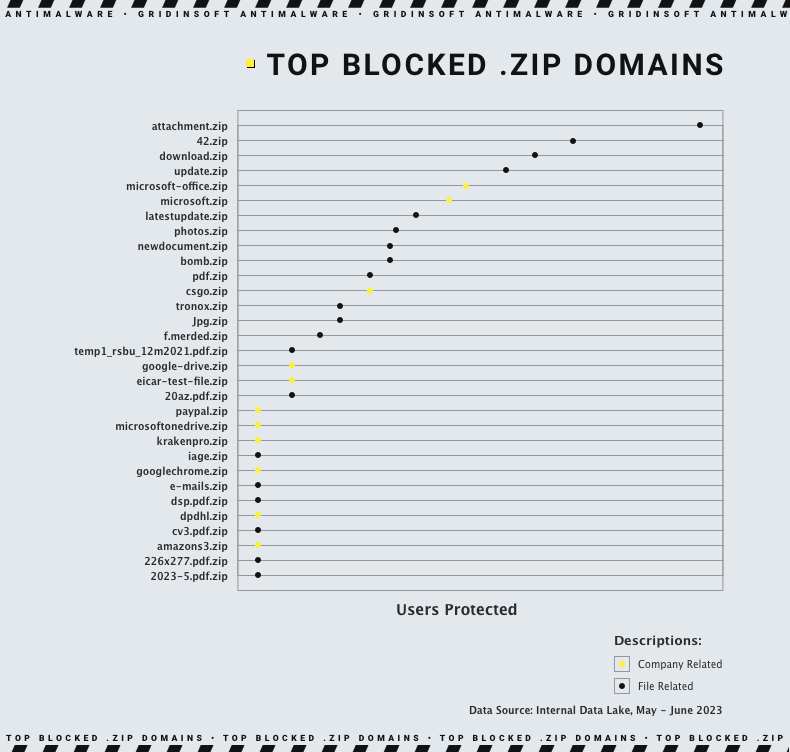
The Internet has become our second home. Every time we surf the Internet, we scammed. And this time, cybercriminals did not miss their chance to deceive us using a new “.zip” domain.
What’s a .zip domain?
Some time ago, Google allowed new Top Level Domain (TLD) names for registration. Those are .zip, .mov, and .phd. Now everyone can buy a domain with the .zip extension, just like purchasing domains with .com or .org extensions. However, the security community has expressed concerns about the potential risks associated with these new TLD.
Experts have discovered that cybercriminals are using .zip domains to deceive users into believing that they are downloadable files when they are URLs. Research indicates that one-third of the top 30 .zip domains can be blocked by our threat detection engines utilize the names of prominent tech companies, including Microsoft, Google, Amazon, and Paypal, to fool people into thinking they are trustworthy files associated with these reputable companies.
Earlier, such concerns appeared about TLDs like .xyz, .online, .biz, .info, .ru, .life, and .site. However, they were mostly true – the vast majority of sites using these domains were used in phishing, shopping scams and pop-up advertisements spam. This time, however, things could be worse.
Security Risks of .Zip Domain
These .zip domains are blurring the lines between a file and a website and making it harder to tell what’s what. One primary concern is the potential for file mix-ups, which can make it hard to tell apart local and remote sources, posing a security threat. Cybercriminals have created a prototype email that considers the possibility that the attachment and the link could lead to different places. This ensures better accuracy and avoids confusion for the recipient.
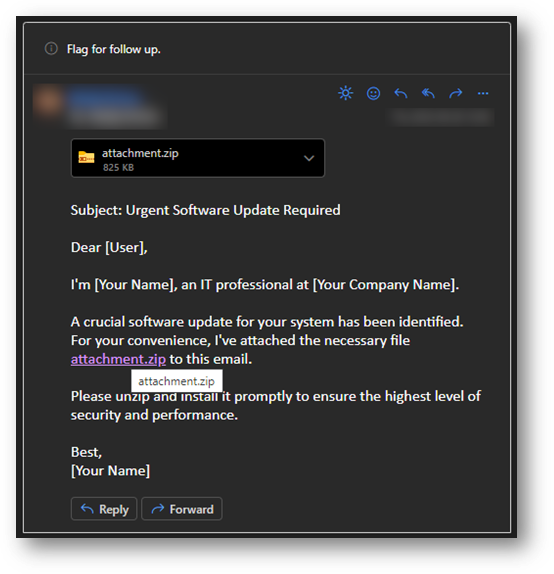
This is an example of a common scam created by cybercriminals. They send an email with an attachment named "attachment.zip," claiming it is a necessary software update. The email contains a link that seems to open the attachment but actually leads to a remote URL. It’s a sneaky tactic used to deceive unsuspecting users.
