Transport Layer Security is a widely used security protocol designed to ensure confidentiality and data security when exchanging data over the Internet. In particular, we use TLS daily to encrypt communication between servers and clients – a common communication for everyone. Meanwhile, people used to hear HTTPS abbreviation regarding the same thing – secure client-server communication. But what is the difference between TLS and HTTPS protocols? Let’s figure that out.
The difference between TLS and HTTPS
The predecessor of TLS is the previous Secure Sockets Layer (SSL) encryption protocol developed by Netscape. Because TLS version 1.0 began development as SSL version 3.1, the name of the protocol was changed before publication. Therefore, the terms TLS and SSL are sometimes used synonymously. Moreover, you can meet both technologies in use even nowadays. Most web browsers support the use of SSL protocol to secure the connection, despite IETF considering it obsolete in 2014. In some configurations, you may witness a connection error when trying to open the site with the obsolete security standard.
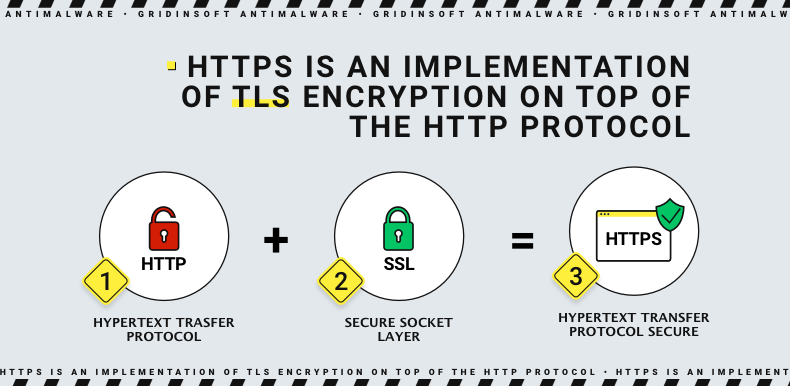
SSL/TLS is what adds S to HTTP. To make the website connection secure, you need an up-to-date SSL/TLS certificate. When you install an SSL certificate, you configure it to transfer data using HTTPS. Thus, the two technologies go hand in hand and, therefore, cannot be operated one without the other. URLs are preceded by either HTTP (Hypertext Transfer Protocol) or HTTPS (Hypertext Transfer Protocol Secure), which determines how the data you receive or send is transferred. To determine if a site uses an SSL certificate, check the URL and see if it uses HTTP or HTTPS because HTTPS connections require an SSL security certificate. Hence, we can conclude that difference between TLS and HTTPS is not that big: the former is a part of the latter.
Why should businesses use TLS?
Because TLS encryption can help protect web applications from data leakage and other attacks, HTTPS with TLS security is standard practice for websites. At that point, there is no difference between TLS and HTTPS, as they mean equal things for you. The Chrome browser promoted the transition of Web sites to HTTPS, after which other browsers followed suit. Today, cybersecurity experts don’t recommend trusting websites that don’t have an HTTPS padlock icon. SSL or more early TLS versions may contain exploitable breaches – thus, the last version (1.3) is the only option. Needless to say that using unsecured connections is like having a shower in a transparent stall amidst the crowded square.
What does TLS do?
The purpose of TLS protocol consists of services to all applications working on it: encryption, authentication, and integrity. Technically, you can apply only a random two of them, providing a sufficient level of security. But in practice, all of them are usually applied for security:
- Encryption – hiding information one computer sends to another. Even if a third party catches it, there will be no way to read the data without the public key. For a bystander, it becomes an unreadable sequence of symbols.
- Authentication – checking the identity of both parties of communication. Usually, that is a handshake and a check of URL correspondence. That ensures the absence of a third party that acts as a shady intermediary and sits in the middle.
- Integrity – detection of information spoofing. The intermediary we mentioned above could not just get the public key and read the info but also inject its own packages, spoofing the result. Integrity checks the hash sum of internet packages at each transfer step.
How does TLS work?
