On Tuesday, December 12, 2023, Ukraine’s largest cellular operator Kyivstar got its network infrastructure ruined. This is a result of a hack that was most likely executed by a Russian threat actor.
I considered delaying writing this post to gather more facts regarding the situation. On day 1, nothing but speculation and suppositions were available. Today, some of the facts appear, allowing me to make a comprehensive analysis of the case.
Ukrainian Mobile Operator Kyivstar Hacked by Russians
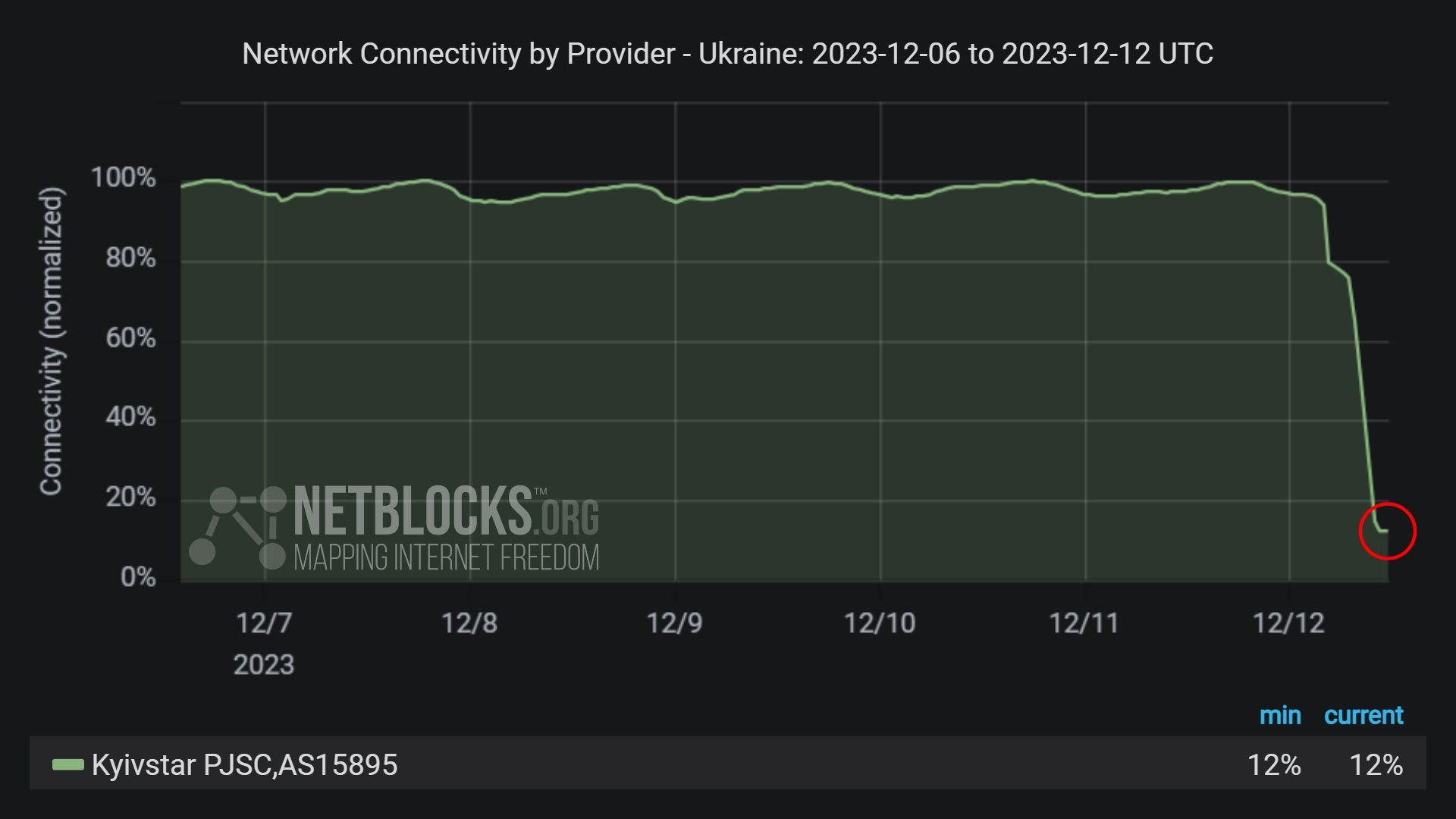
Early on December 12, Kyivstar services stopped working. As the company operates not only in the cell carrier segment, but also provides home Internet and connectivity services for businesses, these were down as well. The “national roaming” option, that allows switching between operators with certain limitations, was unresponsive, meaning that the network structure is severely disrupted.
