Locklocklock is a ransomware virus designed to lock your files and demand payment to restore access. Victims can identify encrypted files by the addition of a .locklocklock extension to every affected one.
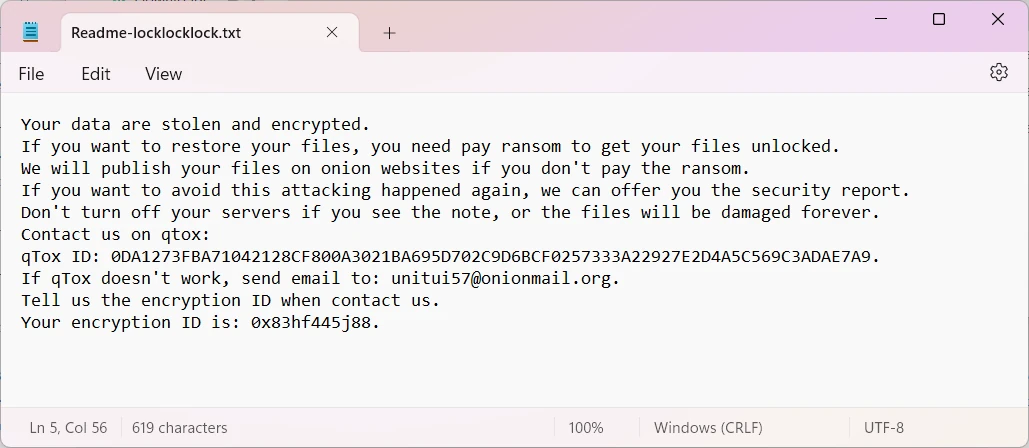
This malware operates under the control of a sophisticated network of cybercriminals who develop, distribute, and profit from it. In every folder containing encrypted files, the ransomware deposits a text note titled “Readme-locklocklock.txt”. This file provides instructions for victims to contact the perpetrators.
Ransom Note Overview
The ransom note is short and stripped of any details, offering little beyond the basics: it explains what has happened and provides a way to contact the hackers – a qTox chat ID and a backup email address. Interestingly, the ransom amount isn’t specified upfront; instead, victims are expected to negotiate the payment terms directly with the cybercriminals via email.
Beyond contact information, the note includes a victim ID – a unique number attributed to this specific attack example. Hackers ask the user to specify it when contacting them, so they can distinguish between their victims. It is possible that they also keep a few other details about the system, which may be used to adjust the ransom sum.
One outstanding detail of the ransom note is the offer of “the security report”. Cybercriminals can apparently provide the victim with the detailed description of how they inject their malware, so one can make conclusions and adjust the protection. It is unclear though how transparent this report is, and whether it may cost additional money.
What is Locklocklock Ransomware?
Locklocklock is a ransomware-type malware that encrypts files on an infected computer and then demands payment in exchange for a decryption key. This ransomware employs robust encryption algorithms, making brute-force decryption virtually impossible. However, this doesn’t mean all hope is lost – there are still ways to attempt file recovery, which I will explain below.
Before encrypting your files, Locklocklock also makes changes to critical system settings, particularly those related to security and file protection. These modifications allow the ransomware to bypass built-in security measures and remain undetected.
After encryption, the malware continues running in the background, which poses a significant threat. Many users mistakenly believe the danger has passed and proceed to use their system normally or try to recover files. However, any new files added to the system will also be encrypted unless the ransomware is removed first. It’s crucial to delete the malware completely before attempting any recovery steps.
How to Remove Locklocklock Ransomware
To effectively remove Locklocklock ransomware, I recommend using GridinSoft Anti-Malware. This software is designed to identify and eliminate malicious files, regardless of the changes they’ve made to your system. You can download the program by clicking the banner below and run a Full scan to let the program thoroughly clean your computer, including files from the most remote areas of the system.
How to Decrypt and Recover Encrypted Locklocklock Files
Unfortunately, no decryption tools are currently available for Locklocklock ransomware. Be cautious of anyone claiming to offer such tools – they are likely scammers or even ransomware affiliates attempting to exploit victims further.
Your best hope lies in the possibility of ransomware operations being disrupted by law enforcement or cybersecurity experts. Law enforcement agencies may arrest key individuals involved in the ransomware’s development and distribution, potentially obtaining decryption keys, which they can then share with victims for free.
Similarly, cybersecurity researchers might discover vulnerabilities in the encryption process and create free decryption tools. Until then, patience and caution are vital. Store the encrypted files on a cloud storage, or on a removable hard drive. In the meantime, there are a few steps you can take to recover your files.
- Option 1. Search for Backups or Online Copies. Look for unencrypted versions of your files in any online storage you’ve used, such as cloud backups, email attachments, or social media platforms. Even older versions of your projects are better than losing everything.
- Option 2. Try Using File Recovery Software. Some ransomware variants use specific methods to handle files, which might allow file recovery tools to retrieve files in their original state. Try a trusted file recovery utility—choose one that supports a wide range of file formats for the best chance of success.
Remember, removing the ransomware is the first and most critical step. Once your system is clean, you can explore file recovery options with minimal risk of further encryption. Stay vigilant, and avoid paying the ransom—it only funds future attacks.