Sihost.exe is a crucial background process for Windows 11/10 that governs essential features like the context menu and action center. However, it can sometimes malfunction and disrupt system stability. In this article, we unravel the essence of Sihost.exe and equip you to eliminate troubles within your system.
Sihost.exe – What is It?
Windows has many background processes, each of which is responsible for something. The Sihost.exe process (Shell Infrastructure Host file) is a critical executable file that executes various system processes. This file involves the following actions: the Start menu, launching the context menu, action center, Cortana, file explorer, etc.
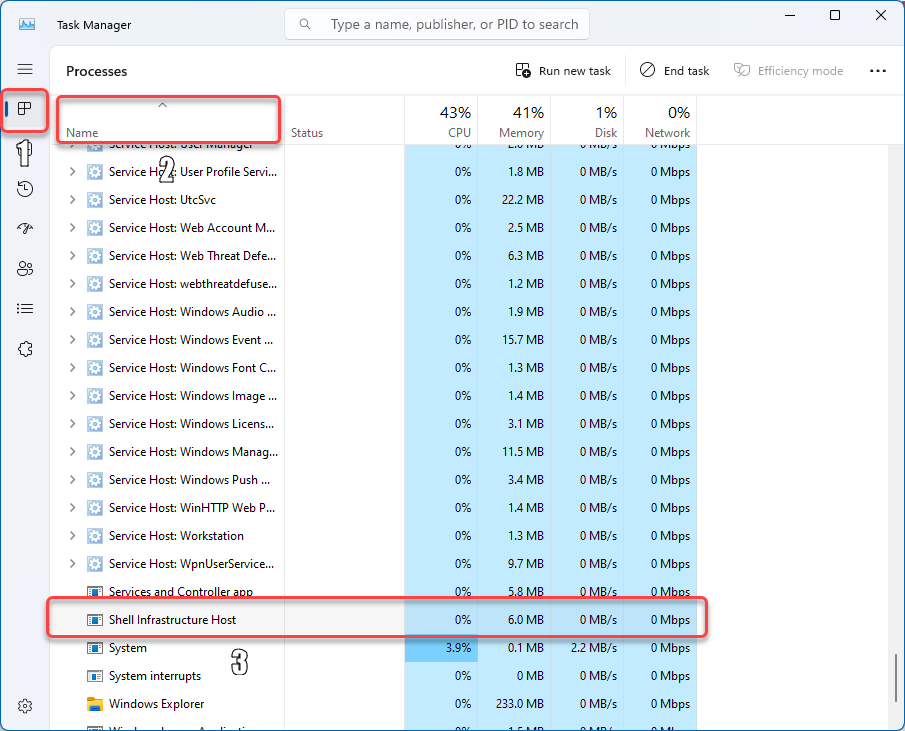
It is essential to understand that Sihost.exe is not a virus. It is a legitimate system process, which you should not stop or delete due to its importance to the system’s stability. However, its name nonetheless can be used by malware, to get a better disguise in the system. You can observe this file in Task Manager in the list of Windows processes. To do this, launch Task Manager, go to the “processes” tab, sort them by name, and scroll down to the “Windows processes” section. Then scroll down some more, and you will see “Shell Infrastructure Host“. In a normal state, this process does not load the system in any way and uses about 6 MB of RAM and miserable amounts of CPU.
Is Sihost Malware?
As I wrote above, malware sometimes masquerades as a legitimate Windows process, using the name of Sihost.exe in particular situations. However, even a legitimate file may consume more resources in some specific cases.
Checking Sihost.exe Location & Properties
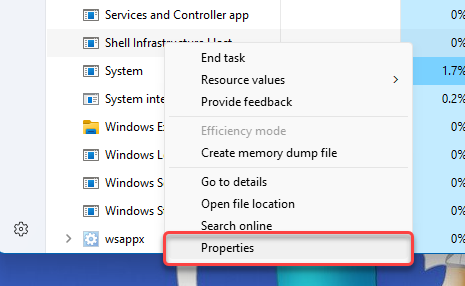
To ensure the process is legitimate, let’s review the sihost.exe instance. First, check its properties through the Task Manager. For this, click with the right mouse button and opt for “Properties.”
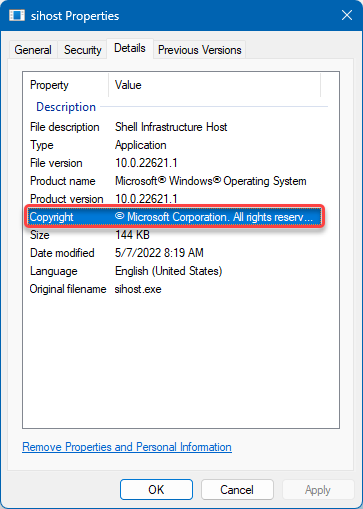
There, click on the “Details” tab and ensure it says Microsoft Corporation before copyright.
