Threat actors started using compromised websites for phishing purposes much more frequently. Such worrying statistics popped up in several recent researches. This is not a brand new approach, though it may be particularly effective for fraudulent purposes.
Hackers Use Poorly-protected Sites in Phishing Scams
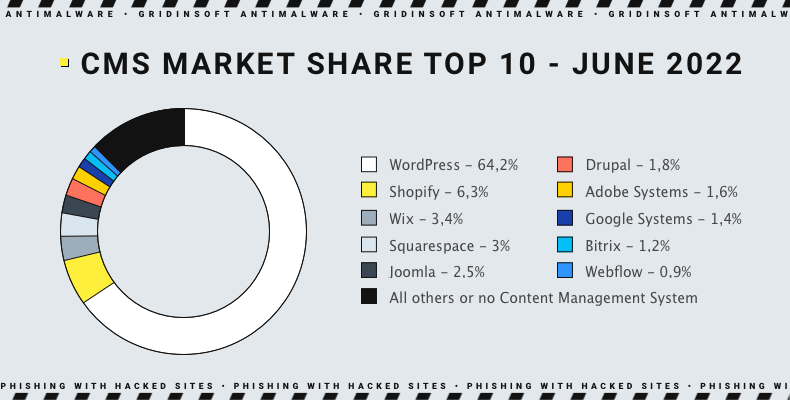
Cybercriminals often target abandoned WordPress websites with poor maintenance and security patches, making even smaller sites attractive targets for long-lasting phishing pages.
Malicious actors can still target actively maintained websites, even though they are kept up to date. Websites with low traffic and smaller audiences are also vulnerable to hacking attempts. Some website owners might need more financial resources to invest in robust information security measures or hire dedicated security professionals. They could also have limited knowledge about security configurations, or they might wrongly assume that their small website wouldn’t attract hackers’ attention. However, for phishers, the potential to exploit a website is more significant than its popularity. This is because they can use compromised sites to distribute links to scam pages through emails or instant messaging platforms, regardless of size. Consequently, even smaller websites present an appealing opportunity for scammers.
According to researchers, most websites on the Internet are powered by the WordPress content management system. This platform boasts an extensive array of third-party plugins aimed at enhancing its functionality. Unfortunately, both plugins and WordPress are frequently found to have new vulnerabilities that hackers can exploit.
WordPress-Based Websites In The Scope
Phishers exploit security holes to hack WordPress websites. After a successful exploitation attempt, they upload a WSO web shell, which allows them to bypass the authentication step and gain access to the website control panel. This gives them full control over the website.
Nevertheless, the majority of compromised websites exhibit broken links leading to various sections of their homepage. This arises because hackers often remove the original directories and substitute them with phishing materials. When users input data, like website credentials or even sensitive information like CVV numbers from bank cards, depending on the specific scam, this data gets stored within the control panel of the deceptive page. In cases where the website is equipped with a web shell and its content is accessible to anyone, the victim’s data becomes readily visible to all.
Signs of a hacked WordPress site
Several fairly obvious signs suggest you are looking at a phishing page hosted on a compromised website.
- The URLs of these pages encompass folders such as
/wp-Config/, /wp-content/, /wp-admin/, /wp-includes/, or equivalents, and within these directories exists a PHP file. Although web pages with the.phpextension can be legitimate components of websites, their presence in conjunction with the aforementioned directory names unequivocally indicates a phishing endeavor. - The content displayed on the homepage seems disconnected from the phishing page.
- The URL includes the service’s accurate (or altered) name that the scammers aim to mimic. However, this name is unrelated to the actual name of the website.
