Pegasus Spyware is a malicious program that is covered with multiple layers of secrets, rumours and false claims. That military-grade malware is something like a legend, that sometimes makes people think it is rather mythical than real. Still, the real Pegasus appears from time to time, just to notify everyone that it is still the best spying software through all that has ever existed.
What is Pegasus Spyware?
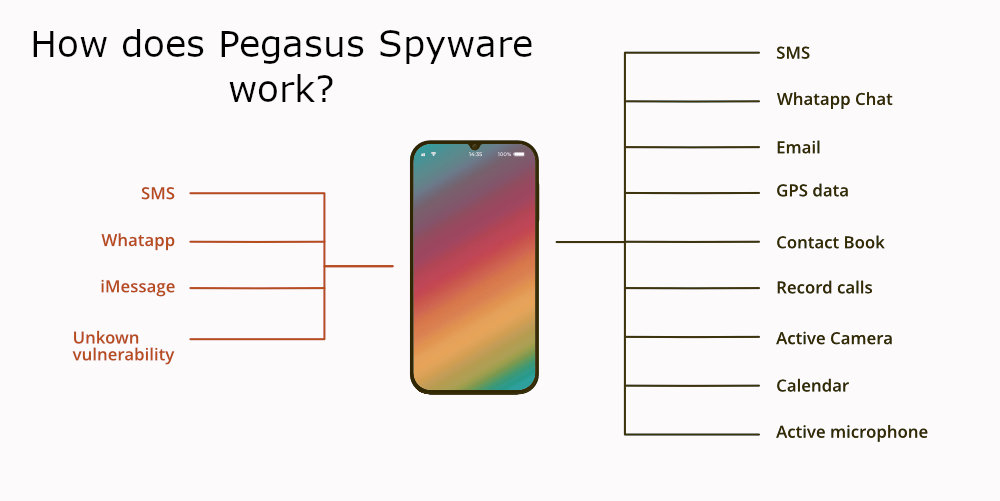
Pegasus is a spying software, developed by NSO Group around 2011. There are no precise terms available, and the community can only estimate its release date by its first appearance. It likely saw its first application in 2012, when it was supplied to the Panama government. Such a mystery is explained pretty simply – NSO is a subordinate company of the Israeli government. The primary purpose of this software was to spy upon anti-Israelian activists, war criminals, and persons suspected of spying for other countries. One may say, it is an example of a cyberweapon – the most modern and pretty effective one.
Its functionality is pretty wide since by design it should be able to provide all possible information about the victim to the person who controls it. Originally, it was oriented on iOS devices, and only several Android attack cases were spotted. There is another malware developed by NSO Group – Chrysaor spyware – that is apparently the Pegasus version which has some adjustments for more efficient attacks on Android devices.
How is Pegasus Spyware Spread?
As Pegasus is a very precise tool that is sold for a pretty big price, there is no massiveness in its spreading – only point strikes that aim at designated persons. Most Google queries like “pegasus spyware download” will lead you to sites that offer a counterfeit for a large sum, or just spyware that will infect your device. NSO Group usually signs a contract with its counterparty (the govt of another country) where the key points about the program usage are stated. In particular, the developers leave the right to decide which amount of functions will be available to a certain country. There is also a contract clause that the government must use the Pegasus only for counter-terroristic actions and for national security needs.
On the devices of users who somehow managed to become a threat to national security, the Pegasus arrives generally through social engineering. Still, the approaches used still differ from classic Facebook spam or something like that. As those persons usually suspect that someone can try to attack them in that way, they will not recklessly click whatever they see. A pretty useful habit for everyone, but not everyone risks getting the Pegasus or spyware, comparable by the level of danger.
The typical ways of this spyware injection are the following:
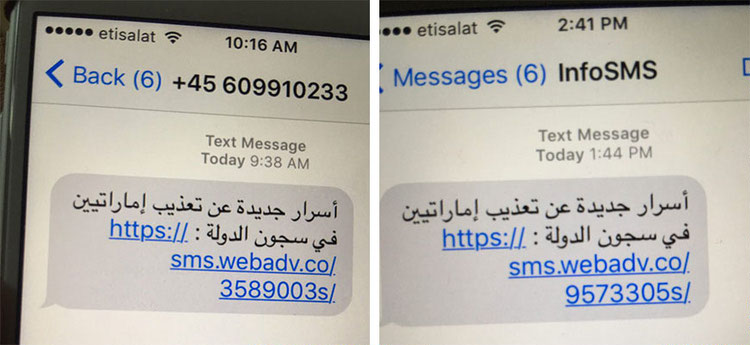
Phishing links are sent via popular messenger or to the email. Usually, those are WhatsApp, iMessage or Facebook – these places are pretty popular among other cybercriminals as well. But this time, the message receives a way more serious disguise – thanks to the “extended” abilities of governmental companies. The latter can easily uncover when the subject of surveillance awaits the delivery, or an invoice from an insurance company.
