A torrent is a tool for free data exchange on the Internet. However, it is considered a symbol of piracy and copyright infringement. The term “torrent” in online communities is mainly used to describe downloading and uploading a file (often a movie, a piece of music, or a book) using a peer-to-peer network. But exactly how does it work? Is it safe to use torrents, and can you get in trouble with the law? Below we will answer all these questions and understand what a torrent is.
What is a Torrent?
A torrent, also known as a “torrent tracker” or “file tracker,” is a small file that keeps track of where the file you want to download is located on a network of different computers. It may not seem easy, but it is easier than you think. A torrent is a small file used by a torrent client that tells others, “Hey, I want to download and upload this particular piece of content for and from you.” You can use a torrent file to share media files, such as movies, music, etc., with others using a peer-to-peer network or “P2P”.
What is a Torrent Client?
The torrent client or torrenting client is software that uses a torrent file to find out who else has the file you want to download. The client gets data from all these computers by slowly adding small packets of the file you are downloading to your computer. The torrent client also downloads small packages of that file from the other computers. This is what forms a P2P network. A torrent client is software that connects downloaders and uploaders of a particular file, using a torrent file to determine which file to share.
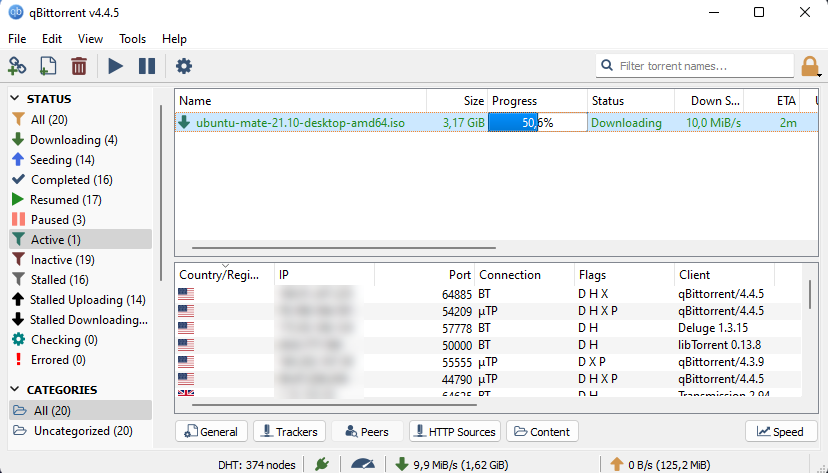
What is Peer-to-Peer?
A peer-to-peer or P2P network allows computers to share a workload while performing a specific task. It differs from the usual client-server model, where a user simply downloads a file from a server. In a torrent case, using P2P, each computer connects to the other to download (leech) and upload (seed) a particular file. In this sense, the people who share the file act as small servers to download the file using the torrent client.
What are Seeders and Leechers?
Seeders and leechers are terms used to refer to different parts of the P2P network. When a client downloads, it is called a leecher because it leeches a file from others. When uploading, the client is called a seeder because it seeds files for others to download. When you use a torrent client, you are both a seeder and a leecher because you are simultaneously downloading and uploading parts of a particular file. When you have fully downloaded a file, you become a seeder because you are no longer downloading the file.
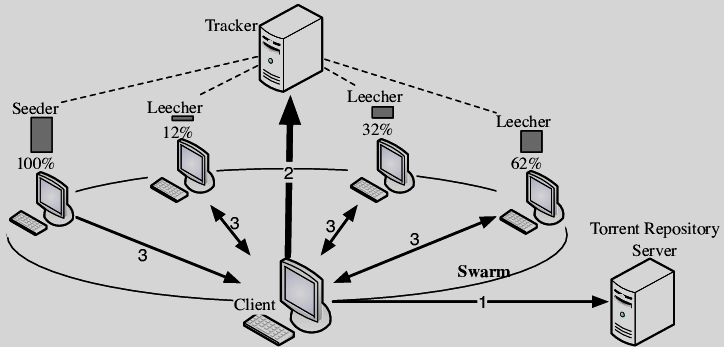
How Does Torrenting Work?
