Taskbarify is unwanted software (like a Movidown)that claims it is a tiny little Windows tweaker. However, it also turns the device into a proxy server without the user’s knowledge. Let me show you what is so dangerous about this utility, and how to remove it.
What is Taskbarify?
Taskbarify is a Windows utility classified as a Potentially Unwanted Application (PUA). As for functionality, officially, this program has one function – changing the appearance of the taskbar. Taskbarify has an “official” website, but most users acquire it unintentionally. The main sources of this app on users’ systems are bundling it with pirated software or displaying it through suspicious banners. This creates one more risk: the appearance of this app may be a sign of numerous other unwanted apps running in the background.
The main reason for Taskbarify categorization as an unwanted program is its proxyware module. In other words, it can use the bandwidth of the victim’s Internet connection to provide proxy server services. This enables the app to intercept network requests, potentially compromising privacy and security. Together with the complicated uninstallation ways, , this all creates a halo of ill fame around the program.
Why is Taskbarify unwanted?
Let’s take a closer look at how this thing works. The official website claims the app is clean as a tear, has no hidden functions, and does not load the system.
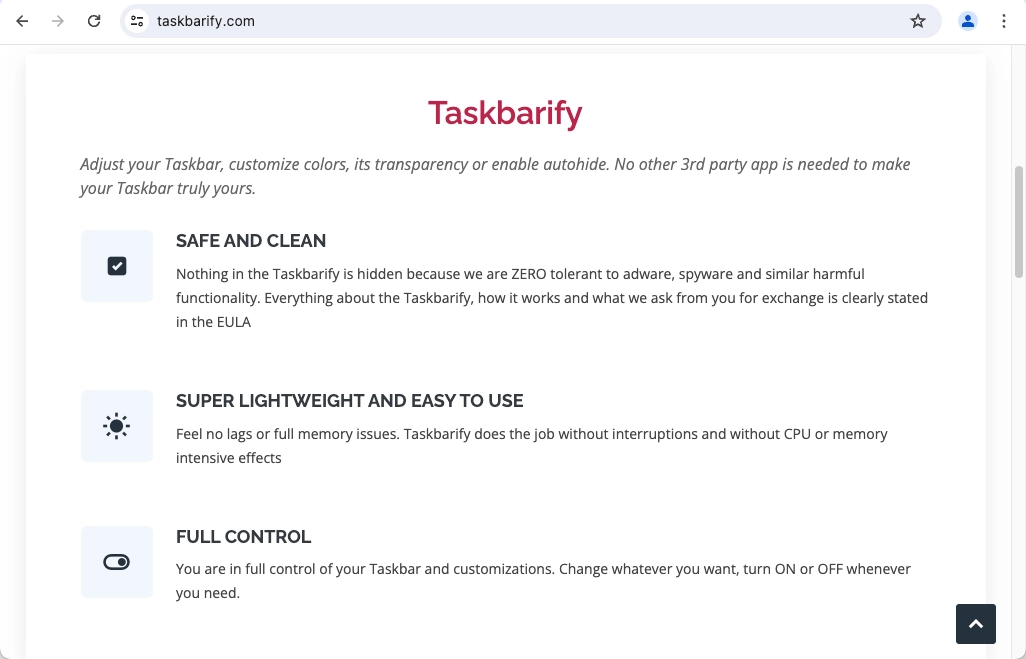
However, the license agreement says otherwise. The text states that the program can be a proxy and use your device’s resources, under the said Globalhop SDK. Moreover, this SDK is included in the application installation by default without explicitly disclosing its usage and impacts on the user’s system on a separate prompt.
The functionality of the exact app is… questionable. Visually, Taskbarify adds transparency to the taskbar, which enhances its look, but that’s it. Promised “spyware uncovering” or “full control” are pretty hard to witness, to be honest. Also, the built-in description (see the screenshots below) lies about the program being available in all regions: by setting the VPN region to Moldova, I’ve managed to make it return a “something went wrong” error.
