The Cybercrime world changes rapidly – both by expanding, collapsing, and evolving extensively and intensively. One of the most massive malware types in the modern threat landscape – Infostealer Malware – appears to enter a new stage of development. Though its major names remain the same, some new malware families with promising features popped out. Let’s have a peek at all of them and see what to expect.
Infostealer Malware Market in 2024
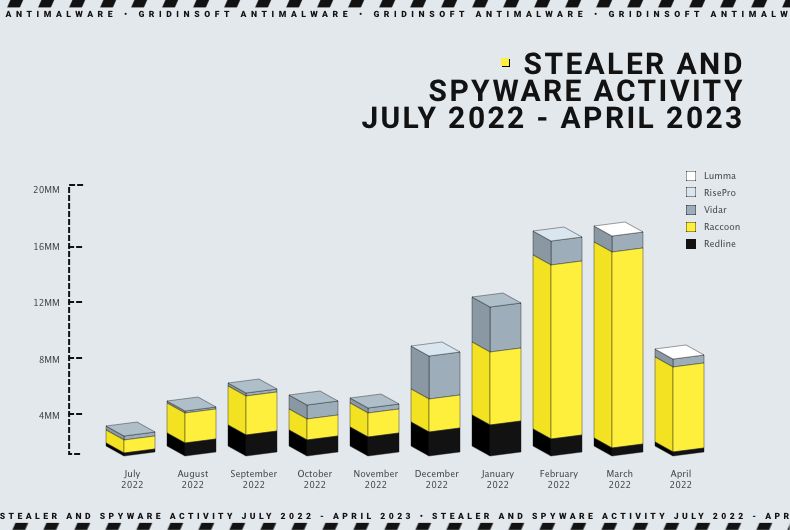
Infostealer malware gained more and more popularity during the last decade. However, the biggest spike happened during the last few years. The first noticeable factor is the massive popularisation of cryptocurrencies. How is that related? Well, relatively big amounts of money always attracted the attention of hackers. Carding and banking fraud though is now less effective as banks implemented strict controlling measures back in the early ‘10s. Cryptocurrency wallets, on the other hand, have low to no control, making them ideal targets for Infostealer.
Another reason that made spyware and infostealers so popular and widespread is their massive application in attacks on corporations. Even when hackers break into the network to cipher the files and ask for a ransom for their decryption, they also drop an Infostealer malware that will exfiltrate as much valuable information as possible. Afterwards, hackers request an additional ransom to keep this data secret. Some attacks are based exclusively on stealers, and the result of their job is both sold on the Darknet or used for business email compromise (BEC) attacks. Additionally, some ransomware groups that aim at home users started adding spyware to their attack chain a while ago.
Infostealer Malware Market Leaders
As of May 2024, 3 major malware families dominate the market – RedLine, Raccoon, and Vidar. All of them are not new at that point of time, with Vidar being active for the longest time. Let’s have a closer look at them, starting with the youngest one.
RedLine Infostealer
RedLine infostealer appeared in 2020, and saw a pretty wide application in different cyberattacks. Most of the time, however, it was aimed against single users, as its functionality fits best for this purpose. Key targets for the RedLine are cryptocurrency wallet data, both from desktop versions and browser plugins. Still, it can gather other data, like FTP/VPN configurations and session tokens for apps like Discord or Steam. Having a pretty large market share at the edge of 2024, it became much less active starting from March 2024. Yet an enormous number of new samples that popped out recently may be the sign of another campaign getting ready. The RedLine developers find hackers who buy this malware is through Telegram groups and Darknet forums.
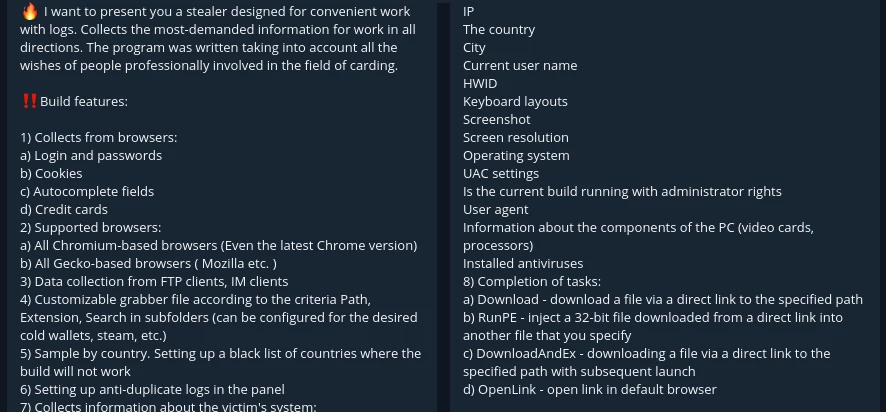
Raccoon Infostealer
Raccoon has key properties similar to ones RedLine offers, but is capable of capturing a much wider selection of data. In its scope are browser autofill files, cookies, and online banking credentials, on top of the ability to pluck cryptocurrency wallets. Since the emergence in early 2019, Raccoon was holding dominant positions on the market – and keeps holding them even now. In the summer 2022, its developers released a new version, promising faster and more reliable malware for a slightly bigger pay. Same as RedLine, Raccoon stealer is commonly spread through ads in Telegram channels and bots; Darknet platforms are less preferred, though are used for public communication.
