Polymorphic and Metamorphic Malware: the Comparison
In this article, we consider two types of pests: polymorphic and metamorphic viruses, which were designed to destroy the integrity of the operating system and harm the user. Before we find out what is the difference between polymorphic and metamorphic viruses, let’s figure out what is virus in general and where it originates.
📌 Virus is a type of malware that aims to infect the victim’s device, break its integrity and distribute its copies for further infection. Malware is malicious software, any program that is designed to do harm to its victim via stealing money or data, extortion, digital vandalism, work disruption, identity theft, etc.
What is Polymorphic Virus?
To understand what a polymorphic virus is, let’s first pose a threat. This threat is constantly hidden from anti-malware, it manages to create itself a similar virus as if it regenerates. The main purpose of the threat is the users device and data thereon, for which it is ready to change as much as it takes. So to summarize:
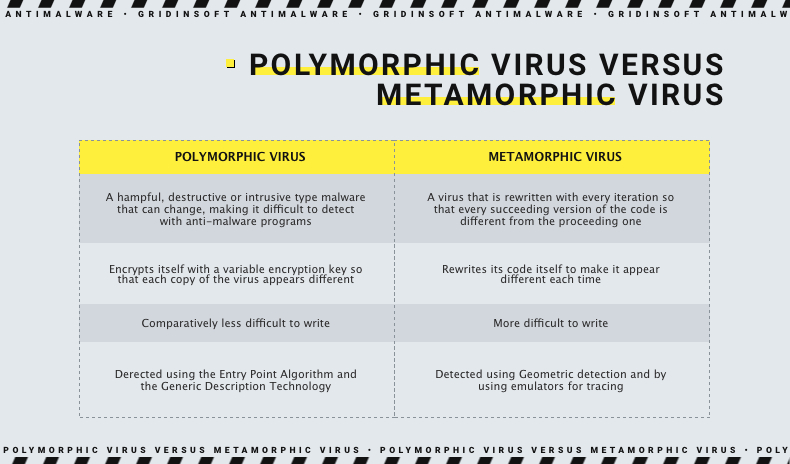
A polymorphic virus is a complex virus that is encrypted with a variable key so that each copy of this virus differs from the other. The purpose of this virus is to hide from anti-malware or scanners. Any pest can be detected through anti-malware or scanner, but this virus is smart, it has learned to pick up different encryption keys. For example, the user downloaded a file on the website, then the second user entered the same site and downloaded the same file. However, the two downloaded files don’t look the same for security programs.
In the normal course of action, a scanner or anti-malware could detect the virus through two identical keys in different files, but a polymorphic virus uses different encryption keys on different files, making the task more difficult than it seems. Therefore, there are two methods by which it is possible to detect polymorphic viruses. This is a general description of the technology and an algorithm of the input point. The general description technology allows the file to be run on a protected virtual computer. The login algorithm provides machine code verification at the point of each file, so it uses software virus detection.
What is Metamorphic Virus?
Now let’s start looking at metamorphic virus. It will reprogram itself. What could it mean? The virus tries to outmaneuver the antivirus and transmits its own code and at the same time creates a temporary representation. After it has bypassed the security, it is written back into the normal code. Copies of this virus are always different, making it difficult for anti-malware to detect these copies.
A metamorphic virus can be transformed due to its ability to edit, rewrite and translate its own code. The purpose of the virus is to damage the computer but to make it so that it is unnoticed by anti-malware. Metamorphic virus does not use encryption keys to change its copies. The virus converts its existing instructions into functionally equivalent instructions when creating its copy. This is why the virus cannot return to its original form. This is the moment that complicates the work of anti-malware programs. There are two methods to detect metamorphic viruses: using emulators for tracking and geometric detection.
Difference Between Polymorphic and Metamorphic Virus
While these viruses are generally similar in that they attempt to circumvent the security system by altering their own codes, there is still a difference between them.
- Polymorphic virus involves changing each copy of its code to bypass anti-malware protection, while Metamorphic Virus with each iteration rewrites its own code.
- The polymorphic virus uses the encryption key to change its code, while Metamorphic Virus itself rewrites its code.
- Writing Metamorphic Virus is much more difficult for a programmer than creating a Polymorphic one, because you need to use several methods of conversion.
- Methods for detecting these two viruses are different. In the case of polymorphic viruses, we need such methods: general description technology and input point algorithms. And in the case of Metamorphic Virus, you need to use the following methods: the use of emulators for tracking and geometric detection.
This article made us realize that attackers find more and more methods to infect systems every day. In order to reduce the risks of infection and prevent threats, install an effective security program on your PC. Gridinsoft Anti-malware is a great choice. Do not neglect your safety. Gridinsoft Anti-Malware is proper and reliable protection that will be your best line of defense.