In the most recent release notes, Google reports about a new 0-day vulnerability that is already exploited in the wild. The update fixes the issue, but the very fact of it being exploited means it should be implemented as soon as possible. It appears to be the first 0-day exploit in Chrome browser in 2024.
New Chrome 0-day Vulnerability Fixed
On January 16, Google released an update for its Chrome browser that contains a fix for 3 vulnerabilities. Among them there is one, CVE-2024-0519, that was reported by an anonymous user. The company acknowledges the exploitation of this breach in the wild.
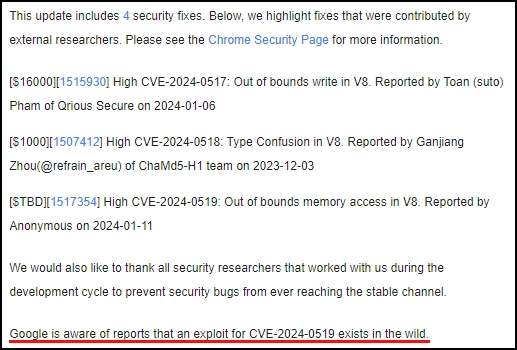
Key issue of the vulnerability lies in an improper memory access control in the JScript V8 engine, used in Chrome. The issue falls under CWE-119 designation. The way Chrome operates supposes the ability of direct memory addressing, but with lack of proper handling, it leads to the ability to reference to a wrong memory location. What this gives to attackers is the ability to both read and write to the random memory area, causing data leaks and arbitrary code execution.
Besides the most sensible issue, there are also 2 high-severity vulnerabilities fixed in the same update. Both touch V8 JavaScript, too, but are related to lack of memory write validation and type confusion. The latter, actually, can lead to similar effects with CVE-2024-0519, so it should be treated with the same seriousness. The good thing about these two is the absence of their real-world exploitation.
Google Releases Fix to the Newest 0-day Exploit
The severity of the issue obviously calls for urgent response from the developer. Fortunately, Google never hesitates to patch such bugs. However, due to the limitations, the patch may not be available to all users simultaneously. Here is the list of OS-specific versions that contain a fix.
| OS | Version with Fix |
|---|---|
| Windows | 120.0.6099.224(225) |
| MacOS | 120.0.6099.234 |
| Linux | 120.0.6099.224 |
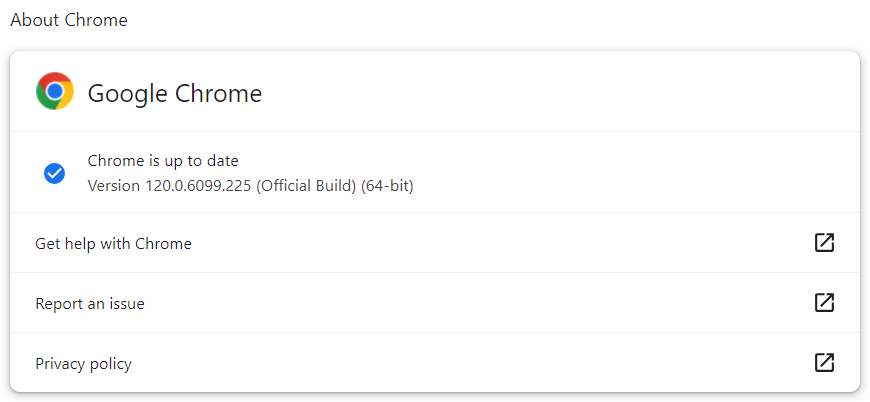
To check whether you have an updated version of the browser or to check for updates, go to Settings → About Chrome. This will open the menu which checks the update availability each time you open it.
Being the most popular web browser is not just about privileges, as you may witness. Such a humongous user base means increased (if not maxed out) attention from adversaries, who take such vulnerabilities nothing short of a gift. For ordinary users, the best way to counteract this is to keep an eye on the latest updates, specifically on what issues they fix.