Suspicious Behavior
The first problem is that the app does not obtain user consent on using traffic. The latter reduces the consumer’s security posture caused by sharing internet resources. Taskbarify reads system certificate settings, security settings of web browsers, and Windows trust settings. The app does not display explicit notification about the potential risks in security posture related to sharing network connection when the app is installed.
Aside from the privacy risks associated with proxyware, the activity of such a module itself may cause issues with bandwidth and system performance. For weak devices, a constant traffic flow may take quite a bit of CPU time, leading to the rest of the applications being laggy and unresponsive. Also, the sheer volume of traffic used by proxyware can turn into significant financial losses for the users of metered connections.
Impossible to Close
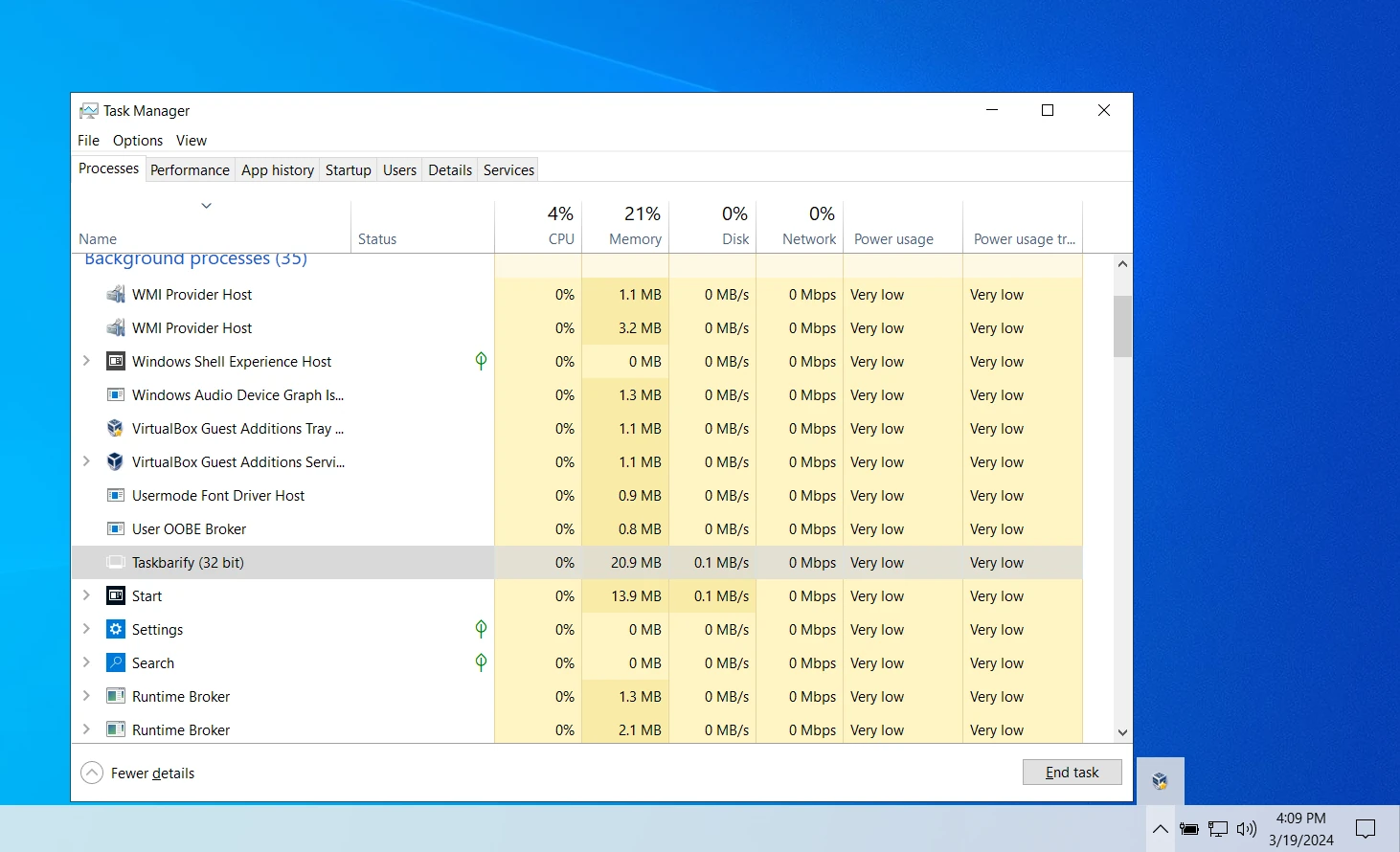
Another red flag is the pseudo-closing of an application. If the user finds the application icon in the tray, right-clicking it, and selects “Quit”, the application will disappear. However, by opening the Task Manager , you can see it running in the background without the tray shortcut. This means the application can cease modifying the taskbar’s “core functionality” but continue running as a proxy server in the background.