For TLS to work on a website or application, the source server must contain the TLS or SSL certificate. A certificate authority issues it to the person or company that owns the domain. It contains essential information about who owns the domain and the server’s public key, which is necessary for server authentication. Then, a TLS connection is initiated using a sequence known as the TLS handshake. For example, when a user goes to a website that uses TLS, the TLS handshake begins between the user’s device (also called the client device) and the web server. During the TLS handshake, the user’s device and the web server do the following:
- Specify the version of TLS they will use (TLS 1.0, 1.2, 1.3, etc.)
- Decide which cipher suites they will use.
- Authenticate the server with the TLS server certificate.
- Generate session keys to encrypt messages between them after the handshake is completed
The TLS handshake sets a cipher for each communication session. Cipher suites are algorithms that specify the information, such as shared encryption or session keys, to be used for a given session. For example, thanks to cryptography, TLS can establish matching session keys over an unencrypted channel. Cryptography is based on a public key technology. In addition, handshake handles authentication, which consists of the server confirming its identity to the client.
Public keys are used for this. These are encryption keys that use one-way encryption. Anyone with a public key can decrypt data encrypted with the server’s private key to guarantee its authenticity. However, only the original sender can encrypt the data with the private key. The server’s public key is part of its TLS certificate.
Once the data is encrypted and authenticated, it is signed with a message authentication code (MAC). The recipient can check the MAC to ensure the integrity of the data. This is something like the protective foil on a bottle of aspirin, which integrity assures the buyer that no one has tampered with the medicine.
The impact of TLS on the performance of Web applications
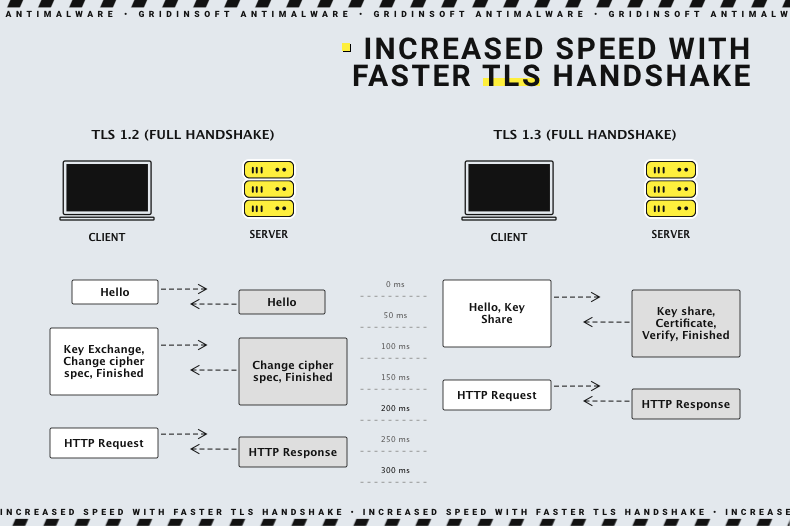
The latest versions of TLS have almost no effect on the performance of web applications. However, because of the complex process of setting up a TLS connection, it takes some time and processing power to load. In addition, the client and server need to exchange data several times before exchanging packets, which eats up precious milliseconds of web application load time and memory for both client and server.
Server administrators can use certain tricks to reduce the potential delay created by the TLS handshake. One such is TLS False Start, which allows the server and client to begin transferring data before the TLS handshake is complete. Another technology for accelerating TLS is TLS session resumption. It will enable clients and servers that have previously exchanged data to use a shortened handshake.
These improvements make TLS a fast protocol that should not affect access times noticeably. As for the computational cost associated with TLS, it is not very important by today’s standards. TLS 1.3, released in 2018, made TLS even faster. Because TLS handshakes in TLS 1.3 require only one round-trip (or two-way communication) instead of two, this reduces the process by a few milliseconds. However, suppose a user had previously connected to a website. In that case, the TLS handshake has no round trips, thereby speeding it up even more.
How to implement an SSL certificate on-site?
Depending on the site hosting parameters, there are different ways to add an SSL certificate. Sometimes, the site should obligatory have the certificate – for example, if it is an e-commerce page. Large hosting providers often offer to host packages that already include SSL certificates. In addition, it is possible to transfer an existing SSL from another host by exporting it from the original server and importing it to the new server. There must be special instructions on the hosting website for this. Finally, some certificate authorities require purchasing a server license for each server hosting the certificate.


