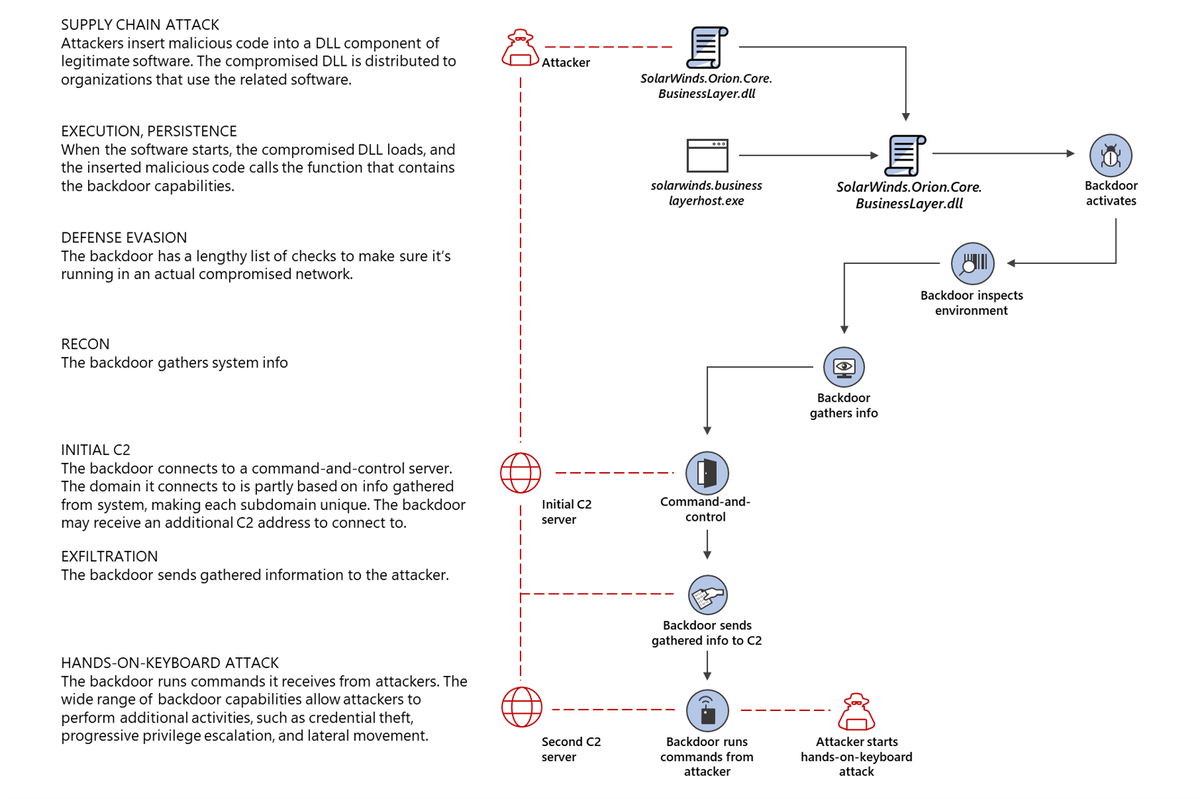
Continue studies oт large-scale attack on the supply chain, for which attackers compromised SolarWinds and its Orion platform. It seems that experts have now discovered another hack group that used SolarWinds software to host Supernova and CosmicGale malware on corporate and government networks.
Let me remind you that the malware used in the original attack was codenamed SUNBURST (aka Solorigate). Microsoft, FireEye and the Department of Homeland Security’s Cybersecurity and Infrastructure Protection Agency (DHS CISA) almost immediately released detailed reports on this threat.
After infiltrating the victim’s network, SUNBURST sent a request to its creators and then downloaded a backdoor Trojan called Teardrop, which allowed attackers to launch hands-on-keyboard attacks that are human-controlled.
However, almost immediately in the reports of information security experts were metioned two more payloads. For example, analysts from Guidepoint, Symantec, and Palo Alto Networks describe in detail that cybercriminals injected a web shell called Supernova into infected .NET networks.
However, Microsoft experts now write that Supernova was part of another attack and has nothing to do with the sensational attack on the supply chain. So, according to a post on GitHub published by Microsoft analyst Nick Carr, the Supernova web shell was embedded in poorly protected SolarWinds Orion installations, which were vulnerable to the CVE-2019-8917 issue.
The confusion arose from the fact that, like Sunburst, Supernova was disguised as a DLL for the Orion application: Sunburst was hidden inside the SolarWinds.Orion.Core.BusinessLayer.dll file, and Supernova was inside App_Web_logoimagehandler.ashx.b6031896.dll.
However, a Microsoft report released last week argues that unlike the Sunburst DLL, the Supernova DLL file was not signed with a legitimate SolarWinds certificate.
This is hardly the fault of the attackers, who have demonstrated a fair amount of sophistication and attention to detail so far. As a result, Microsoft experts are convinced that this malware has nothing to do with the original attack on the supply chain and generally belongs to another hack group.
Let me remind you that SolarWinds was hacked because its credentials were publicly available on GitHub.