Fake Windows Update became a malware spreading way once again. Updates are a pretty routine part of the Windows user experience. Over the last 7 years, Windows users mostly used to see the familiar update icon in the tray. Inexperienced people, however, do not know the mechanics of Windows update, and can be trapped with the disguise of a “legitimate” and “trusted” update. Crooks who spread Aurora spyware seemingly opted for that approach in spreading their malware.
Fake Windows Updates in Browser – What is That About?
Even the most novice Windows users have likely seen the Update section of Settings in Windows at least once. There all updates, including ones for Microsoft Defender, are displayed. This is the only place users can observe and control the patches installation, without any exception. The latter, however, is not that obvious, and hackers use it for their good.
Actually, that is not the first case when the topic of Windows Update is exploited. Since the release of Windows 10, when Microsoft started to offer the updates to their new OS in a pretty obsessive manner, numerous campaigns impersonating the infamous system notifications popped up. Users were tricked into clicking the “install button” that triggered the malware installation. Current case is almost the same, yet different in possible consequences.
Most often, tricks like fake Windows update banners/pages were aiming at installing malicious browser plugins, adware or unwanted programs. These three are unpleasant, yet not critical. In the case of the most recent campaign, victims receive Aurora stealer – a threat of a completely different grade.
What is an Aurora Stealer?
Aurora is a novice example of infostealer, emerging in early autumn 2022. First spreading way it used was noteworthy as well – malware exploited ads in Google Search to propagate itself. At that time, the campaign of malvertising in Google Ads was unexpected, and Aurora had a great start.
Itself, this malware appears to have some features that are worth having a peek. Immediately after the execution, Aurora checks not for the “classic” VM presence, but for the WINE environment. This toolkit for Linux allows to run most Windows programs, even when they are not ported to the *NIX platform in a proper way. Malware analysts appreciate WINE because of the ability to observe the malware behaviour and absence of any counteraction from malware – contrary to virtual machines and debugging tools.
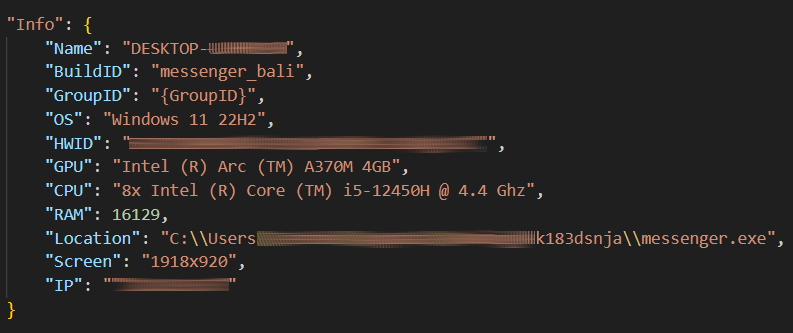
When it comes to functionality, Aurora appears to be a classic example of infostealer that aims at in-browser data, session tokens, and crypto wallets as a desktop app and browser extensions. First of all, it gathers a small blob of system information to fingerprint it. System name, username, HWID, CPU, RAM, GPU, screen resolution and malware file location are accompanied by two sample-specific values (buildID and groupID) and are sent to the C2 server.
Data stealing
After the initial fingerprint, malware checks web browser files to locate SQLite databases with cookies, search history and login data. Having that done, it starts seeking for crypto wallets extensions by their extension ID. Overall, there are 100+ extensions it searches for. Furthermore, it starts checking the AppData/Roaming folder to see if there are any desktop crypto wallet apps. If ones are present, malware gathers the data from databases these wallets use to store credentials in.
Once Aurora is done with cryptowallets and stuff, it switches to session tokens and credentials for several popular applications. In particular, it aims for Steam and Discord – stealing their session token allows them to take over the user session. Telegram treats the user in a different way, thus malware simply tries to extract all the session-related data available. With FTP access utilities, malware works in a manner similar to web browser contents – it extracts sensitive data from databases located in the program folder.
