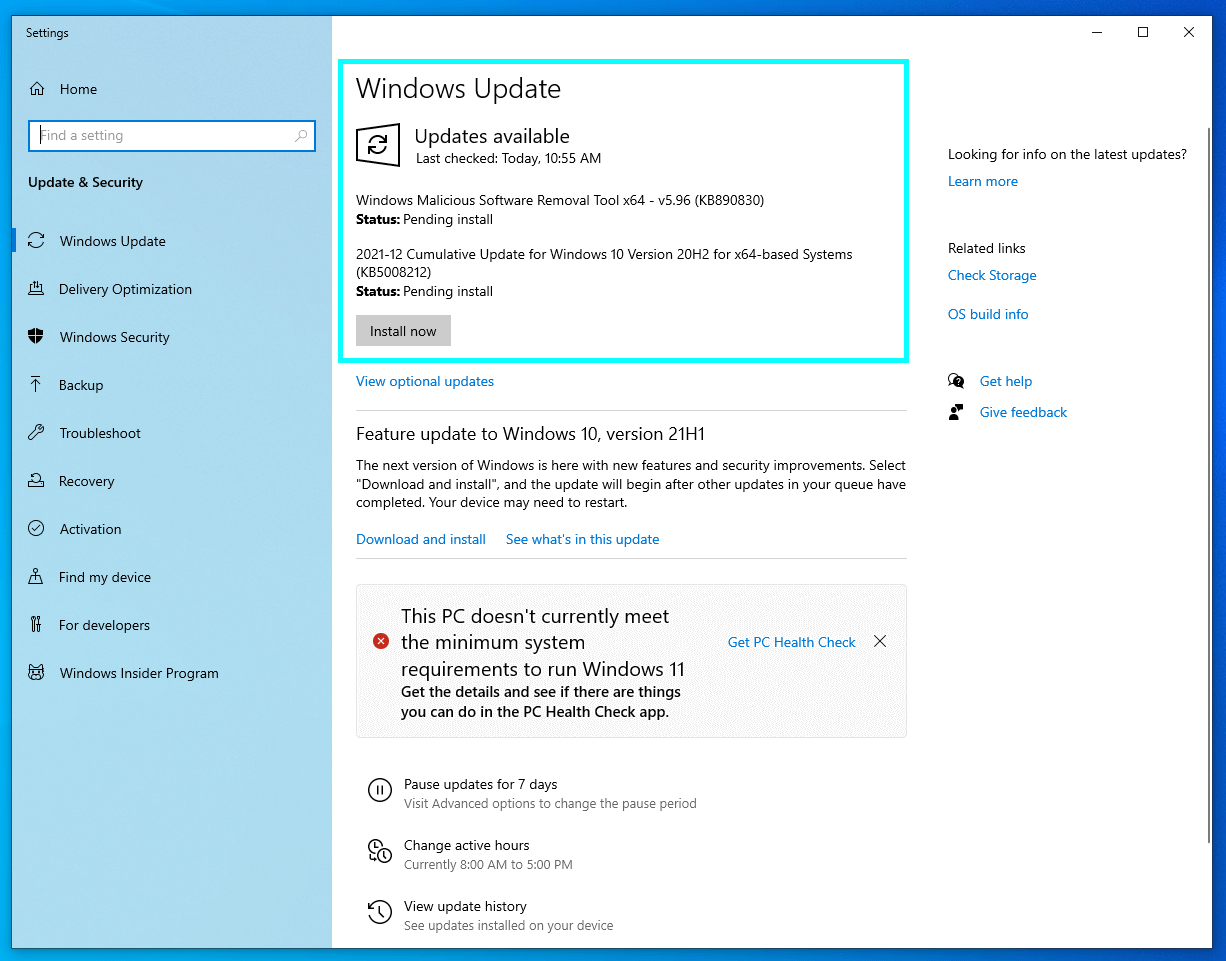
Reboot your PC after all the updates.
Free HDD space
Swapping is a process of loading data that exceeds the size of physical RAM into virtual RAM – a file on the HDD called swap file (also: page file). Its size can amount up to 4 times larger than that of the real RAM. The lower limit is 1,5 of the RAM.
