Trend Micro warns that since March 2021, the TeamTNT mining botnet from the same-named group has successfully compromised more than 50,000 systems.
The TeamTNT group has been active since at least April 2020 and started with attacks on incorrectly configured Docker installations, infecting them with miners and bots for DDoS attacks.
Then it became known that the hackers slightly changed their tactics: they began to attack Kubernetes, and also began to search for credentials from Amazon Web Services on the infected servers and steal them.
In addition, there have now been recorded cases of hackers posting malicious images to the Docker Hub, and researchers have discovered that the group is using the Weave Scope tool in their attacks, designed to visualize and monitor cloud infrastructure.
It is also known that TeamTNT comes with a worm component that turns every infected server into a new botnet host and forces it to scan the network for new potential victims; steals SSH credentials and can be used for DDoS attacks (although this feature has not yet been used by hackers).
As a result, grouping is one of the main threats to cloud environments today.
The rich functionality is now paying off for TeamTNT authors, Trend Micro now reports. As mentioned above, according to analysts’ estimates, in just three months, mining malware successfully compromised more than 50,000 systems.
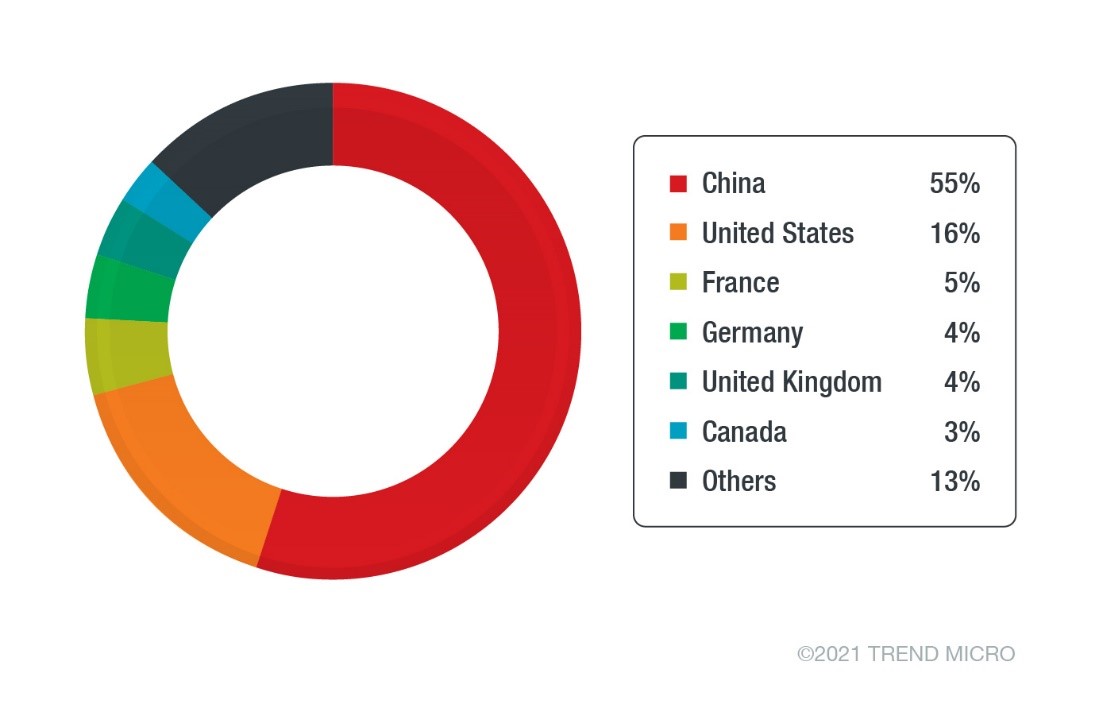
Most of the victims are systems hosted by Chinese cloud providers. This data correlates well with the statistics of the Lacework company, published in early 2021.
Let me remind you that I also talked about the fact that Microsoft warns of the growing number of cyberattacks using web shells.