Unusual Details
Extensive stealer capabilities are threatening, though not the most interesting detail of Aurora malware. First of all, the spreading campaign appears to be related to a row of URLs exploited to display the malignant banner. Some of them belong to the Russian domain name pool, and some contain obscene phrases in Russian in URLs.
pochelvpizdy[.]ru
evatds[.]ru
click7adilla[.]ru
oled8kultra[.]site
activessd6[.]ru
activedebian[.]ru
grhfgetraeg6yrt[.]site
moskovpizda[.]ru
oled8kultra[.]ru
xhamster-18[.]ru
shluhapizdec[.]ru
04042023[.]ru
clickaineasdfer[.]ru
chistauyavoda[.]ru
xxxxxxxxxxxxxxx[.]ru
Once the victim opens the site, it shows the banner that states about Windows Update and plays animation. Then, it asks to finish the update setup “by installing the critical Security Update” – a file downloaded when the “update” is at 95%. The request to update a third-party browser to finish the Windows patch sounds goofy, but for inexperienced users it may look normal. In fact, the “update” is an InvalidPrinter loader that acts as a precursor to Aurora. Though, it is not obliged to deliver only this one – other malware strains may appear as well.
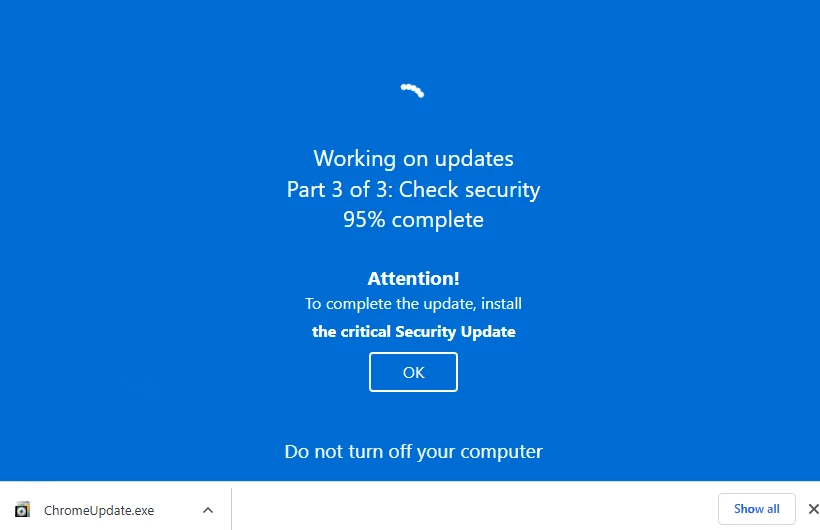
How Did Fake Windows Update Page Appear?
Obviously, most of the users who witnessed or even fell victim to that scam will never visit these sites on their own. Moreover, they will likely fail to access them manually – they simply do not respond. That happens because such websites wait for the clients from adware – the specific kind of malware that shows unwanted and malicious promotions to its victims. This virus changes networking properties of a system, forcing it to connect to the mentioned site through a specific port.
Even away from the fake Windows update, adware is a pretty unpleasant thing. Showing spam-like ads is distracting and annoying, but when these promotions contain malicious content, things become dangerous. The case I described above is a perfect depiction. Additionally, adware-related banners commonly contain phishing links or downloading pages of unwanted programs. If you see the fake Windows update page, you’d likely see other signs of malware.
How to protect yourself?
The advice for counteracting fake Windows update pages, and particularly adware that causes it, consists of preventive and reactive measures.
To avoid being infected with adware, the best option is to avoid any dubious software sources. They always were and remain a widely used source of malware. Crooks add malware into the bundle with the initial app, or even spread one instead of the promised software. Using unlicensed software is illegal, and, as you can see, may end up with a chain of really bad consequences.
Use a proper security tool. Adware may be quite tricky to find and remove, especially one that masks as a legit app. Malware that can arrive during its activity is even more tough. For that reason, a really complex and high-quality solution is needed. GridinSoft Anti-Malware is what can help you with all purposes. It features frequent database updates that are very useful against adware, and heuristic detection – a silver bullet for spyware and other stealthy malware.