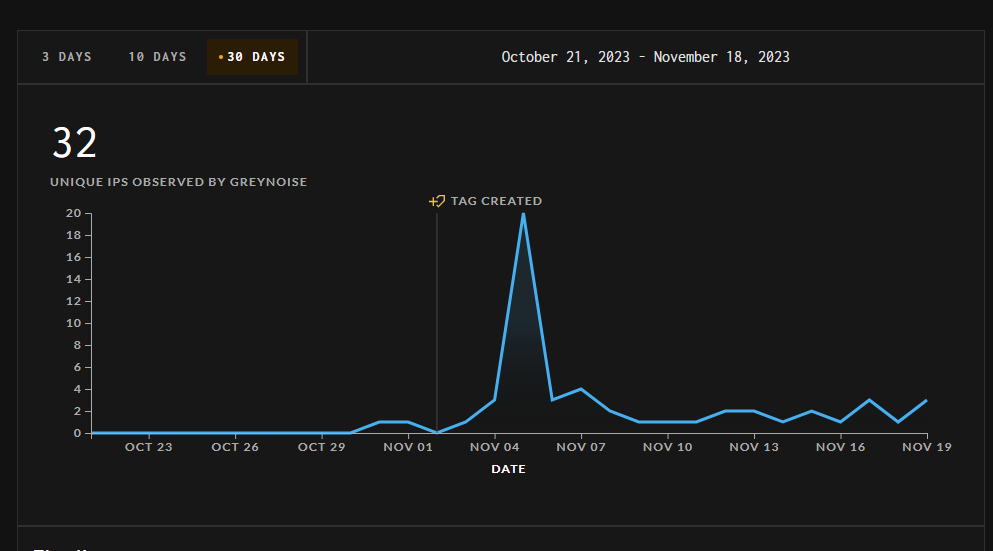
Recent Apache ActiveMQ vulnerability, that allows for remote code execution, is reportedly exploited in real-world attacks. Analysts noticed several exploitation cases that used this vulnerability to infect Linux systems with Kinsing malware. That is a rare sight of a high-profile vulnerability being exploited to infect exclusively Linux machines.
Apache ActiveMQ Vulnerability Allows for RCE
Analysts from TrendMicro warn about an active exploitation of an ActiveMQ vulnerability, discovered back in late October 2023. CVE-2023-46604 allows for remote code execution due to the failure of class type validation. Typically for RCE vulnerabilities, it received a high CVSS score of 9.8/10. Apache warned its clients, released fixes and recommendations regarding supplementary software that is related to the successful exploitation.
Despite the fast reaction from the company, hackers managed to start using this vulnerability for malicious purposes. As it usually happens, companies hesitate with updates, especially when they are not exploited at the moment. And it is completely understandable – for large corporations, who are the main ActiveMQ users, installing updates is always a pain in the neck. But now, there is a chain of successful exploitation – a great stimulus towards getting the latest software version.
ActiveMQ Vulnerability Exploited in the Wild
As the same research says, the known exploitation cases were aiming at the installation of Kinsing malware. This Linux threat is also known under the name of h2miner – which already says enough about its capabilities. Aside from Kinsing, hackers were using another, unnamed miner. Other reports say that CVE-2023-46604 exploitation is primarily done by the threat actor that stands behind HelloKitty ransomware.
Still, the 9.8 score for this vulnerability is not just to scare people. Being an RCE vulnerability, it can help with delivering any other malware to the target environment, depending on the wish of the attacker. It is great luck that the detected exploitation cases were mostly related to coin miners. There is always a chance that the very next attack will introduce ransomware, spyware, or their mix.
Available CVE-2023-46604 Mitigations
Back on October 24, 2023, Apache released a lineup of recommendations for ActiveMQ users. The main one though was concentrated on updating the protocol brokers to the versions where the breach is patched.
List of versions with the vulnerability fixed:
| Classic |
|
| Artemis | 2.31.2 |
The company offers no temporal mitigations, which leaves 0 ways to circumvent patching. However, several other approaches will provide you with better exploitation protection.
Extended Detection and Response solutions (XDR) are the cornerstone of modern corporate cybersecurity. When joined by SOAR and SIEM systems, XDR allows detecting, stopping and blocking all further attempts of a cyberattack within the entire environment. Policies like zero trust will enhance protection against exploitation even further, weeding out attempts to use well-known and trusted software in the attack.