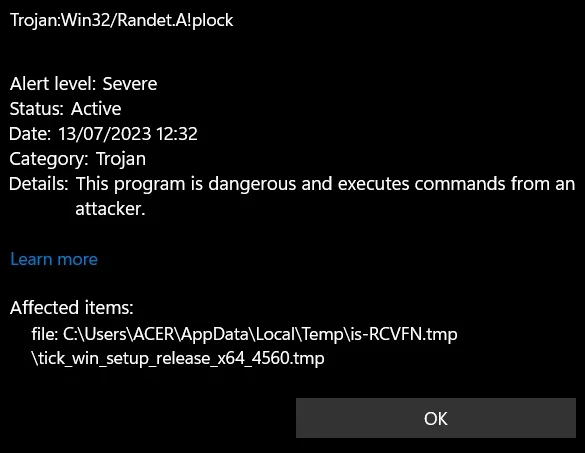
Windows Defender’s mass detections of Trojan:Win32/Randet.A!plock worries people. Are the user files complained about by Defender malicious?
Trojan:Win32/Randet.A!plock Microsoft Defender Detection
Recently, users have been actively discussing on thematic forums on the network about Windows Defender triggering on files that, according to the Defender, are Trojan:Win32/Randet.A!plock. According to users, the detected file may be a legitimate program, an anti-reader program, a game, or a file belonging to a legitimate program. A Reddit user is confused trying to figure out why TickTick, which he downloaded from the official site, Defender detects as Severe Trojan.
“Is anyone get the same issue as the image below? I tried installing TickTick many times but still got the same issue. Do you have any solution to fix this?” – Reddit user.
Roblox Studio users have encountered a similar problem.
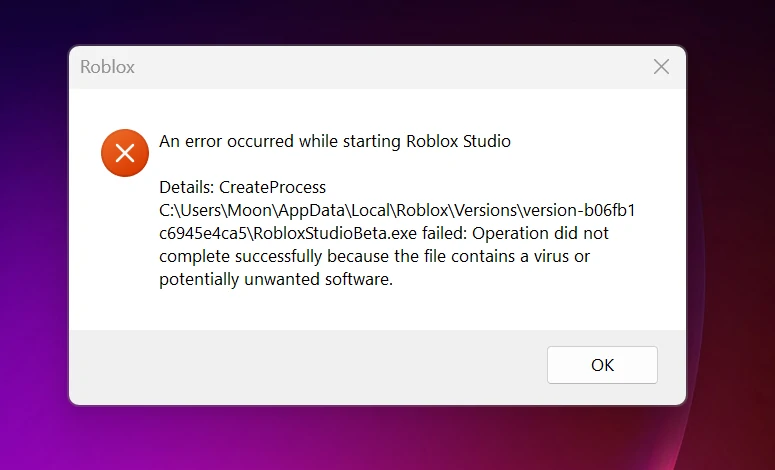
While these are not the only cases, users online are wary of these Defender notifications. However, some admit that the Defender’s detects may be false.
What is Trojan:Win32/Randet.A!plock?
As for Trojan:Win32/Randet.A!plock, it is normally a malware. More specifically, it is a stealer, which is obviously unpleasant and justifies users’ fears. We have a separate article dedicated to this malware type. But in short, info stealers can steal your personal and sensitive data by infiltrating your system. Attackers use this data for fraud, theft, or blackmail. They can also access your social media and email accounts to spread malware.
Although, in this case, the Defender’s triggering is more of a false positive, some users note that after installing the latest Windows updates, the false positive problem disappears. However, some users report that they still have the problem even after the update. Antivirus software can produce false positives due to imperfect detection algorithms, database updates, and fuzzy heuristic algorithms. Users can check suspicious files with online antivirus scanners or reliable desktop antimalware solutions to address this issue and exclude safe files from scanning.
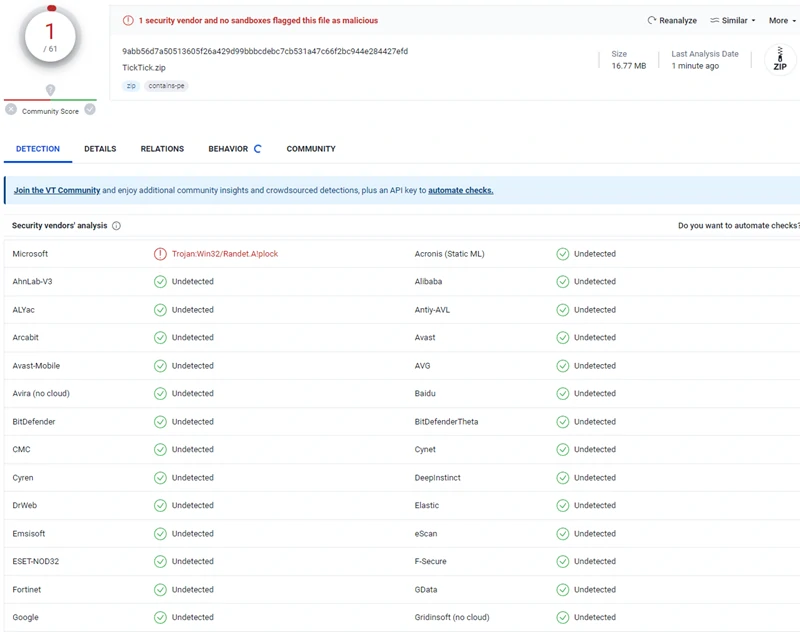
Make sure your system is clean.
Windows Defender is a good antivirus tool. Users can forgive it for some mistakes since it is free and part of the OS by default. However, attackers do not forgive mistakes. If you encounter a Trojan:Win32/Randet.A!plock detection notification, we recommend checking your system with a third-party anti-malware tool, such as GridinSoft Anti-Malware. This solution can work with Defender and provide advanced protection without overloading the system.