Now you see why the OS needs some free space on the hard drive for smooth operation. Check whether your HDD is full. Of course, we’re talking about the same hard disk where your system is.
Clean up Temp files
Creating, storing, using, and deleting temporary files is a process that accompanies your computer’s execution of complex programs. There is a folder in the operating systems for these temp files. Some of the files stay there for a long time, and that’s okay.
Temp files piling up can cause a visible deceleration of the PC. The more so if there is a hard disk drive overload.
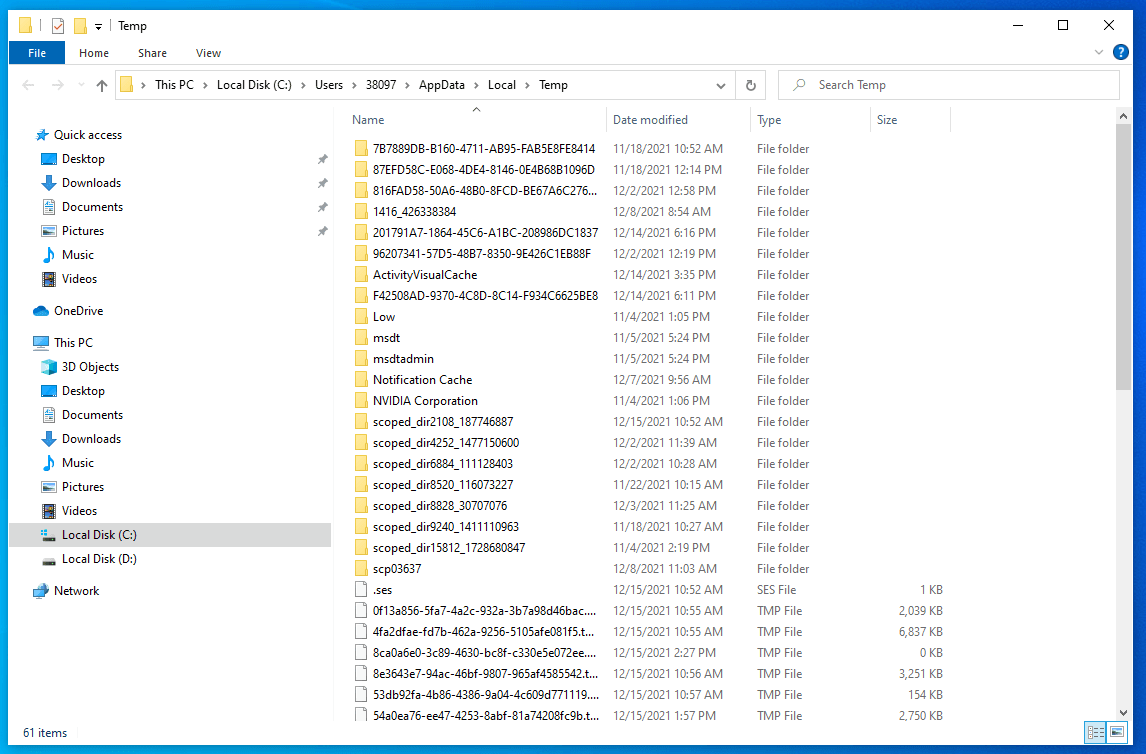
Follow this instruction to remove temporary files:
- In the Start Menu search bar, type %temp% and hit Enter.
- The temporary files window will open.
- You can delete all of them. If some programs use any of these temp files right now, Windows will notify you, and you’ll be able to skip that very object. The rest of the files will be created again if they are needed.
If the temporary files were the reason for your PC slow down, you will feel the improvement right away.
Disable/remove browser extensions
If your computer becomes slow specifically as you use the Internet, the problem may lie in browser extensions. Users are often unaware of how many useless extensions they install into their browsers while surfing the Web, mindlessly clicking consent buttons without even looking at the proposition. You can either turn unwanted extensions off or even delete them. Considering many extensions are PUPs alright, maybe the second option is preferable.
However, before removing any extensions, make sure you are not browsing with many browser tabs open and active. Some users don’t care about it, while the open tabs can banally overload the PC.
