SYSDF is a ransomware-type program that belongs to the Dharma malware family. Such malicious software aims mainly at small companies, aiming at file encryption with further requests for ransom payment for their decryption. It was originally discovered by Jakub Kroustek on February 16, 2024.
What is SYSDF Ransomware?
SYSDF ransomware is a yet another example of Dharma ransomware, a malware family active since 2016. First detected on February 16, it appends its unique SYSDF extension to the files, along with the complex mask with the attack information. The latter includes victim ID and the contact email the victim is supposed to reach the hackers on. Following the encryption, the files start looking like the following:
Image1.png → Image1.png.id-C3B22A85.[[email protected]].SYSDF
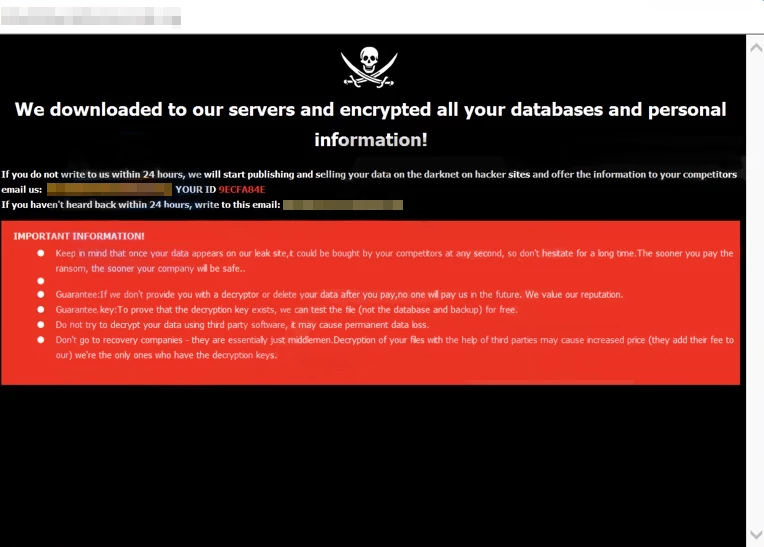
Upon finishing the encryption, malware creates its specific README!.txt files in each folder that includes encrypted files, and also on the desktop. Additionally, malware spawns and opens a file named info.hta, so it acts as notification for a victim. Below, you can see the messages from both ransom notes.
Text in the README!.txt ransom note:
Your data has been stolen and encrypted!
email us
[email protected] or [email protected]
How to Recover .SYSDF Files?
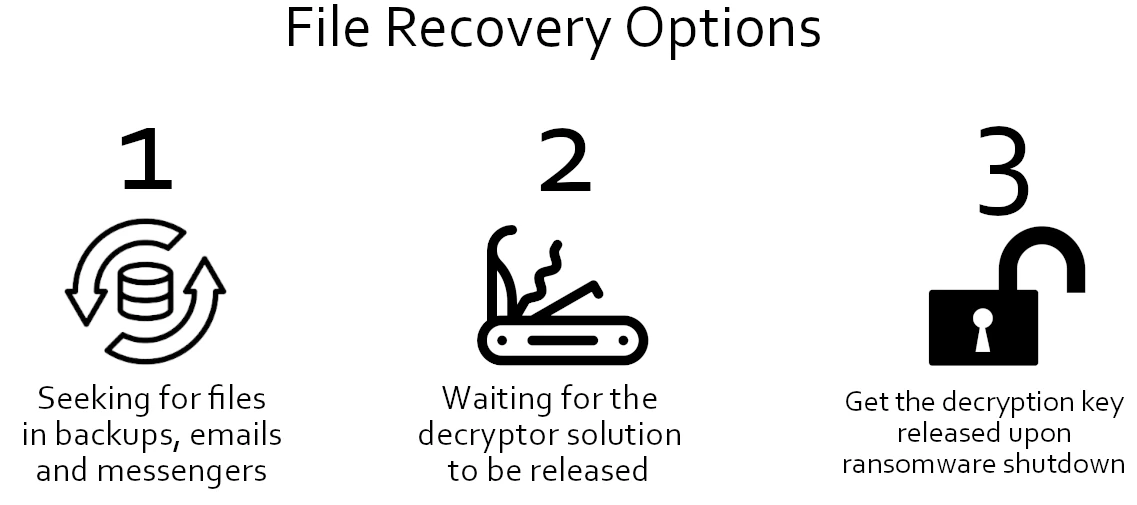
Unfortunately, there are no options for Dharma ransomware decryption available at the moment. The majority of file recovery services of “certified hackers” you can meet online will in fact only arrange negotiations with cybercriminals. Paying them is not a great idea, as this motivates them to continue the attacks. Losing the files is unpleasant, that is for sure, but as statistics shows, there are quite a few opportunities to get them back.
Try searching for backups or file duplicates, stored away from the affected system or network. Even a past version of the file is better than nothing at all. Aside from the backups, there is quite a hope on ransomware decryptors that exploit vulnerabilities in the encryption mechanism and allow you to get the files back for free. For January and February 2024, 4 decryptors for different ransomware families were published. Patience is key here, and considering the latest trends, this becomes a more and more popular option.
How to Remove Ransomware?
But before you do any file recovery operations, it is important to remove the malware beforehand. It did not disappear after finishing the encryption: SYSDF is still active, seeking for the new files to cipher. And be sure, it will do this as soon as you get a fresh unencrypted file to the disk.
For ransomware removal, I’d recommend GridinSoft Anti-Malware. Its advanced detection techniques along with live database updates allow it to detect even the most recent malware samples. Run a Full scan, wait until it is over, remove the detected stuff – and your system will be ready to any further actions, free of malware.