Vidar Infostealer
Among top 3 Infostealer threats, Vidar is most definitely a dark horse. It is considered to be an offspring of Arkei stealer, malware that made quite an image back in early 10’s. After the launch in 2018, it never had a dominant share on the market, being at best #2. Nonetheless, its efficiency and unique design is hard to deny – Vidar offers a modular approach towards data stealing and has an uncommon way of C2 communication. It also performs self-destruction after the successful data exfiltration. Additionally, it is often spread in a bundle with other malware, such as STOP/Djvu ransomware. Methods of selling it to cybercriminals, however, are less unique – it uses Telegram channels dedicated to malware promotion.
Newbies
It would be quite reckless to deny the importance of new malware. For sure, not all of them will make it even to the 1-year milestone, but Raccoon and Vidar once were newbies as well – and you can see where they are. Among stealer families that popped out over the last year, there are a couple you should keep in mind.
Lumma
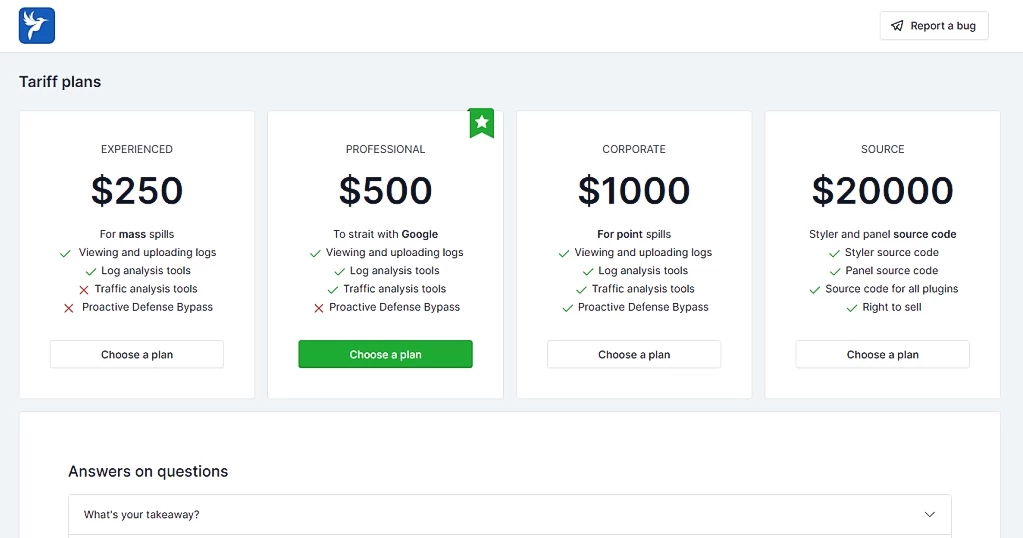
Also known as LummaC2, this infostealer appeared in December 2022. At the outset of familiarity with this malware, you can already see some fairly noteworthy details. At the “pricing plans” panel, developers mention the ability to configure the payload in a specific manner, and add network sniffer functionality. The presence of these functions depends on the price of the chosen plan – $250, $500 or $1,000. Additionally, masters offer access to malware and panel source codes and the right to sell them – for $20,000. Other functions, however, are available regardless of the plan. Lumma can grab browser cookies, autofill forms, data from 2FA plugins/apps, and crypto wallets credentials – from both apps and browser plugins.
Stealc
Stealc is another youngster, which was first mentioned on January 9, 2023, on several Darknet forums. It appears to utilise best practices from most popular stealers, which already makes it pretty potent. Among unusual practices is a free test and weekly releases of new features. As for other functions, malware has a classic set of a modern infostealer: it gathers data from web browsers (cookies, autofill forms etc), cryptocurrency wallets extensions and even email clients and messengers. Such extended functionality, especially compared to other new malware examples, will definitely be appreciated.
How to Protect Against Infostealer Malware?
Protection against threats like infostealer is always a tough question to answer. Thing is, malware like this is forced to evolve constantly, finding new ways to be more efficient and stealthy. This makes any advice that reacts to some malware features useless in the long-term. However, there are still some things Infostealer Malware developers can’t (or don’t want to) change.
Beware of spear phishing. It may have different forms – from email messages that are sent from a compromised business email to posts in social media from the hijacked account of a legit company. But even after all the sophistications, hackers can never make a check-proof legend. Most commonly, they attract victims by urgent events or exclusive deals. A simple source check will reveal any possible scam – if the impersonated company has nothing to do with such claims, ignore the spooking message.
Avoid using pirated software. Despite losing a significant portion of market share due to email spam expansion, software cracks are still used for malware spreading. Torrent-trackers and third party websites are flooded with numerous offers on a brand new software – and try to guess which one is infected. Using only licensed software will not make you clear before the law, but also nail any risk of malware injection. And, believe me – dealing with malware activity consequences will cost you way more than you can save on program licences.
Protect your system with proper anti-malware software. Yes, it is better to avoid muddy waters at all, but having a security tool that will take care of problems will make your life much easier. Not any utility will fit though, as infostealer malware have some tricks to avoid basic anti-malware software. GridinSoft Anti-Malware gives them no chances, thanks to its three-component detection system and constant updates that retain its databases’ relevance.