At around 12:00, the first official comments from the company appeared. They claimed a cyberattack disrupting their services, and told about a rather long recovery process ahead. Further statements specified that the estimated time of major services recovery is not earlier than on December 13.
Until the evening of the same day, the details were lean. Some analysts tried to make conclusions, though they were at best blurred. Certain sources of information also supposed that Kyivstar suffered outages due to the DDoS attack, but that was likely just a confusion due to the simultaneous launch of a DDoS attack on one of Ukrainian banks. Meanwhile, the company succeeded with recovering part of its services, particularly the home Internet service to the end of the day.
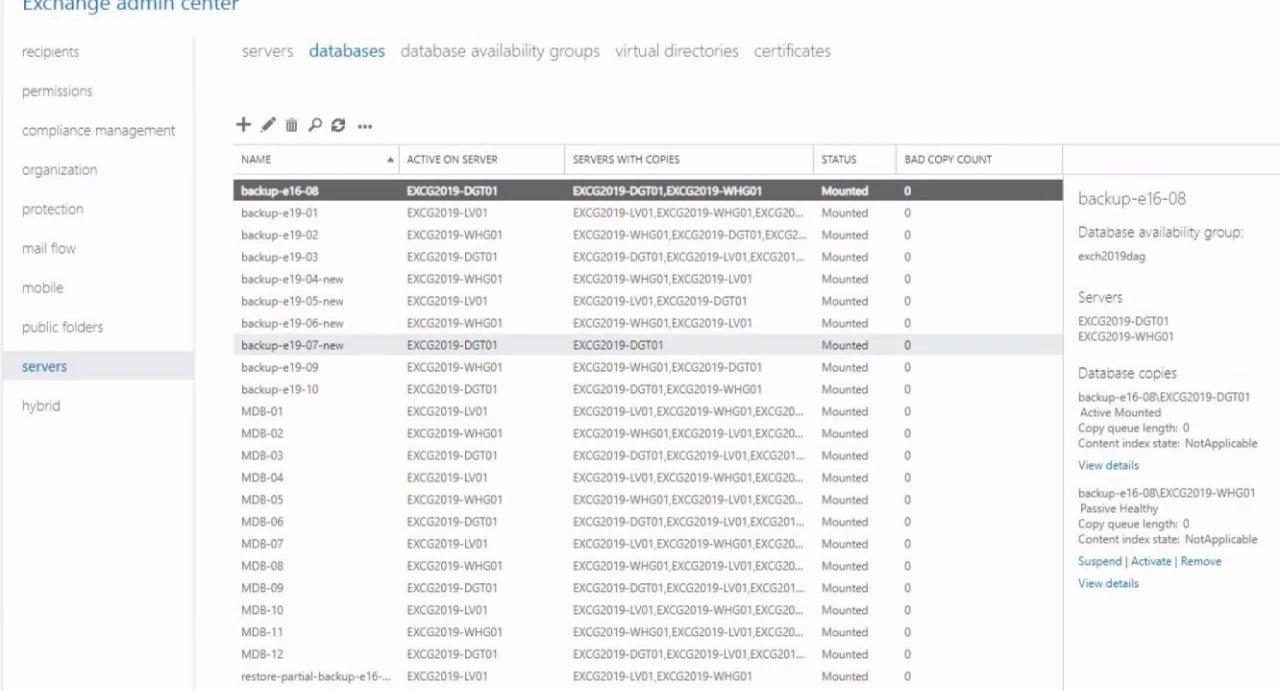
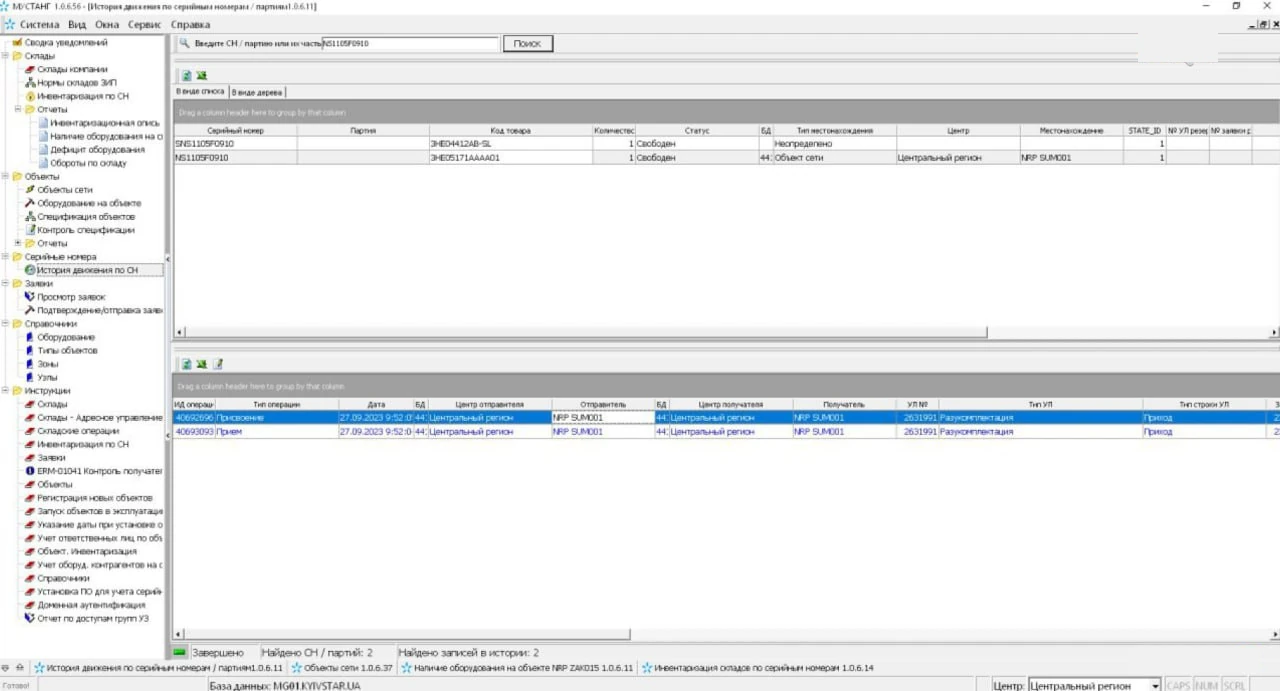
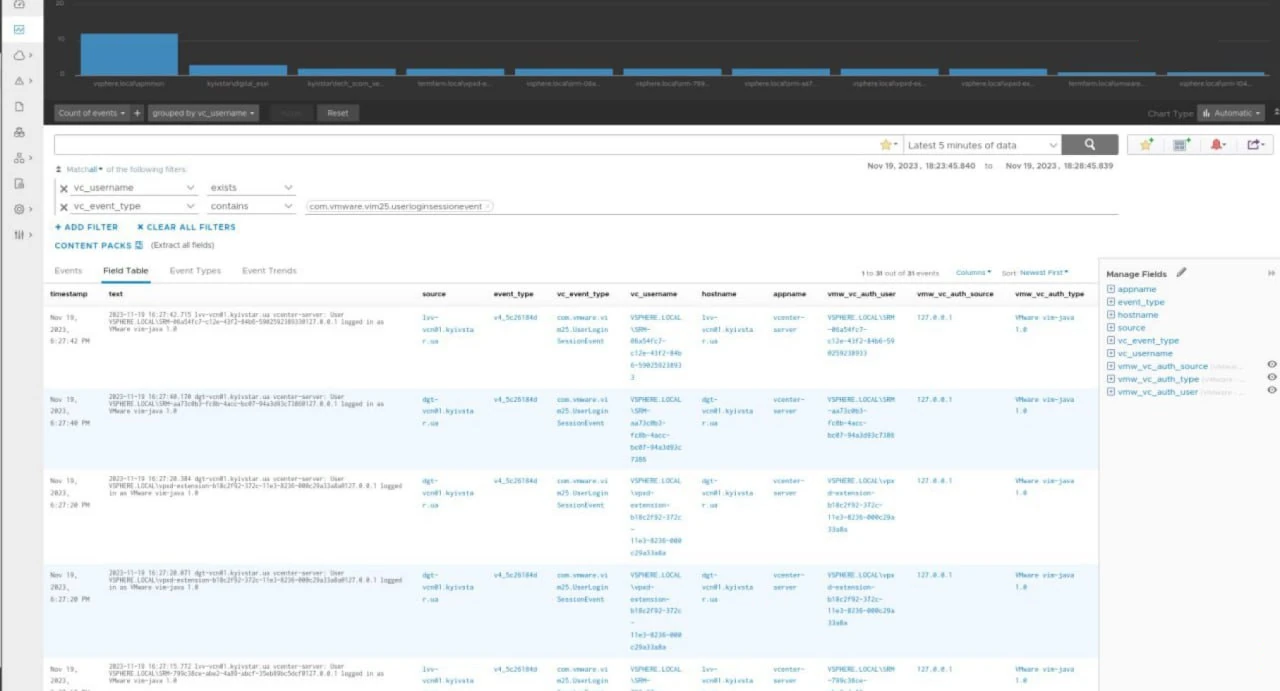
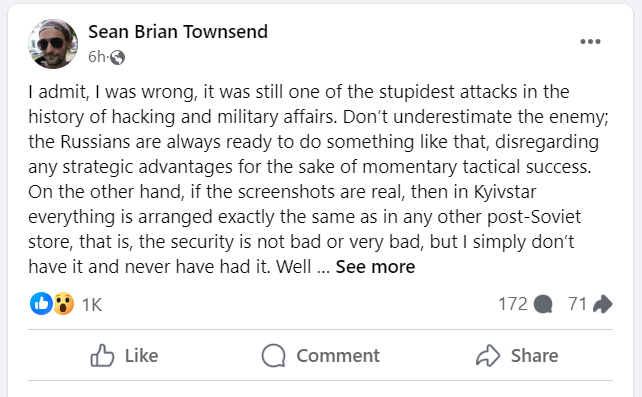
On the morning of December 13, 2023, some facts and even more rumors began to surface. Among the latter, the brightest was the responsibility claim from a previously unknown Solntsepek threat actor. The gang published their statement along with the screenshots of what they claim to be insight into the hacked network. Nonetheless, I heavily doubt credibility of both claims and screenshots, since no one heard of the group before, and no identifiable details are present on those pictures.
Unpredicted outcomes
As Kyivstar is the biggest cellular operator in Ukraine, the outage caused obvious troubles for over 24 million users. Considering the population of the country is around 40 million in total, the outage touched every second citizen to a certain extent. That obviously uncovered how hard people are dependent on technology nowadays, but some of the issues caused by the Kyivstar hack were not that clear.
