Cookies are an essential part of how the Internet works. They help websites remember your logins, shopping carts, and other settings to make your browsing experience more convenient and personal. However, cookies can also pose a privacy risk if they fall into the wrong hands. Below, we’ll explain what cookies are, what they’re used for, and other key details.
What Are Cookies?
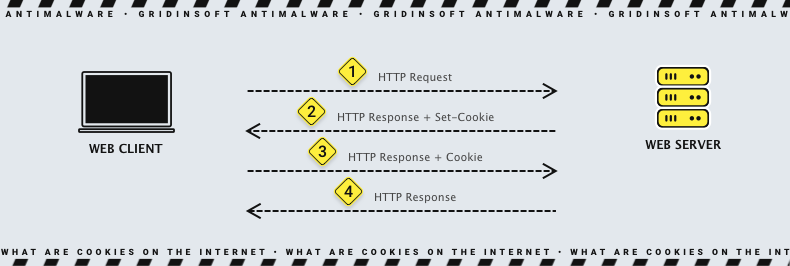
Cookies are small files that web browsers store at the request of a website’s server. They can contain details like the contents of your shopping cart or your browsing preferences. When you revisit a website, the browser sends these stored cookies back to the server, allowing the site to recognize you and tailor your experience. Some cookies enhance security, such as authentication cookies, while others are used to personalize content. Also called HTTP cookies, these files typically work over the HTTP/HTTPS protocol.
What Are Cookies Used For?
Websites use cookies to make browsing more convenient by automatically remembering your information after you leave or close the page. Consequently, you wouldn’t have to log in again or reinstall your shopping cart if you closed the tab accidentally. Cookies provide a significant part of the Internet experience. Therefore it’s necessary to understand why they’re valuable before deciding whether or not to keep them.
- Session management. For example, cookies allow websites to recognize users and remember their personal preferences, such as sports news versus politics.
- Personalization. When sites use cookies to personalize their advertisements, they usually use customized advertising. This means that cookies help websites create ads you might like based on your data.
- Tracking. Online stores use cookies to remember information about the items someone has previously viewed. This allows them to continue suggesting other things the user may like and keep their carts filled with items they still need to purchase.
What are the different Types of Cookies?
Some of the most significant types of cookies include:
1. Session cookies
Websites employ a session cookie to track a user’s session. Session cookies are erased after the user’s session is over — once they log out of their account on a website or leave the site. Session cookies have no expiration date; this indicates to the browser that they should be deleted once the session is over.
2. Magic cookies
This old term in computing refers to packets of information transmitted and received without alteration. Typically, this would be employed to access a computer database system internal to a business, such as a network. This idea is older than the modern “cookie” we utilize today.
3. HTTP cookies
HTTP cookies specifically designed for web browsers to record, personalize, and save information about each user’s session. A session is the amount of time you spend on a website. Cookies are employed to recognize you when you visit a new website. The server that hosts the website’s data transmits a brief, identifying message to your web browser. Browser cookies are placed by their name and value pairs. These instructions tell cookies where to go and what information to remember.
4. Authentication cookies
Authentication cookies are used to maintain user sessions, created when a user logs into an account via their browser. They ensure that confidential information is delivered to the intended users by associating user account information with a cookie identifier that is unique to each user.
5. Tracking cookies
Cookies that are generated by tracking services are called tracking cookies. This is because they observe user behavior, and browsers transmit this information to the associated tracking service the next time they visit a website that utilizes that service.
6. Zombie cookies
Like the “zombies” in popular fiction, zombie cookies will regrow after being deleted. Zombie cookies have multiple copies of themselves that are not stored in the specific location for cookies. They utilize these backups to re-appear within a browser after they are deleted. Dishonest advertising networks and cyber criminals sometimes employ zombie cookies.
How Do Browser Cookies Affect User Privacy?
Cookies can track a user’s browsing activities, often for advertising. Many people prefer not to have their behavior monitored online. At the same time, users want more transparency and control over how their data is collected. Even if cookies don’t directly contain a person’s name or device information, certain tracking methods can still connect browsing habits to a real identity. This data may then be used for targeted advertising, unwelcome personal profiling, or harassment. Still, not all cookies raise these concerns.
Privacy regulations, like the EU’s ePrivacy Directive, set rules for using cookies. Under this directive, websites must inform users about their cookie practices and obtain consent before using non-essential cookies. Only cookies necessary for the site’s basic functions are exempt. Additionally, the EU’s General Data Protection Regulation (GDPR) treats cookie identifiers as personal information. As a result, any personal data gathered from cookies must comply with GDPR guidelines. These regulations lead many websites to display banners that allow users to review and manage their cookie settings.
Why Can Cookies Be Dangerous?
Technically, cookies themselves are not harmful. They cannot spread malware or infect computers. However, cybercriminals can hijack cookies to access your browsing history and potentially identify your online activities. Understanding which cookies pose risks can help you protect your privacy. Generally, the threat level depends on who created the cookie:
- First-Party Cookies: Created by the website you’re visiting. They are usually safer, especially if the site is reputable and not compromised.
- Third-Party Cookies: Generated by outside domains, often through ads on a page. For example, a single webpage with multiple ads might place several cookies on your browser, even if you never interact with them. Over time, these advertisers can connect your browsing habits across different websites, allowing them to piece together a detailed profile of your online interests and activities.