The Browser file archiver
There is a phishing kit called "file archiver in the browser" that uses ZIP domains to trick users into running malicious files. This attack makes fake WinRAR or Windows File Explorer windows appear in the browser, making it seem like the user is using actual software. Also, to make it even more convincing, the attackers are using a .zip domain. A security researcher recently discovered this phishing tactic.
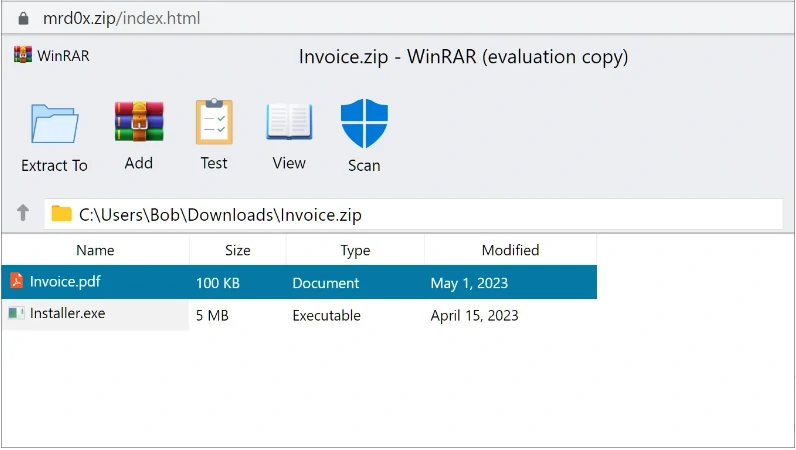
With the toolkit, it is possible to create a fake WinRar window within the browser that appears to open a ZIP archive and show its contents when accessing a .zip domain. But, this can be used to deceive users.
In conclusion, threat actors may use this phishing toolkit to steal credentials and distribute malware.
What are .zip domain phishing risks?
Security researchers have warned that domains using the “.zip” top-level and similar domains increase the chances of exposing sensitive information due to accidental DNS or web requests. With the new .zip TLDs, internet browsers and messaging applications like Telegram recognize strings that end with .zip as URLs and automatically create hyperlinks.
It has been found that these domains are susceptible to abuse, as evidenced by Silent Push Labs. This cyber intelligence firm recently detected a phishing page at microsoft-office[.]zip. This page designed to steal Microsoft Account credentials.
Potential @Microsoft phishing page abusing the new .zip top-level domain 🚨
Hosted on 151.80.119[.]120 → AS16276 @as16276
IoCs:
microsoft-office[.]zip
microsoft-office365[.]zip#phishing pic.twitter.com/gDhZMobXZp
— Silent Push Labs (@silentpush_labs) May 13, 2023
There is a debate among developers, security researchers, and IT administrators regarding the recent developments. Some believe the concerns surrounding the ZIP and MOV top-level domains (TLDs) are unfounded. In contrast, others think these TLDs pose an avoidable risk in an already precarious online environment.
Recommendations
Be cautious of websites with a .zip Top-Level Domain (TLD), as they may contain harmful content.
- Monitor your company’s web traffic and observe any unusual activities related to .zip TLDs. Above all, keep a close eye on these activities to ensure the safety and security of your company’s online presence.
- To enhance protection against possible threats, it’s advisable to introduce email filters that target messages containing .zip TLDs in their content.
- Keep your antivirus software updated to ensure it’s working at its best against any new threats. Make sure to check for updates to stay protected regularly.
- It’s essential to stay informed about emerging threats to stay safe from potential dangers. Also, Regularly reading security bulletins and reports can help you avoid these threats.