Zero-click vulnerability exploitation. This rare type of exploit is even harder to imagine in iOS, which stands out with its security features. However, this breach in iMessage is actual for all versions up to 14.7 – then Apple claimed it fixed the breach. To be trapped, it was not required even to open the app or read the message – once received, it already was able to install the Pegasus. As researchers say, this bug could be present in the operating system since iOS 7 – which was released in 2013.
Photos app exploitation. Apple implemented its unique way for iPhones, iPads, Macs and the rest of their product lineup to process the images. However, as it was uncovered, this method made it possible to exploit the Tagged Image File Format (TIFF) files for remote code execution. The breach received the index of CVE-2016-4631. Crooks were sending the photo to a victim, and once they tried to open it – the code was executed and the Pegasus was delivered.
Apple Music MitM attacks. Apple Music application – a cross-platform mobile music library that is present on both iOS and Android, had a security flaw in its version for iOS 11. It lacked the diligent checkup of certain SSL certificates from the server. This cert serves for making sure that the server the app has connected to is genuine, and that no one can eavesdrop on the traffic. However, the uncovered flaw made it possible to spoof the certificate and connect the device to a hacker’s server, giving them the ability to interact with the system without any restrictions and security alarms. That flaw got the index of CVE-2017-2387.
Pegasus Spyware technical details
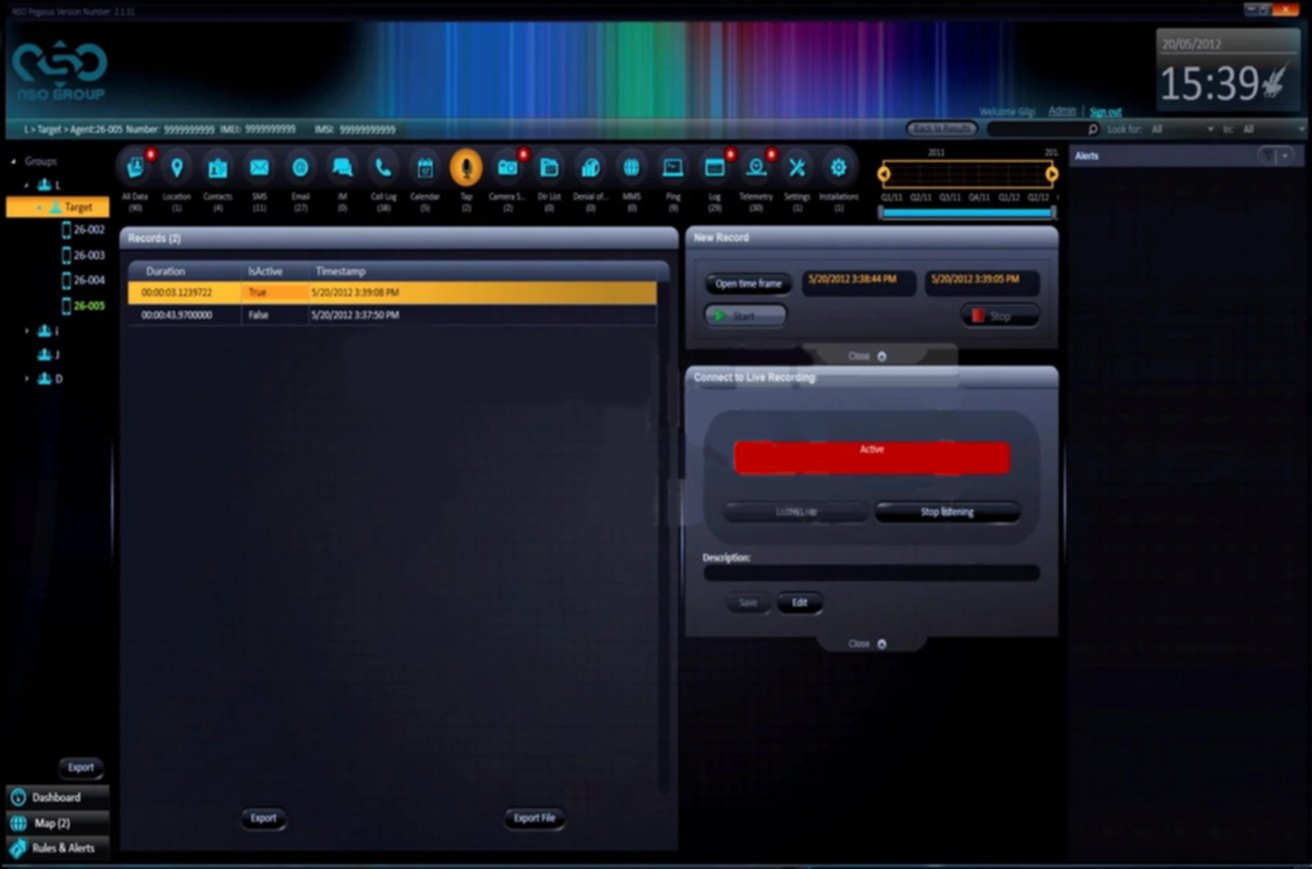
The sophisticated delivery ways I have mentioned above already made this malware quite unique. But the things under its hood are even more amazing – that’s the real representation of how well the malware may be made. Contrary to most of the malware you can see for sale in the Darknet, it is made for being way more autonomous – so even the target who expects the spying will likely miss its presence. It also tries to usethe deep integration to the attacked system by getting information directly from the hardware. That helps the Pegasus to circumvent the OS restrictions or spoofing techniques.
Pegasus is capable of reading SMS, emails, recording cellular and VoIP calls, and enabling the mic and camera to record the environment around the phone. It also has full access to the device memory: this malware can harvest photos and videos present on the device, as well as a calendar and contact book. Thus, it is theoretically capable of deleting certain data from the phone – but it goes against stealthiness. This malware can also grab the information about the current phone location – regardless if there are any software location spoofers present, it will get the info directly from the GPS chip.
