Sextortion is a specific email phishing tactic that was around for quite some time. Over the last few years though its popularity skyrocketed, and some novice technologies make me concerned regarding possible sextortion approaches in future. Let me explain what I mean, what this scam is about, and how to detect and avoid it.
What is Sextortion?
The term “Sextortion” is rather self-explanatory, aside from the fact that this practice has been in use for a pretty long time. That is a type of email scams that aim at money extortion through the threats of publishing explicit visual content with the victim. To look more authoritative, the scammer may claim to have access to the target’s social media accounts.
Contrary to more classic email phishing scams, the attacker will never ask the victim about an action other than sending a sum of money. The reason for such a generous act is, as the villain assures, its possession over some compromising materials about you. Email text often discloses the way these photos and videos were obtained – from a webcam while you were browsing through adult sites, leaked from the hacked phone, or the like.
All this boils down to a simple demand: send the money or I will leak all these nude videos and pics to the public. Some definitely not exaggerating mates say they will post it from your profile, as they have access to it as well. Though ones who try to look more realistic simply promise to tag your entire friends list on a specific social media.
Are Sextortion Threats Real?
99.5% of the time, they are not. Even though some people can have someone’s nude photos on hand, the number of scam emails exceeds the number of these people by orders of magnitude. And since such graphic materials rarely end up in the hands of a stranger, it will be particularly easy to identify the extortionist. This adds up to the generic message text and absence of any proof – some definite signs of a scam. By the way, let’s have a more detailed look at them.
How to detect a Sextortion Scam Email?
Same as any email scam, sextortion bears on 3 psychological tricks: calling for a shock, forcing the feel of vulnerability and feeling of urgency. This leaves its footprint in the text, and eventually makes it somewhat templated in all the scam cases. Let’s review the most popular of them.
Typical Sextortion Email Patterns in Text
With time, there were dozens and hundreds of different text patterns for extortion emails. Most of them, however, are created with the intention of being suitable to any victim. It would be rather uncomfortable for a scammer to adjust the text whenever they target a new group of people. Thus, utterly generic and abstract text with absolutely no personalization is what you would expect from sextortion scams.
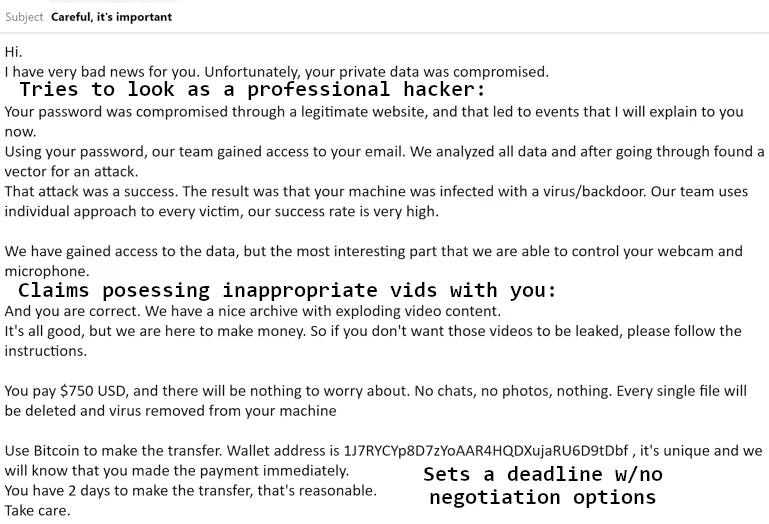
The sense of shock appears as the stranger says it has your nude photos. Moreover, this guy tries to pose as a “professional hacker”. They boasts of having access to all the browsing history, webcams, online wallets and the like. Why would they do nothing about this info – hijacking accounts, stealing all the money from online wallets? The question is rhetorical.
Urgency to the situation appears due to the “deadline” you should pay the ransom before. As the hacker says, any negotiations and stuff are not possible, and failing the payment date will end up with publishing all the materials. Some crooks also say things like “this is not my email so I will stop using it shortly after”. This creates even bigger concerns about the inability to avoid public shame.
Sure enough, the same methods may be used by someone whose threats are real. But they never follow the pattern, at least not that straightforward. This distinguishes a letter written by a real human from a tool of scammers, designed to fit any circumstances.
Check For A Re-Used Crypto Wallet
As sextortion scams are running in “waves”, you are most likely not the only person who got such an email. Frauds often stick to the exact same text, changing only the crypto wallet they ask to send the ransom to. A simple Google search of the wallet may reveal not just one, but several text patterns used in the same scam wave.
Obviously, when the con actor is real in its threats and is not running this as a business, it will never use someone else’s crypto wallet or the one used in a scam before. Even when a real hacker does something like this (such an occasion happens once in a while) it will never use the same wallet twice. Moreover, “real hackers” rarely opt for Bitcoin as a payment method, preferring cryptos like Monero or DarkCoin. The latter have the anonymizing infrastructure that is so heavily demanded when you are going outlaw.
AI-fueled Sextortion Scams Incoming
All in all, sextortion is a rather old scam that was not really effective over the last few years. People are aware about it, and there is almost no way this is real after all. This is true, but over the last few years, there is a huge risk of sextortion scams being resurfaced with a force yet unseen. Let me explain.

The current AI development is exciting. But what is more mind-boggling is the number of malignant implementations for this potential. In particular, we are talking about their photo editing capabilities. There are quite a few AI services even these days that will edit the clothing out of the picture of a person you’ve uploaded. Combine this ability with sextortion scams and the fact that most people share their normal photos without any doubt – and you receive fuel for a new, unpredictably powerful scam wave.
Scammers who stand behind sextortion emails will finally stop extorting money for nothing. This time, they may get not only a manipulative text, but things to prove their claims with. And, if you ignore the demand, they will post them somewhere. There’s still no reason to believe in their tails about access to all your accounts, but dumping the photos while tagging all your friends list may still be effective.
Sure, it is rather easy to prove the AI origin of images and videos. But the very fact of these images’ existence may throw people into panic. This will eventually force them to pay the ransom – which still does not guarantee that the scammer will not publish these fake photos. And even when you remain calm and ignore all the threats, it may be bothersome to prove that these nude photos of yours are just a hallucination of a vicious neural network.
How to protect yourself from email scams?
Well, that is not an easy question to answer. As I’ve just explained, things are getting complicated, and there is no well-rounded advice for the most modern cases. However, I took my time to think through the possible mitigation options for the majority of situations.
Control sharing your personal email address. While benign services try to keep their customers’ info private, there are enough services that do not care. Some shady forums, torrent tracking sites, websites with cracked software – they will gladly sell databases of their users’ emails to someone. Then, these databases are used to spam people and spread scams, including sextortion. Avoid leaving any personal info in such places, or at least do not use your personal email for authorization purposes.
Keep your head cold. A thing all extortionists rely on is your panic actions upon realization that someone may publish inappropriate graphic content with you online. You, in turn, should not do any emotional acts – that will save you both money and gray hair.
Change all your passwords. This is mostly for good measure, as only a few cases out of thousands of sextortion scams could really boast having your passwords leaked. Though, the very habit of updating your login credentials is a great enhancement to your personal cybersecurity.
Warn your friends, colleagues and relatives about a fake video. By announcing preventively that a provocative video can appear, you minimize the initial shock it may create. After that, all the fake video will do is call friendly laughs, avoiding shame or arguments. Even if the scammer is kidding and there is no graphic material in its possession, even a fake one, this will uplift the awareness of such cases.