First-tl pop-up ads are malicious push notifications (like a Sec-tl sites) that parasite legitimate browser functionality. Fraudulent actors that stand behind this chain of websites earn money by showing hundreds of ads in such a way. And those are not just regular ads: it is common to see scams and phishing sites among them. Let me explain how this scam works, and how you can stop it from happening and avoid such troubles in the future.
First-tl Pop-Up Notifications Overview
Push notifications from First-tl series of websites is a fraudulent campaign that aims at earning money through pay-per-view ads. Con actors who stand behind it set these sites to send dozens of notifications each minute, each containing some promotion. It works by abusing legitimate browser functionality of push notifications, and the user is tricked into allowing these sites.
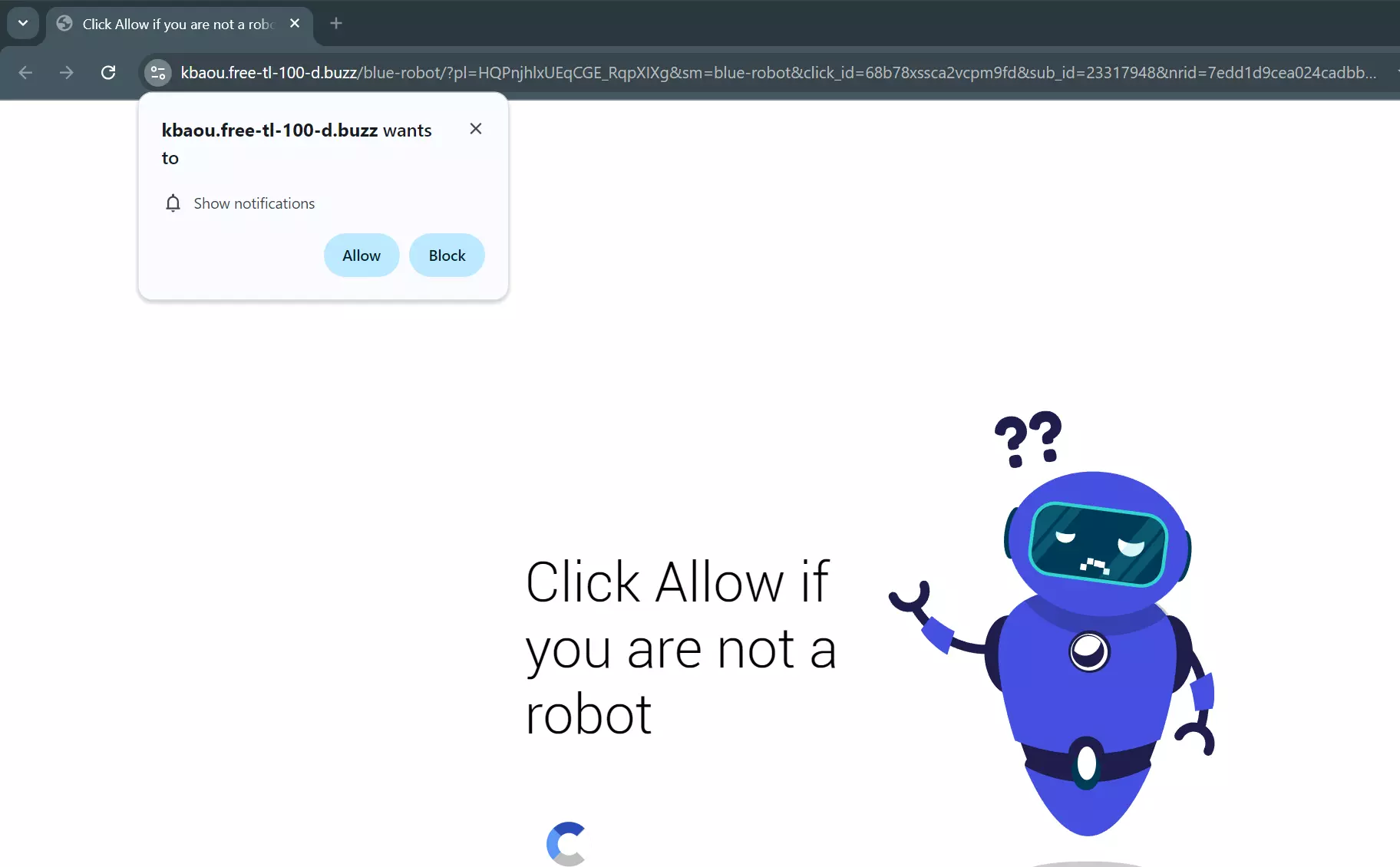
Typically, when users get to any of First-tl sites, they see a demand “to prove that you are not a robot”. To do this, the site asks to enable notifications. This, eventually, is where it all starts. You can open such a page literally dozens of times, and that will have no impact on you or your system unless you press the “Allow” button.