Aside from the “deep” data, Pegasus is also able to dig into the programs to get the information. Popular apps like WhatsApp, Viber and Facebook Messenger can easily be accessed, resulting in stolen conversations, and even more contacts leaked. Researchers say about over 50,000 contacts that Pegasus have successfully stolen from the attacked devices. As this spyware always runs with root privileges, it can even recover the data that was deleted some time ago – of course, if it is possible for the storage device technology.
The infamous spyware can also perform self-destruction under different circumstances. If it cannot connect to the command server for more than 2 months (60 days), it automatically destructs itself, together with the packages of gathered data. Alternatively, it may be self-destructed from the device after the corresponding command from the server. It also provides some alternative ways of installation – even with physical access to the device.
Pegasus and the international community
According to the reports from different sources, there are thousands of people from all over the world who were attacked with Pegasus Spyware. Some of them were breached through WhatsApp, some got a malicious iMessage SMS. The only thing that unites them, aside from the payload, is the fact that they had no way to prevent that. Most of the injection cases were done through zero-day vulnerabilities that were uncovered later by the developers. This thing, considering that spying is not a very moralistic act, creates a lot of awkward questions.
First of all, do the governments have a right to spy on the person they want to? When buying the Pegasus, govts promise they will use the tool only against the persons who pose a threat to national security. However, this category’s borders are blurred. Some Muslim countries have proven that by spying on human rights activists, in particular – women who promoted women’s rights in Middle East countries.
Second – is there a way to prevent that? Obviously, this question appeared almost immediately after the Pegasus identification. An infamous Anti-Pegasus tool, anti-spyware software that is designed only to detect and wipe out the Pegasus, became not just an item of constant speculations, but also the disguise for the other malware. Still, it does not provide you with a guarantee that malware will be deleted, since this spyware is extremely secretive.
On the other hand, installing the last security updates and using the most modern smartphones will likely not help at all. Hackers who deploy malware use the most unexpected ways, which are not countered by software patches or other stuff. To be honest, there is no way to prevent zero-day exploitation on mobile phones – just because there are no solutions capable of doing that without dealing serious harm to the phone’s performance. Apple implemented a Lockdown mode in iOS 16, which supposes a harsh restriction on the device’s functionality for maximum security. Will this trade-off be effective? Only time will tell us.