TikTok has become a popular social network with over a billion registered users. According to statistics, each user spends about 95 minutes daily on this platform. Such an extensive social network is also susceptible to many different scams. Scammers found ways here to hurt users and lure them into their traps.
Who is being targeted by TikTok scams?
TikTok was founded in 2017, but scammers started using the platform shortly after its release. Many TikTok scammers create false accounts to cheat money, distribute malware on your device, or acquire confidential data for sale on the darknet. Some of their biggest target audiences are children under 14 years old. Privacy concerns are why parents believe social media is unsafe for kids.
Most common TikTok scams
TikTok is susceptible to many different types of fraudulent actions. These scams can be seen by the platform’s users, ranging from making easy money to false accounts offering true romance. Some scammers even claim to be famous or influential people. By knowing the methods of these scammers, you can avoid their devious techniques. Some of the most common TikTok scams are outlined below.
1. Easy money offers and fake giveaways
Criminals will often use the promise of easy money to lure victims into scamming schemes. These crooks will claim that large financial rewards are available for minimal effort on the victim’s part. Scammers may also claim that a famous person will randomly select someone to give away a large sum of money if they follow the scam’s instructions. Any offer that’s too good to be true is probably a scam. Confusing deals and agreements are standard among social media accounts. These agreements may contain scams that promise a lot of money or gift cards in exchange for liking, following, or sharing information. Although these scams are common on social media platforms, most of them are banned.
2. Duplicated celebrity and influencer accounts
Impersonators frequently copy the social media accounts of celebrities and influencers. Then, they use this content to increase their number of followers. They might even claim to give donations to charity, which is one of the scams they use to convince users. Additionally, they might try to convince users to invest in cryptocurrency – of course, by using the affiliate link that this celebrity offers.
If you see a suspicious celebrity account, look for red flags. This could be poor spelling, the account sending you a private message or an offer that seems too good to be true. If these accounts are fake, you won’t find any mention of them on the celebrity’s official website.
3. Bot accounts
TikTok, like other social networks, became the platform where bots numbers are galloping. The purpose of these bots is to distribute as much false information as possible and to send links to phishing sites through which they can get user data. Part of this information contains malicious content, which may be bad for users’ PCs and other devices.
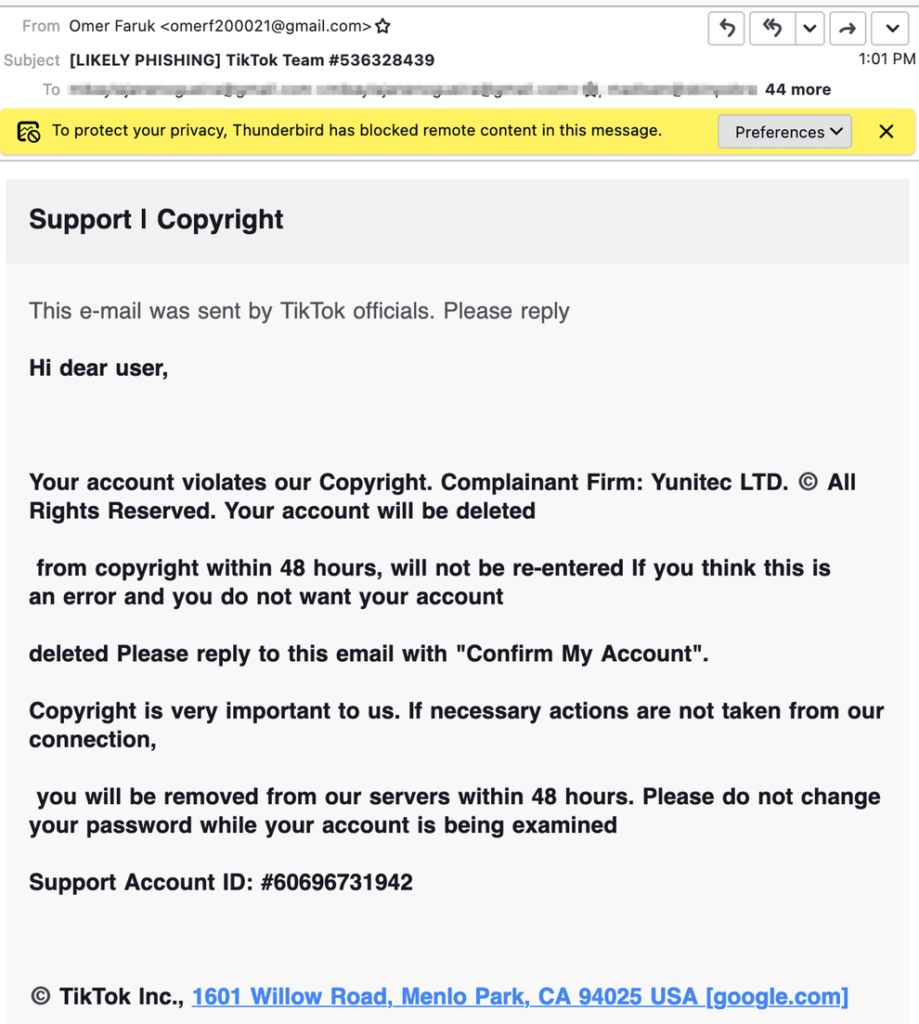
4. Phishing (the most common cyberattack)
Phishing is an easy way to handle confidential user data. They look completely harmless and casual at first sight. Phishing messages or comments convince users to click on a particular link or attachment. Generally, these are suggestions for increasing the number of subscribers or getting a verification badge.
Once a user opens such an attachment or link, they risk infecting their PC with malware. To steal an account, scammers can send a link to a server that will steal the authentication token. Another event option is to receive a request to enter your data to enter your account. If the user does not use two-factor authentication, hackers are even more likely to gain access to the victim’s sensitive data.
5. Promoted scam apps
TikTok has profiles that advertise and promote rogue apps. This is done to infect the user’s device with malicious content or to distribute spam. In addition, malicious applications can request payment for the installation. Therefore, it is best to read the reviews about these apps and check the ratings. If all this has a questionable response from other users, it is better to refrain from it.
6. Bogus products and services
Ever since the TikTok marketplace launched, users can sell their products. But there is one thing, the goods often do not correspond to the picture in advertising. Moreover, the seller can pay but not provide the goods. So be careful what you want to buy on social networks – all, exactly, not only TikTok. Also, check whether the TikTok profile is marked with a blue tick and whether it is verified.
Tips to stay safe on TikTok
TikTok is a platform where users can post their short videos, dial views, advertise their products, and other things. However the fraudster decided to use such platforms differently. The above points make us understand that you need to be more careful on the Internet. So, here is a list of the most necessary measures to be taken to avoid becoming another victim of scammers.
- Do not let all users send you emails. This way, you will protect yourself from phishing emails, unwanted ads, and other redundant information.
- Do not click on unfamiliar links and attachments. Such attachments may carry malicious content. They may also request your confidential information and then sell it to third parties or use it for other malicious acts.
- Use two-factor authentication. This will reduce the chances of hackers successfully hacking your accounts because 2FA requires a double check on who logs in.
- Use reliable protection from GridinSoft-AntiMalware, which will protect you from spyware, adware, trojans, and malware. Thus, if the fraudster can convince you to click on malicious links or anything else, GridinSoft-AntiMalware will prevent it from getting on your device.
Sooo this person is saying that if I buy a 10 dollar apple gift card that they will send money is it true or false