Domains involved in the scam
| URL | Registered | Scan report |
|---|---|---|
| First-tl-209-a.buzz | 2024-09-21 | 209-a |
| First-tl-209-b.buzz | 2024-09-21 | 209-b |
| First-tl-209-c.buzz | 2024-09-21 | 209-c |
| First-tl-259-a.buzz | 2024-09-26 | 259-a |
| First-tl-259-b.buzz | 2024-09-26 | 259-b |
| First-tl-259-c.buzz | 2024-09-26 | 259-c |
| First-tl-259-d.buzz | 2024-09-26 | 259-d |
| First-tl-259-e.buzz | 2024-09-26 | 259-e |
| First-tl-139-f.buzz | 2024-09-12 | Report |
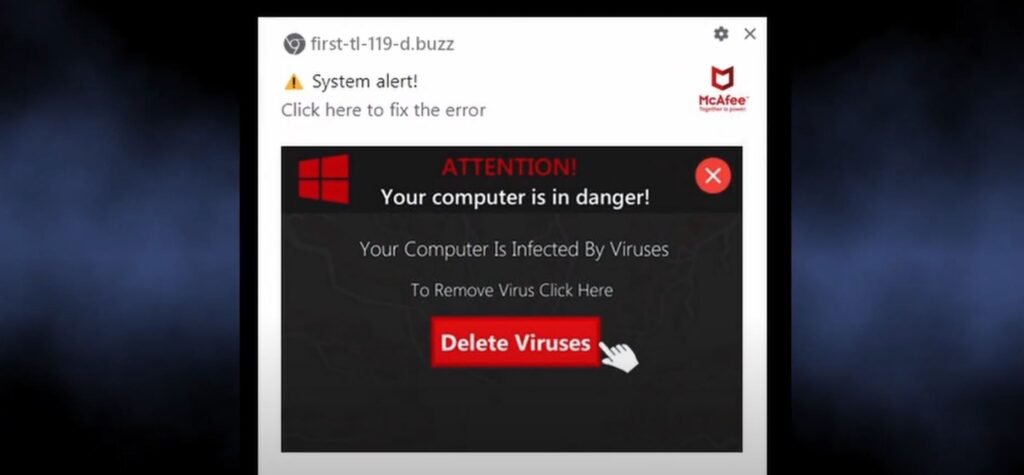
But let’s get one step backwards, to the way one can get to these websites. Similar to quite a few other similar scam campaigns, these sites gain visitors through redirections from other sites. I am not talking about regular external links – no, frauds rely on random redirects that happen as you click on any website element.
As far as my research shows, First-tl sites mainly get redirects from sites that offer pirated movies and TV series. In particular, there are two sites to stay away from – moviesnation[.]org and moviesearch[.]org.
By just going to the root domain, you will see either a 404 error or a hosting boilerplate message saying that the domain is for sale. All the fraudulent activity happens on a much deeper level, with several URL parameters generated during the redirect. And, as you can see from the list above, frauds use quite a few domains, meaning that each can target different countries or show different ads in notifications.
Are First-tl Push Notifications Dangerous?
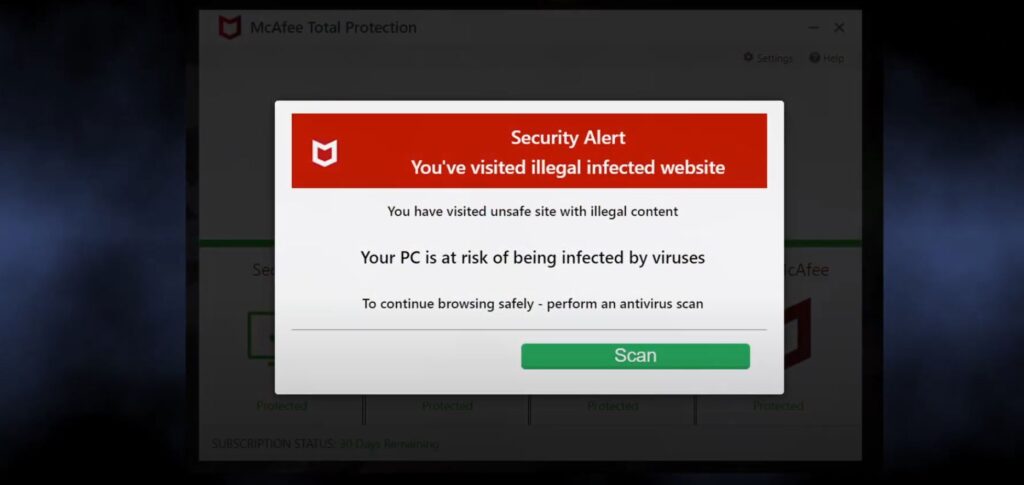
Yes, they are. Aside from being just annoying, as any excessive advertising is, their contents are not filtered in any way. What’s more, scammers apparently cooperate with other frauds in that matter, so quite a lot of push notifications lead to a downloading page of some sketchy software, a shopping scam site, or else. There can also be promotions of gambling or betting sites, or low-trust dating platforms. All of the latter pose less danger than phishing or scams but can create headaches nonetheless.
It is also worth saying that these pop-ups pose no threat unless you click them, and consequently interact with the contents of the site. And it is tricky at times: images in notifications can contain a “cross”, suggesting you to click it to close the ad. Instead, as you had in fact clicked the main content of this promotion, this will throw you to a promoted website.
As for direct dangers for the system, they are not too high unless you have interacted with the ads. However, there are a lot of cases when an active adware was opening such notification spam pages, so the user should not even go to some dodgy websites to trigger a redirect. That’s why an anti-malware scan is a recommended step even after the manual removal of the pop-ups.
How to remove First-tl pop-up spam?
Since the main source of pop-ups is the permission to send notifications for a certain website, it is possible to remove it manually. To do this, go to your browser settings and type “Notification settings” in the search bar. I will show this on the example of Google Chrome, but the steps should be similar for the rest of browsers.
Then, it is time for the second step – anti-malware scan. As I said, there is a risk of unwanted pop-ups appearing as the result of adware activity. Removing it manually is a much, much more complicated task than removing permissions for notifications, so an automated scan will be more convenient. For this purpose, I recommend GridinSoft Anti-Malware.
First-tl Removal Guide

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.