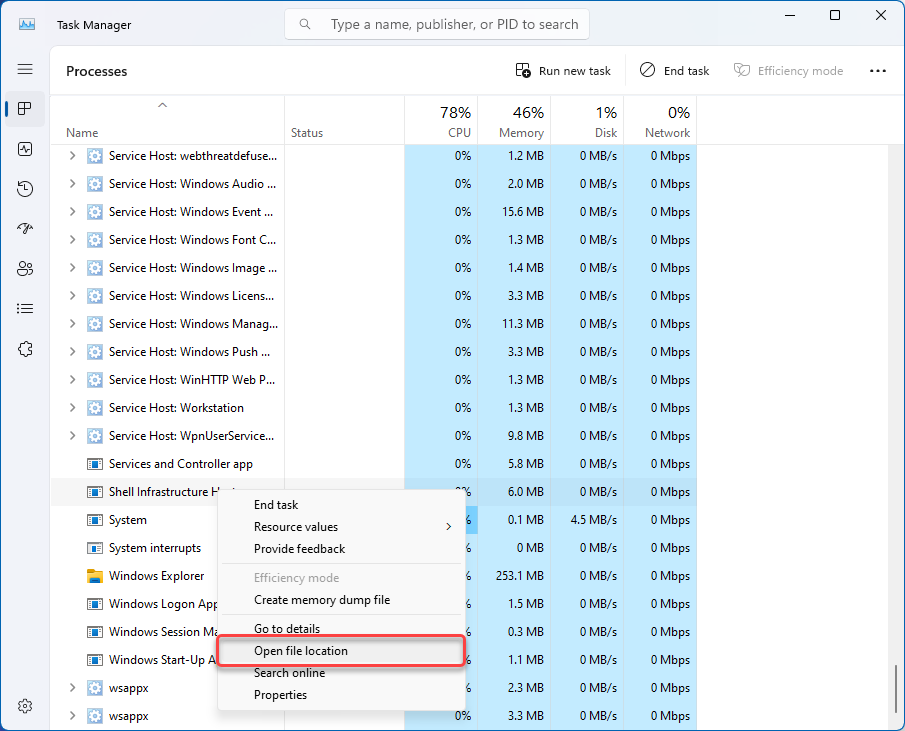
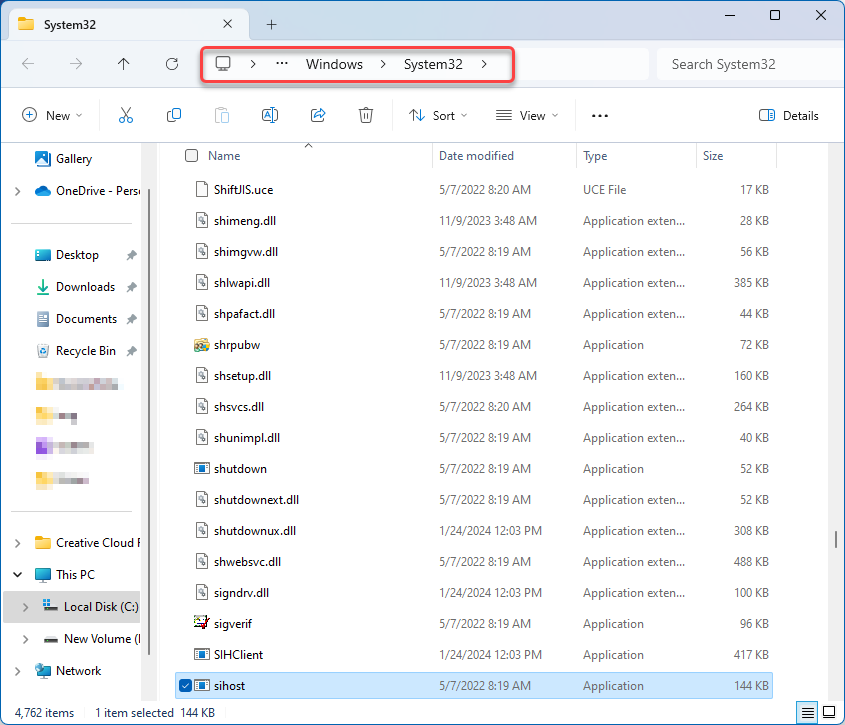
The next step is to look at the sihost.exe location. Close the previous file properties window, right-click on the process, and select “Open File Location.”
By default, the file is located at C:\Windows\System32\. If the file location differs, there is a chance that the name of Sihost is used by malware. We recommend scanning your computer with GridinSoft Anti-Malware.
Fix Sihost.exe High CPU Usage
Suppose your file is legitimate after running the tests but consumes an abnormally high amount of resources. In that case, you can perform the following steps:
Reboot your PC. This is an obvious and trivial tip, but it solves a lot of problems. If the problem hasn’t gone away after rebooting or reappears after a while, move on to the next step.
