It’s no secret that cybercriminals are increasingly using mobile platforms as an attack vector lately. One example is a new Android malware. It spreads through fake cloud mining scams services and targets cryptocurrency wallets and online banking apps. Analysts dubbed this banking trojan as Roamer, though hackers may use different other malware for such attacks.
What are we talking about?
The era of hype around crypto-mining is over, and the shortage of video cards and mining farms is a thing of the past. Today, cloud computing technology is making it possible to significantly lower the entry threshold into the world of crypto-mining. To start mining Bitcoin, for example, there is no need to buy expensive equipment. Instead, the user can rent computing power from cloud mining companies for a fee. Of course, scammers couldn’t stay away from this niche.
The current fraudulent scheme is as follows: attackers create a phishing website that pretends to provide cloud mining services. Unsuspecting users end up on the website, where they are prompted to download a smartphone app. However, instead of the promised app, the user downloads malware that steals crypto wallet data and other valuable information from their device. It sounds too obvious, but this scheme works if it’s being written about.
How the Cloud Mining Scams scheme works
A team of researchers discovered a phishing website with the address hxxps://cloudmining[.]uk[.]com, which looks like a cloud mining platform. The site has “Create Account” and “Sign In” buttons and links to download a mobile app from Google Play and the App Store for Android and iOS devices, respectively. However, attackers use a trick: when clicking on the “Google Play” link, the user is not redirected to the application page in the store, but a direct download of the .apk file named CloudMining.apk takes place. An experienced user might have noticed the unusualness of this behavior. Still, an ordinary user might not pay attention to it. This is precisely the kind of oversight that attackers are counting on. After downloading the file, the victim gets a malicious software module that aims to steal confidential data from the victim’s device.
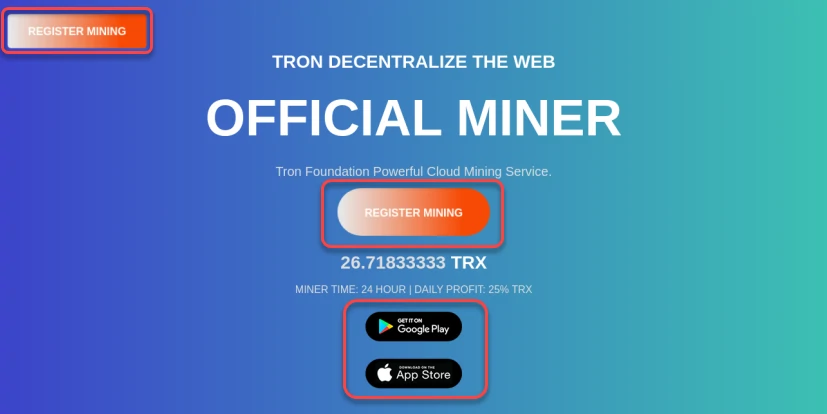
The Roamer Banking Trojan
The “Roamer” Banking Trojan is a malware that extracts sensitive information from infected devices. It targets various crypto wallets and banking applications. It is distributed through fraudulent websites and employs different themes, such as gaming or shopping mall names and icons. Once installed, the malware exploits the Accessibility Service to extract information from targeted applications. The malware targets the following cryptocurrency wallet and banking applications:
- HDFC Bank Mobile Banking App
- Bitso
- OKX: Buy Bitcoin, ETH, Crypto
- TokenPocket Wallet Crypto DeFi
- TronLink Pro
- Binance: BTC, Crypto, and NFTS
- Coinbse: Buy Bitcoin & Ether
- aelf Official Wallet
- Bitpie Wallet
- Trust: Crypto & Bitcoin Wallet
- MB Bank
- SafePal: Crypto Wallet BTC NFT
- KuCoin: BTC, Crypto Exchange
- Poloniex Crypto Exchange
- MetaMask – Blockchain Wallet
- SCB Mobile Banking
- ACB One
- VCB Digibank
- PayPal – Send, Shop, Manage
- MSB mBank
- VietinBank iPay
- Coinbase: Buy Bitcoin & Ether
- Bybit: Buy Bitcoin, Trade Crypto
- Huobi: Buy Crypto & Bitcoin
- imToken: Crypto & DeFi Wallet
Roamer Trojan steals sensitive data, including crypto wallet details and banking credentials. It automatically inserts TA’s crypto address into the victim’s app and transfers funds to TA’s account. In addition, it collects SMS data, files, and location details from infected devices. It can open targeted apps, take screenshots, and initiate screen recording. Stolen data is transmitted to a C&C server.
