Researchers report about a new malware strain dubbed FBot. This Python-based malicious program appears to be a unique tool in cybercriminals’ arsenal. Its uniqueness is due to its targeting of web and cloud services. Deeper analysis reveals that it was potentially made for a specific cybercrime group or for the use in specific attacks.
FBot Targets AWS, Twilio and Office365
FBot is a Python-based hacking tool that was recently detected by SentinelOne analysts, particularly in its targeting of cloud services and payment platforms. FBot’s primary function is to hijack cloud, SaaS, and web services, with a secondary focus on obtaining accesses for further attacks. Among its most noteworthy features are credential harvesting capabilities, essential for initial access and potentially lucrative through the sale to other cybercriminals. FBot shares some commonalities with typical stealers, particularly in its functionalities related to credential harvesting and account hijacking.
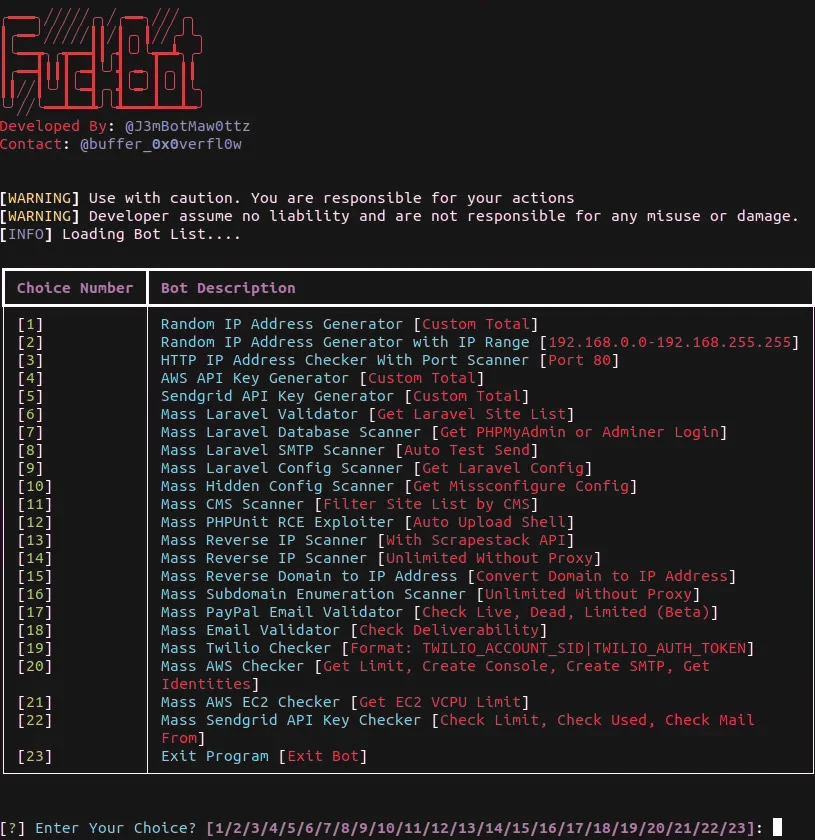
Distinct from other infostealer malware families, FBot does not lean on the commonly used Androxgh0st code. Instead, it carves its unique path, sharing functional and design similarities with the Legion cloud infostealer. Its smaller footprint suggests private development and a targeted distribution strategy. It tops up with its extensive capabilities, including tools for hijacking AWS accounts and credential harvesting for spam attacks. Additionally, it has specialized functions to target PayPal and various SaaS accounts.
AWS Targeting
There are three functions in FBot that are designed specifically for attacking AWS accounts.
Let’s look at each of yb] in more detail:
- AWS API Key Generator
This function of FBot creates artificial AWS API access keys. Think of it like trying to make duplicate keys for a lock, but without having the original. It randomly generates these keys hoping to guess the correct combination that will give access to an AWS account. Once succeeded, it allows unauthorized users to access the services without the manipulations visible to administrators. - Mass AWS Checker
This part of FBot inspects AWS account properties, permissions and services. In particular, it looks into the email configurations of AWS Simple Email Service, focusing on email sending capabilities. Moreover, it takes a step further by trying to set up a new user within the AWS account with administrative access. Such functionality may further be useful for performing massive email spam campaigns. - AWS EC2 Checker
One more function checks the AWS EC2 service permissions and capabilities of the compromised account. FBot checks what resources the account has available, which could be useful for someone planning to utilize these resources without authorization. Further use may be different, as spare calculation power has extremely versatile applications.
Exploiting Payment Services and SaaS Platforms
FBot’s targeting of SaaS and Payment Services is multifaceted. It includes a feature for PayPal account validation, termed “paypal_validator,” which checks if an email is linked to a PayPal account. This is executed by sending a request to a hardcoded URL, uniquely utilizing a Lithuanian fashion designer’s website for authentication. This may allow transactions hijacking or similar mischievous activities.
Additionally, FBot targets several SaaS platforms, including Sendgrid and Twilio. For Sendgrid, it has a feature to generate API keys, while for Twilio, it takes input in the form of SID and Auth Token. Similarly to AWS SES, hijacked Sendgrid accounts may further be used in impersonation email scams. Meanwhile, dumping Twilio SID/Auth Token data, malware provides its masters with quite a bit of info regarding the account – currency, balance, connected phone numbers, etc.
Web Framework Vulnerabilities
FBot’s capabilities in targeting web frameworks are particularly focused on exploiting vulnerabilities in various environments. It has a feature for validating if URLs host a Laravel environment file and extracting credentials from these files. This functionality enables FBot to potentially access sensitive configuration information. Additionally, it includes a Hidden Config Scanner, which sends HTTP GET requests to several PHP, Laravel, and AWS-related URIs, looking for stored configuration values. This scanner parses responses for keys and secrets related to a range of services, making it a potent tool for extracting valuable data from compromised web frameworks.
Protective Measures
To combat FBot’s threats, it’s crucial to understand its indicators of compromise. These include specific SHA1 hashes and hardcoded AWS IAM usernames and passwords used by FBot. The fight against FBot isn’t just about detection; it’s also about proactive defense.
- Employ comprehensive antivirus solutions that are regularly updated. Modern antivirus software is equipped with advanced detection capabilities to identify and neutralize malware like FBot. These tools often include real-time monitoring, heuristic analysis, and behavior-based detection, which can be particularly effective against new and evolving threats.
- FBot may use spamming tactics or exploit network vulnerabilities to gain entry. For spam protection, a robust firewall acts like a vigilant gatekeeper, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. By setting up appropriate firewall rules, you can effectively block malicious traffic and unauthorized access attempts, reducing the risk of FBot infiltrating your network.
- Organizations are advised to enable multi-factor authentication (MFA) for AWS services and set up alerts for any unusual activities, such as the creation of new user accounts or significant changes in SaaS configurations.