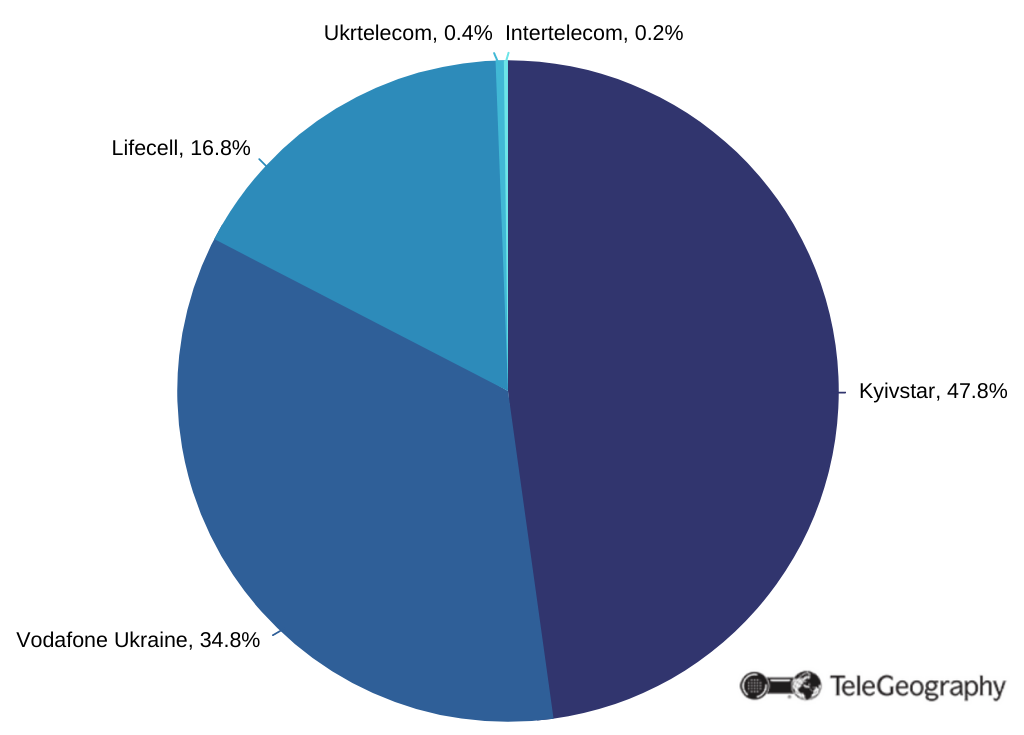
For instance, the air raid alarms – a heavily needed thing in a belligerent country – were reliant on the Kyivstar’s cell network. As a result, numerous cities across the country did not hear air raid alarms, and even online air raid maps were not able to work properly. That is especially unfortunate as rocket and UAV strikes happen on a daily basis.
What is less unfortunate for Ukraine though is that Russian troops who reside in the occupied areas of Kherson and Zaporizhzhia regions experienced cell coverage issues as well. Since invaders used stolen SIM cards of Ukrainian operators, their phones stopped working once the attack happened. Pay day for stolen SIM-cards, one may say.
Kyivstar Hack – Who is Responsible?
Well, all symptoms aside, let’s think of what exactly happened and figure out who is responsible for the hack. The character of destruction and the way the recovery goes supposes that hackers managed to establish persistence in the majority of infrastructural elements of the corporate network. Further, they destroyed all they could reach. That was not just a “DROP DATABASE”, as someone supposed before – in that case the recovery would not take that much time. Moreover, Kyivstar themselves claim that they are forced into recovering the network “piece by piece”.
The executor is, most likely, one of Russian APT groups. Sure enough, there is no confirmation, but there is no one to hack Ukrainian companies for pure vandalism except for Russians. Even though I doubt the claims of a no-name hack group, the nationality of hackers is almost certain.
Another edge of responsibility lies on the Kyivstar itself. Having such a large number of users creates significant responsibility, not only in the matter of service availability, but also data safety. Addresses, passport info, phone numbers, emails – all this was successfully leaked. Bad luck for a country in peacetime, culpable negligence for a country at war.
If the screenshots shared by the Solntsepek group are real, things can be much worse. An analyst under the nickname of Sean Townsend shares his thoughts regarding what the pics say. Spoiler – things may be extremely bad, and the security was non-existent at all.
Update 12/13 (21:00 GMT)
Olexandr Komarov, CEO of Kyivstar, uncovered some of the details regarding the beginning of the hack. The initial access was gained through a compromised account of an employee.
Are Other Companies in Danger?
What is the conclusion from such a situation? This is what all Ukrainian companies should be ready to counteract. And not only Ukrainian – Russian hackers are now naught on limitations in attacks on countries “rival” to Russia. Since hackers aim only for vandalism and do not try to monetize their job, the effects may be rapid and irreversible. A sturdy, well-engineered security system should be mandatory for all companies.