As written above, a torrent works on the P2P principle. First, you have to upload a torrent-client – a program that allows you to participate in this network. Additionally, you’d need a tracker – a small file that contains the information about the file that will be managed. The torrent client uses this tracker to see who else has the actual file you are about to download. For example, suppose you want to download a movie, and the torrent client gets the data from all those computers, adding snippets of the file you are downloading to your computer.
While you’re downloading those snippets, you’re also giving the snippets you’ve already downloaded to other people, turning your computer into a small server. This download process continues until you completely download the file or stop your torrent client from sharing the file. You will usually have to stop sharing the torrent manually to stop sharing the file.
Where do People get Torrents From?
First, you need to get the torrent file itself. There are now various websites that host these files. They are called torrent sites. An example of such a site is Pirate Bay. However, many torrent sites contain copyrighted content, so downloading such torrents is fraught with legal problems. Some torrent sites, such as Kickass Torrents and The Pirate Bay, have even been shut down with the help of local law enforcement. Even though downloading a torrent is perfectly legal, a great number of files on these sites are copyrighted.
Is Torrenting Legal?
Yes, the use of a torrent itself is legal. This means that it is not illegal to download and upload packages of a specific file. However, most countries have a law that prohibits downloading copyrighted content. This is called piracy, and people involved in copyright infringement are commonly referred to as pirates. However, whether punishment follows depends a lot on where you live. For example, in most countries, especially in Eastern Europe or Latin America, torrent use, although illegal, is rarely enforced. Therefore, it is common to use torrents without any security measures.
However, in cases where the fact of piracy is tracked and acted against, you can get a hefty fine. Unfortunately, only a small number of people downloading copyrighted content get fined or sued. However, suppose you are caught downloading illegal files in countries like Germany. In that case, you will probably receive a huge fine in the mail. Moreover, for consequent software piracy acts you will likely face an imprisonment. Additionally, the company you’re working for will likely to pay a fine as well, and also face legal consequences as the use of pirated software for commercial purposes is punished in a way more severe manner.
What are the risks of using torrents?
Consider a few risks if you want to download from a torrent. The most common problem is downloading malware along with or instead of the file you want. Although this problem has been observed since the early 2010s, those regions where torrents are popular are still at the top of ransomware infections. Here are the most significant risks you may encounter when downloading torrents:
- You may download copyrighted content. This is considered illegal in most countries and can cause serious legal problems.
- Hackers can attack torrent downloaders in many different ways.
Read on to learn more about these risks.
The risk of downloading malware
One of the most significant risks when downloading via torrents is getting infected with a virus. Threat actors who may create the distribution along with other users may embed malware in the files. Since most giveaways contain cracked software with the keygen, the authors often ask to disable antivirus. This gives the green light to any malware. Therefore, it is essential to use proper anti-virus software when surfing the Internet.
Risk of violating the law
When you use torrent clients to download copyrighted material such as movies, songs, books, or video games, you get copyright-protected content without paying for it, which is outside the law. Even if your region does not currently enforce copyright laws on torrents, this may be corrected in the future. Using pirated software is much more risky, as it can be detected through the traces a hacked program leaves in the files, created with its use.
How to Stay Safe When Torrenting
You can take the following steps to be safe when using torrents. It is worth noting that downloading copyrighted content is illegal, and we strongly recommend against it. However, there are also many fully legal torrents. To stay safe when using torrents, follow these tips:
- Use only trusted, reliable torrent sites considered safe and free of malware.
- Use proper anti-virus software, such as GridinSoft Anti-malware, to protect against any unwanted malware you may encounter when downloading a torrent file.
- Refrain from downloading copyrighted content so as not to break the law.
That way, the very act of downloading a torrent is 100% legal. All you are doing is transferring data. You can use torrent programs to download and share files with other users.