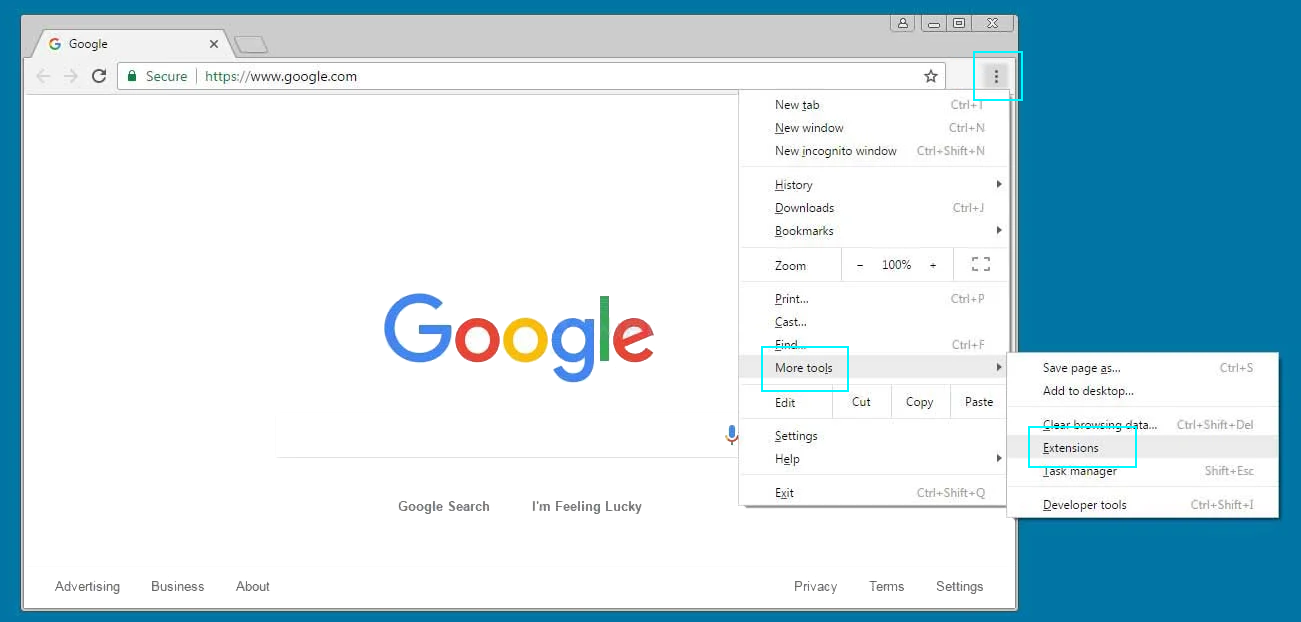
To remove extensions in Google Chrome, press Chrome Menu (three dots icon at the upper right corner) and choose More Tools in the popping-out menu. In the next menu, select Extensions. Find an extension you want to disable or remove and do it. Flip the blue switch to disable the extension, press Details to learn more about it, and, finally, press Remove to get rid of it.
Do the anti-malware scan.
Many types of malware are capable of slowing the computer they target significantly. The most prominent example is a Trojan horse that uses your system’s resources to mine cryptocurrency.
Related reaning: Coin Miners – What is it? How to know that you are infected?.
Open your antivirus program control panel and run a deep scan. Since there is such malware that only some of the existing security programs can detect, it is advisable to use a different counter-malware software alongside your antivirus to achieve a better effect. We recommend GridinSoft Anti-Malware, a safety program that can function as a powerful scanner utility as well as your primary system antivirus.
Rule out CPU cooling problems
Central processing units can lower their frequency to reduce heat in the chip. It is called “throttling.” Poor ventilation within the system unit can trigger this safety measure.
Remove the cover from the system block and see whether hair, dust, and dirt obstruct normal airflow. Clean the interior of the system unit accurately. If you’re not sure what is allowable during cleaning: check with this article on cleaning a system unit.
Attentively examine cooling grids and fans. Consider replacing a CPU fan if it is out of order. By the way, graphic cards feature cooling fans as well. If your PC decelerates running video games, check the graphic card fan as well.
Check the hard disk
Although software causes of the computer being slow are more probable, we should not ignore the possibility of the hard drive malfunction. What can we check in a hard drive, and how? If it is damaged and if it is fragmented. For both examinations, we can use standard tools featured in operating systems. Both procedures take time.
