127.0.0.1. You’ve probably seen this number on memes, t-shirts, and tech documents. But what exactly is it, and why is it so popular? Let’s dive in and find out. 127.0.0.1 is a special Internet Protocol (IP) address known as “localhost“. As the name suggests, it’s used locally to create an IP connection with your own computer. This address makes sure that any data packet sent to 127.0.0.1 never leaves your computer. Instead of being sent out to the local network or the Internet, it “loops” back to the same computer that sent it, making your computer both the sender and the recipient.
According to RFC 1122, the “Internal loopback host address. Such addresses MUST NOT appear outside the host”. This means that routers will drop any traffic for 127.0.0.1, ensuring it stays within your computer and doesn’t reach the Internet. While 127.0.0.1 is the most famous, it’s part of a larger range (127.0.0.0 – 127.255.255.255) reserved for loopback purposes, as explained in RFC 6890. For IPv6, the loopback address is a bit longer: 0000:0000:0000:0000:0000:0000:0000:0001, but it’s usually shortened to ::1 for simplicity.
How Does the Internet Protocol Work?
IP (Internet Protocol) is a set of rules that provides a standardized method of addressing and communication between computers and other network devices. In IPv4, 127.0.0.1 is the most widely used worldwide. IETF RFC 791, finalized in September 1981, is the current definition of the protocol. Although IPv6 is gradually replacing IPv4, its adoption is still under development.
IPv4 is considered a connectionless protocol intended for use in Ethernet networks. Therefore, the protocol does not guarantee delivery, data integrity, or correct data consistency; instead, relying on the Transmission Control Protocol (TCP) to solve these problems.
How Does 127.0.0.1 Work?
Establishing a network connection to the loopback address 127.0.0.1 is almost identical to any remote computer or device on the network. The main difference is that connecting to 127.0.0.1 does not use the LAN interface hardware. Usually, system administrators and application developers use 127.0.0.1 to test applications. When establishing an IPv4 connection to 127.0.0.1, a subnet mask of 255.0.0.1 is generally assigned.
Suppose any public switch, router, or gateway receives a packet that someone has addressed to a loopback IP address. In that case, it should discard the packet without logging information. As a result, if a data packet accidentally gets outside the local node, it will not reach the computer. This aspect of loopback helps to ensure network security.
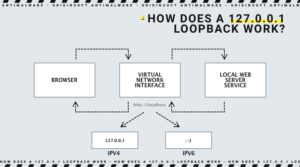
What Is Localhost?
In most cases, localhost is just an acronym that, by default, refers to 127.0.0.1. However, you can change it – by editing the hosts file, you can make localhost refer to any reserved addresses as to 127.X.X.X. You can also create other localhosts, such as localhost2, which may reference 127.0.0.2, for example. As IPv6 gradually sees its usage in the network structure, more and more devices will likely soon use ::1 as their default short-circuit address. Even though 127.0.0.1 has been in use for decades, it will still be in use for the next ten years.
Using 127.0.0.1 in Hosts File
Each time a computer user attempts to access a Web site or remote computer by name, the computer first checks the Hosts file for domain name resolution. It then sends a query to the DNS server. IP address 127.0.0.1 is usually found in the Hosts file on computers that are assigned a plain English “localhost” address.
It also sees its use in malware approaches to block access to legitimate websites. Hence, the end user cannot search for computer security help while dealing with malware. This change often appears together with a great variety of malware packages, that crooks deploy on the Internet. In particular ransomware, spyware, coin miners, and rogue software are the usual contributors to such a change.
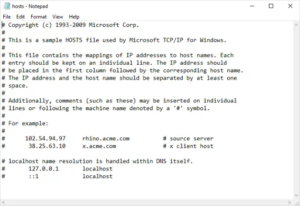
Some administrators may modify the “hosts” file to prevent access to unwanted websites. Examples of entries in the hosts file:
127.0.0.1 localhost
127.0.0.1 www.google.com
127.0.0.1 facebook.com
Google.com will not load in this case, or you will see the page you’ve established on the localhost address instead of the search engine site. Another case when you can be redirected to a 127.0.0.1 is a specific setting in a Domain Name System (DNS)
What is the Domain Name System?
Unlike machines, people have difficulty remembering IP addresses, and web addresses in plain language are much easier to remember. However, the Domain Name System (DNS) was developed to convert easy-to-remember addresses into numeric addresses for a remote computer or server. Its job is to direct local and Internet traffic to the appropriate destination by searching for an Internet address in real-time with other DNS servers located on the Internet. But before the local computer sends a DNS query to the local network DNS server, it will first check the locally stored hosts file to save time and network resources.
The hosts file contains pairs of IP addresses along with one or more hostnames. It sometimes receives updates depending on certain conditions on the local computer. Before the invention of DNS, one Hosts file was available over the network. However, this did not pass the scalability test. So, when several networks started to connect, it led to the development of the current DNS system.
What is the Use for Localhost?
What might be the purpose of having packages return to the same computer? There are several common uses. For example, to test something: suppose you have a server or a website that you will put on your local network or the Internet. With localhost, you can first run the server and client on the same computer to ensure that all the basics work correctly. This is how application developers perform basic network function checks when developing a program or component of an application before “going live” on the network or Internet with testing or deployment. It is common to check the computer’s networking hardware, operating system, and TCP/IP implementation. To do this, a ping request is sent to the address 127.0.0.1. According to the results of the test, administrators or users of computers can fix network connectivity problems.
It is, of course, worth mentioning the “easier” use of loopback. More experienced Internet users trick computer security or computer science students into trying to hack, examine, or test the network’s speed using the address 127.0.0.1. On the Internet, you can also see variations on the “World’s Worst Hacker” theme. In these stories (which may have actual events as a base), fellow hackers encourage “newbies” or “not too knowledgeable” hackers to infect, hack or conduct a DOS or DDOS attack on 127.0.0.1. In the humorous stories, the hacker manages to infect or delete information from his computer, causing a fit of laughter from the audience.
Where is 127.0.0.1 Defined?
The first document the Internet Engineering Task Force (IETF) posted was RFC 1700, which reserved a 127.0.0.0/8 address block for loopback. The IETF document, RFC 3330, describes using the IPv4 address block 127.0.0.0/8 for loopback. These definitions were later updated exclusively through IANA and cannot be assigned by regional Internet registries or IANA.
Localhost in IPv6
The loopback address in IPv6 is ::1 or abbreviated as 0:0:0:0:0:0:0:1. It performs the same function as in IPv4, allowing a host to send a packet of data to itself. It also cannot be assigned to any physical interface on the computer and is considered to have a “link-local” scope. The ::1 address cannot be used as the source address in IPv6 packets sent beyond one node, and the IPv6 router cannot forward the data packet. If a packet with such an address is received on an interface, it must also be discarded. Loop, “unspecified addresses,” and IPv6 addresses with embedded IPv4 addresses are assigned from binary prefix space 0000 0000 0000.
No opan in Google