Trojan:Win32/Pomal!rfn is a detection commonly encountered when downloading programs like emulators or games. This detection, shown by Microsoft Defender, often sparks concerns about whether the threat is real or a false positive. Let’s break it down to understand its nature, potential risks, and the steps to remove it effectively.
What is Trojan:Win32/Pomal!rfn?
Trojan:Win32/Pomal!rfn is a type of detection flagged by Microsoft Defender that generally indicates the presence of an info-stealer. This kind of malware is designed to operate covertly, stealing sensitive information such as login credentials, cryptocurrency wallet keys, or other personal data.
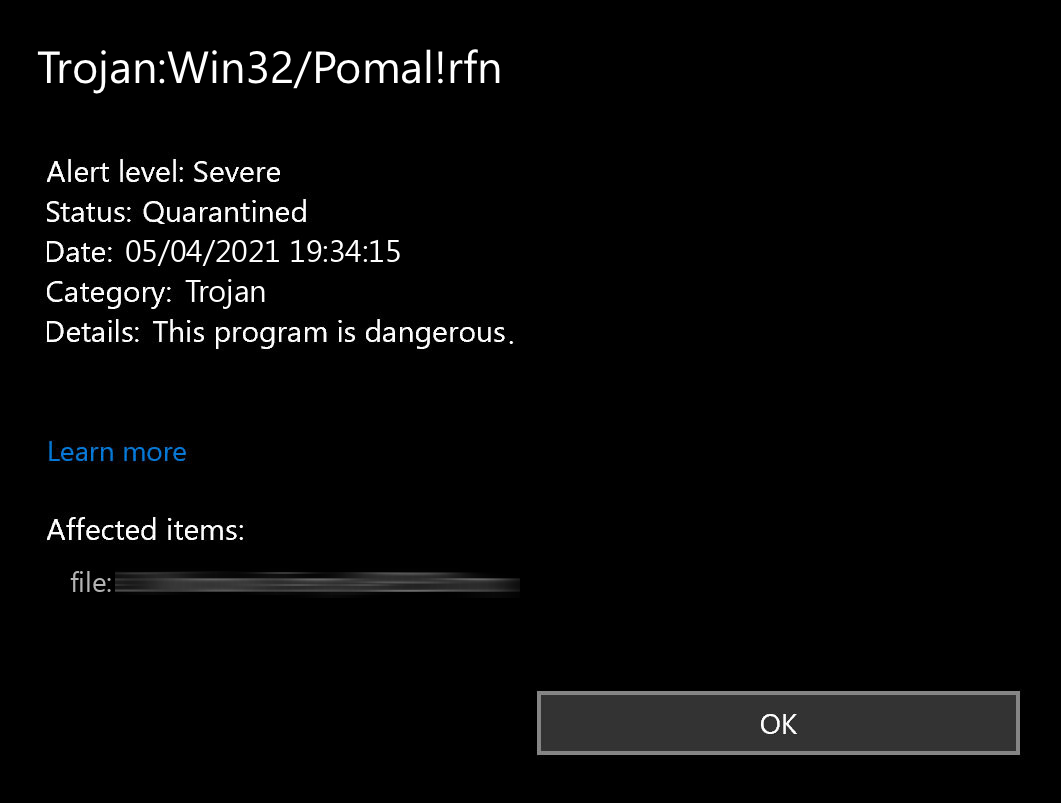
Once installed, Trojan:Win32/Pomal!rfn may create registry entries, schedule tasks, or modify system settings to ensure it starts automatically when the system boots. This persistence allows it to remain active and continue stealing information over time. Although it typically operates covertly, users might notice unusual behavior, such as slower system performance, consol windows chaotically blinking, or unauthorized activity in their accounts.
Is it a False Positive?
As I’ve mentioned before, Trojan:Win32/Pomal!rfn can sometimes be a false positive. This occurs because the detection is heuristic, relying on behavior rather than signatures. Quite a few users have reported that Defender flagged game files as Trojan:Win32/Pomal!rfn after installing updates from Steam. A similar case was discussed on Reddit, where a program hosted on GitHub was repeatedly detected as a threat after each update.
More examples of false detections include programs like Roin Simulator, TheoTown, and certain network utilities. Seeing them detected is much more likely to be a false detection, and one should react appropriately.
If the detection is valid, Trojan:Win32/Pomal!rfn can operate in the background without showing any visible signs. That is why thinking the infection is non-existent after seeing no visible symptoms may end badly. Victims typically notice the consequences later, with spam emails being sent from their accounts, unauthorized access to online accounts, or cryptocurrency funds being stolen.
Detection Explained
The name “Trojan:Win32/Pomal!rfn” is structured to provide specific information about the detected threat, and each part has its own meaning: Trojan indicates the generic type of malware. A “Trojan” is a malicious program that disguises itself as legitimate software to trick users into installing or running it.
Win32 specifies the platform or operating system targeted by the malware. In this case, “Win32” refers to 32-bit versions of the Windows operating system. Although, it can also affect 64-bit systems due to compatibility.
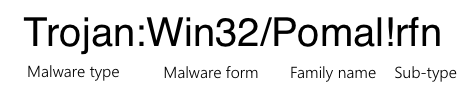
“Pomal” is also a generic identifier assigned by Microsoft’s security team. It acts as a label for a group of malware samples that share similar characteristics. The name itself does not carry specific meaning about the malware’s behavior but helps categorize it within Microsoft’s threat database.
“!rfn” indicates that the detection is based on heuristic analysis. This part signals that the detection might not be tied to a specific, known malware signature but rather to suspicious activity or attributes.
How did I get infected?
Trojan:Win32/Pomal!rfn typically spreads through unsafe downloads, particularly from unverified or unofficial sources. This includes cracked software, pirated games, and emulator programs that users obtain from unreliable websites or file-sharing platforms. Cybercriminals often bundle the malware with legitimate-looking applications to trick users into installing it.
It can also spread through malicious email attachments, links in phishing emails, or compromised websites that exploit vulnerabilities in outdated software. In some cases, Trojan:Win32/Pomal!rfn may also be distributed through fake updates or installers, which appear genuine but contain hidden malicious code. These methods rely on user interaction, so the key to preventing the infection is following safe browsing practices and sourcing software only from reputable sources.
How to Remove Trojan:Win32/Pomal!rfn?
If you’re unsure whether this detection is a false positive, using a third-party anti-malware solution is the best approach. Consider using GridinSoft Anti-Malware as an additional tool to gain a clearer understanding of the situation. Download it by clicking the banner below and run a Full scan, that will check the entire system, down to the most remote files and folders.