Difficulties With Removal
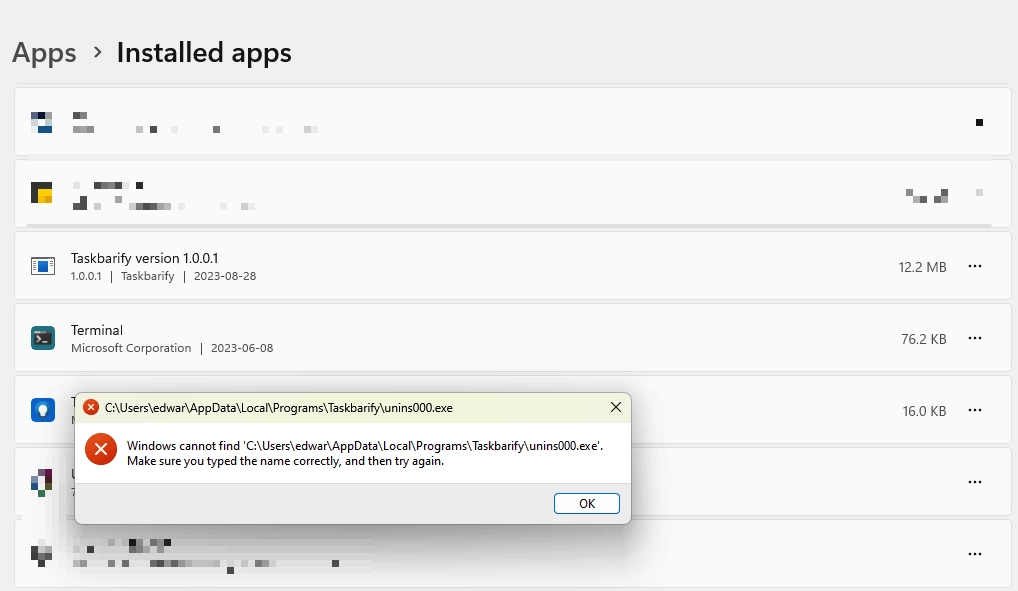
Unlike most programs usually installed at “C:\Program Files\”, Taskbarify’s default installation folder is “%AppData%\Local\Programs\”. Since this directory is hidden by default, it virtually eliminates manual removal by the average PC user. Moreover, some users are having trouble uninstalling Taskbarify with the built-in uninstaller, which indicates that the application is trying to avoid removal or recover the app.
How To Remove Taskbarify?
It is possible to uninstall Taskbarify manually, but tricky installers may cause problems and revert the uninstallation. Also, as I’ve mentioned in the introduction, this app often comes as a part of a software bundle, and is installed along with numerous other unwanted programs. To get rid of all this in just a couple of clicks, I recommend using GridinSoft Anti-Malware.
A Standard scan will be enough. GridinSoft program will check the entirety of the system volume – this is where all the unwanted programs typically reside. Give it time to finish, and your system will be as good as new.