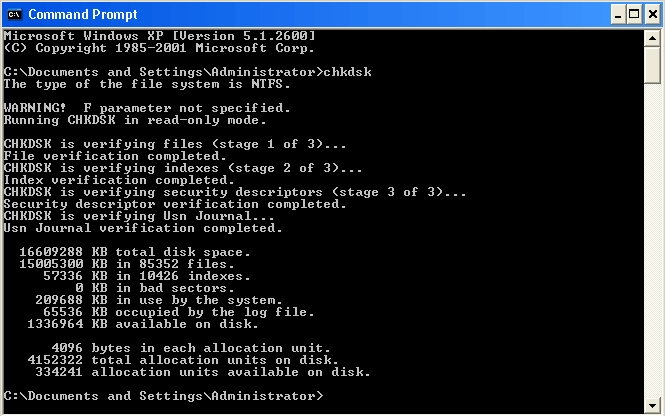
To check HDD for errors, run CHKDSK.
- Type “cmd” in the Start Menu search bar and open the found item, the Command Prompt.
- Press the right mouse button on the found Command Prompt and select Run as administrator.
- In the command prompt, type the command:
chkdsk C: /f /r /x
- Press Enter.
This command launches a disk check attempting to fix any error or bad sector on the hard drive. CHKDSK will mark hard-damaged sectors so that they are not used again. If you’re up to scanning another drive, type its drive letter instead of “C.”
If your PC is Apple, use Disk Utility to do the same thing. Take this path:
Launchpad (Dock icon) – Other – Disk Utility
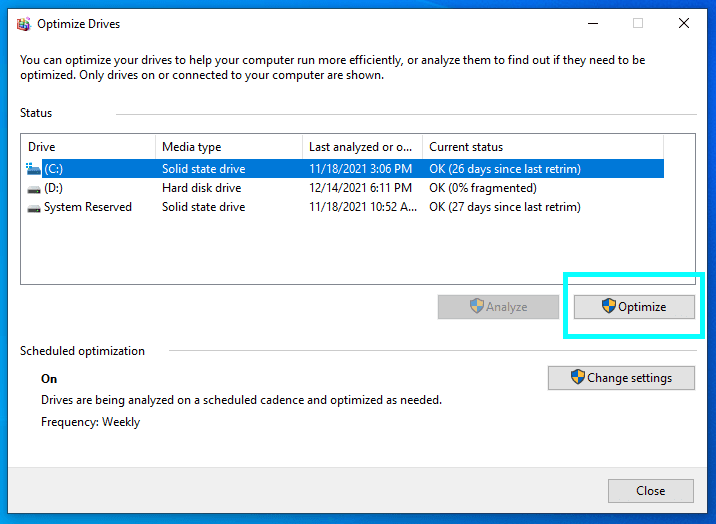
The second thing to be checked is disk fragmentation or, in other words, the extent to which data is scattered across the hard drive. It takes much more time to operate with a fragmented disk. To defragment the HDD, use the Windows in-built optimizer.
- Search for Defragment and Optimize Drives in the Start Menu search bar.
- Open the found utility and, in its window, select one of the drives and press the Optimize button near its entry.
Check hardware
If nothing worked, it is time to check the hardware then. There are three PC components whose defects might cause the symptoms you’re trying to cure: CPU, motherboard, and RAM.
To do the maximum from home, you can use Ultimate Boot CD, software created to detect hardware issues by measuring the time it takes your PC to do some specially designed tasks.
The UBCD is downloadable nowadays; it is not necessarily on a CD.
A device wherein the UBCD finds a defect should be replaced or fixed.
READ ALSO: How to Fix High CPU Usage.
Reinstall Windows
An operating system like Windows is a highly sophisticated program. As you use it and interact with it, it becomes more and more customized, thus deviating from its most optimal state.
Normally, these deviations are minor, but sometimes they get truly significant due to software conflicts that are hard to track. If the UBCD detected no hardware problems, but still there is something wrong with the computer’s running speed, it might be reasonable to cut the Gordian knot by reinstalling the system. If you choose to install the system anew without keeping your files, you will lose your data. However, since you can still launch your PC, just back up your files and proceed.
Here is the Windows 10 Reinstallation Manual.