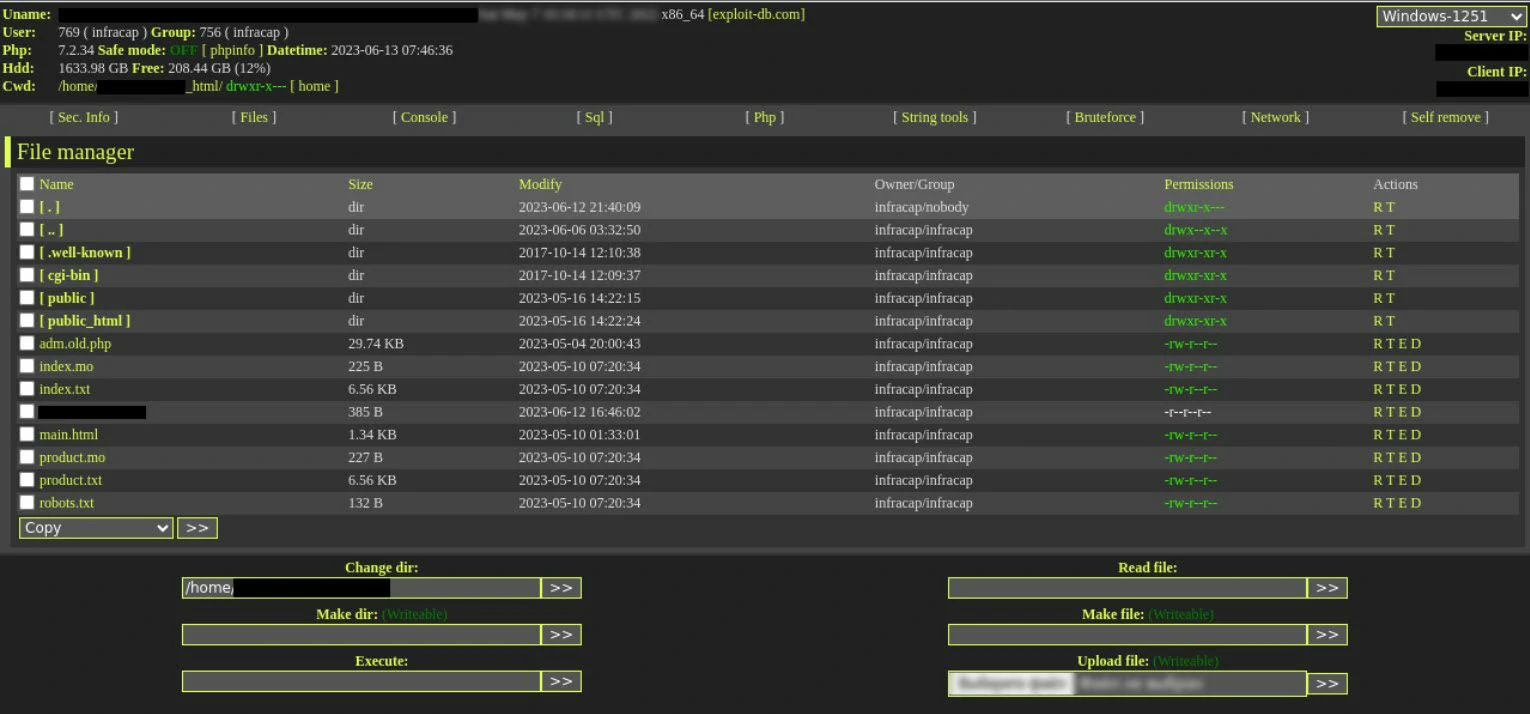
How to recognize phishing with hacked sites
Despite hackers’ diligent efforts to fabricate convincing replicas of popular websites that their targeted users frequent, there are telltale signs of phishing on a hacked site. It’s particularly important to be vigilant for the following indicators:
- The presence of default names of WordPress directories in the URL.
- Inclusion of the imitated brand’s name within one of the directory names.
- Page content that appears unrelated to the website’s overall theme.
How to protect yourself against phishing attacks?
Most phishing cases are conducted mostly thanks to the victim’s inattentiveness. Hence, you may suppose an easy solution – being attentive at each questionable moment. You can find a lot of things spoofed, and with the special tools that are available nowadays, this form of fraud is very easy to perform.
- Use two-factor authentication. That won’t let anyone except the one who has your mobile phone (hopefully, yourself) log into your account. However, your phone might have yet another authentication procedure to unblock it, which would make the authentication to your account multi-factor, which is even better for tackling the consequences of a successful phishing attack.
- Should you fall victim to a phishing attack, better have all your valuable data backed up on a hard drive or cloud storage. Phishing attacks may have various consequences, but data protection is the most maintainable countermeasure.
- Protecting your personal information is crucial for maintaining your privacy and security. Think twice before sharing personal information in casual conversations, both online and offline. Avoid posting sensitive details like your full address, phone number, and financial information.
- Use a spam filter. With spam filters and anti-spam features, it’s possible to stop receiving unwanted emails. Opt into text lists that allow you to unsubscribe from future messages. This will help minimize the damage from phishing.
- Ultimate counteraction method for any form of phishing on the computer is anti-malware software. Of course, it is important to note that not each security tool will fit you – programs with an online protection function guarantee the best protection. GridinSoft Anti-Malware may offer you such a function. Moreover, it is also able to get rid of the virus that helps the fraudsters to fool you.