Telegram channel for phishing distribution
Researchers also found an active telegram channel that began its activity on May 15, 2023, and has more than 5 thousand subscribers. Supposedly, scammers use this channel for their purposes and to attract victims. The channel regularly publishes information about cloud mining schemes and distributes phishing websites hxxps://cloud-miner[.]cc and hxxps://cloud-miner[.]top. Although the latter site has a different design, it also involved cloud mining scams. It offers to download the previously mentioned smartphone app.
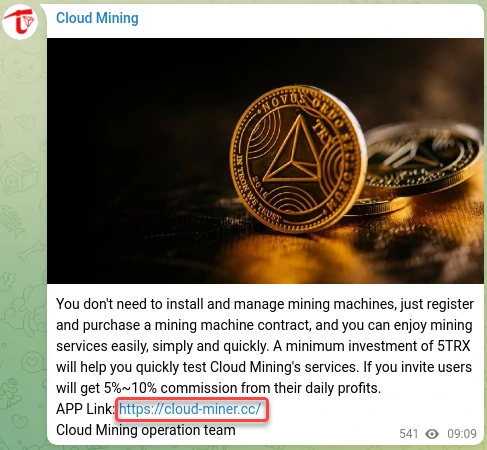
Another phishing site
These sites have “Sign in” and “Sign up” buttons to give them a realistic look, but they are not just decorative elements. Clicking on these buttons will redirect the user to another phishing site, hxxps://cloud-mining[.]vip, which offers to create an account and mine Tron (TRX). After registering, the user will be prompted to top up their wallet to start mining, a typical scam scheme. As you may have guessed, it simply hijacks your wallet, since the site intendedly lacks any forms protection.
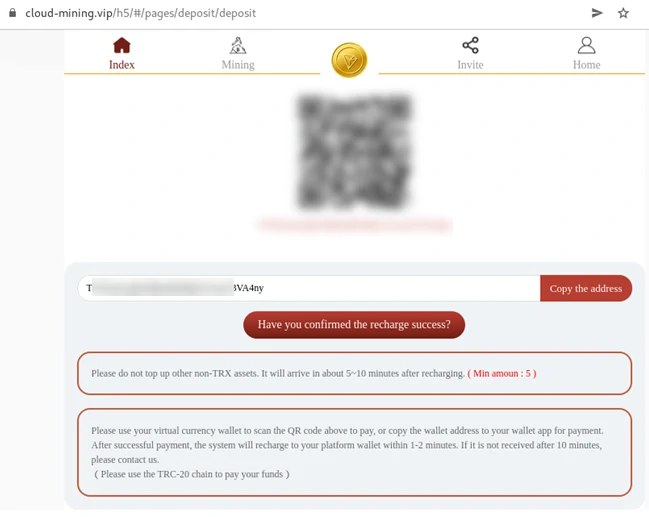
Safety tips
The following are tips to help prevent unpleasant experiences with this cyber threat:
- Only install software from official app stores. This is the Google Play Store for Android and, for iOS, the App Store. While this doesn’t guarantee 100% protection against rogue apps, it significantly reduces the chances. Also, if you are an Android user, ensure that Google Play Protect is turned on.
- Use biometric security features such as fingerprints or facial recognition to unlock your mobile device.
- Use strong passwords, change them periodically, and use multifactor authentication wherever possible.
- Update your device firmware and apps to the latest version to fix vulnerabilities and improve security.
- Be wary of links from unknown senders in SMS, messengers, and emails. Don’t click on them, especially if they are suspicious.
- Never give anyone your banking information or confirmation codes, even if they pretend to be from a bank or other organization.