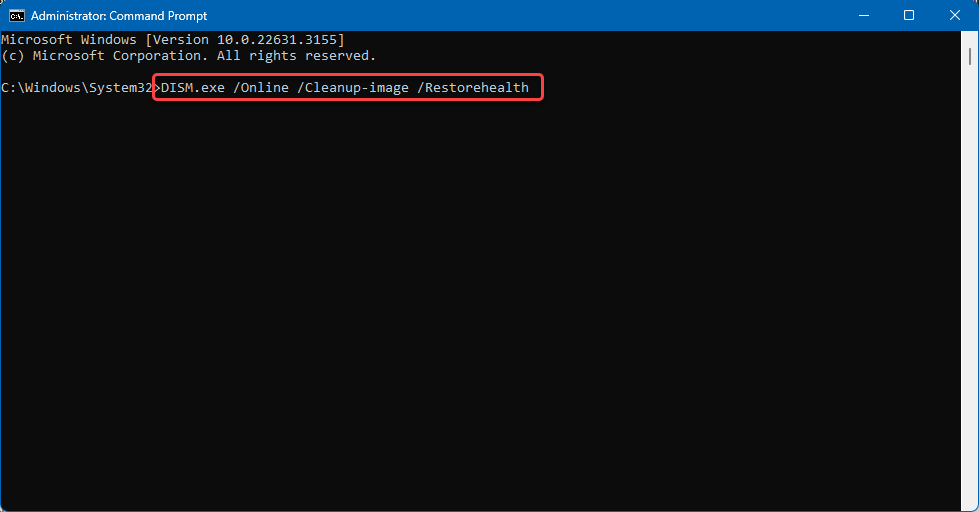
Run the System File Checker tool (SFC.exe). Some user or software actions can adversely affect system files. Restoring important system files should solve such problems. To do this, open Start and write “cmd,” then click “Run as administrator.” Next, paste “DISM.exe /Online /Cleanup-image /Restorehealth” into the command prompt window. If necessary, this action will check your system files and download them from the Windows Update Center.
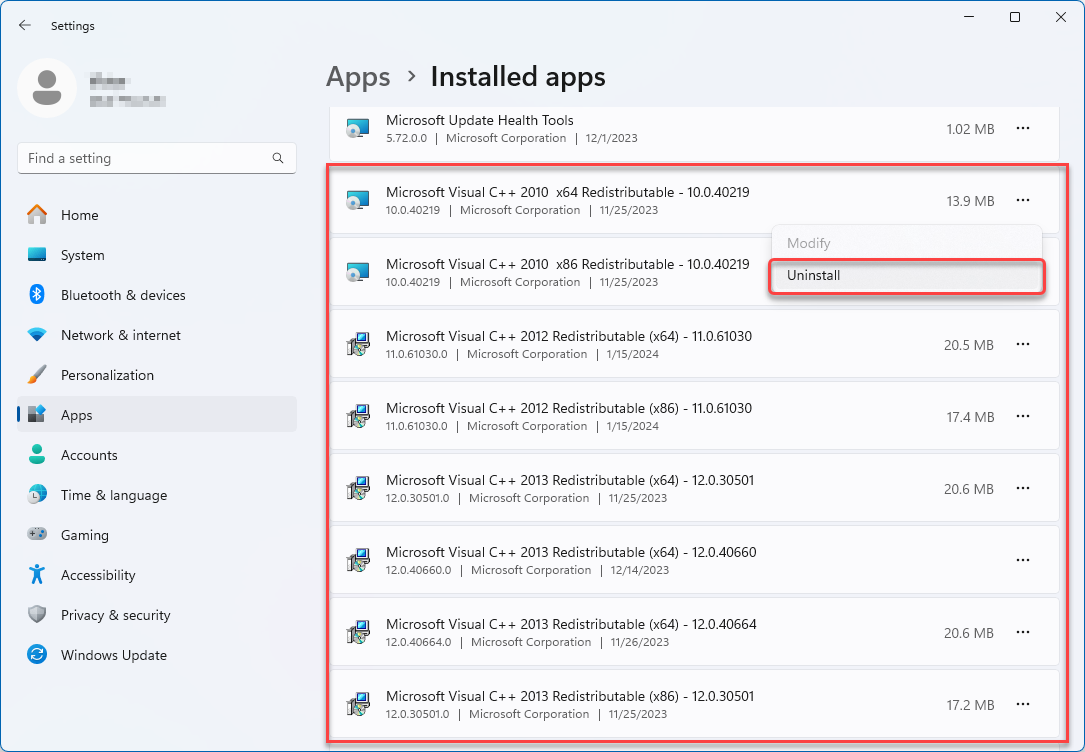
Reinstall Microsoft Redistributable Packages. These packages are necessary for some programs to work, but they can cause the Shell Infrastructure Host to become unstable. To do this, uninstall all installed packages, download the installation file from the Microsoft website, and reinstall it.
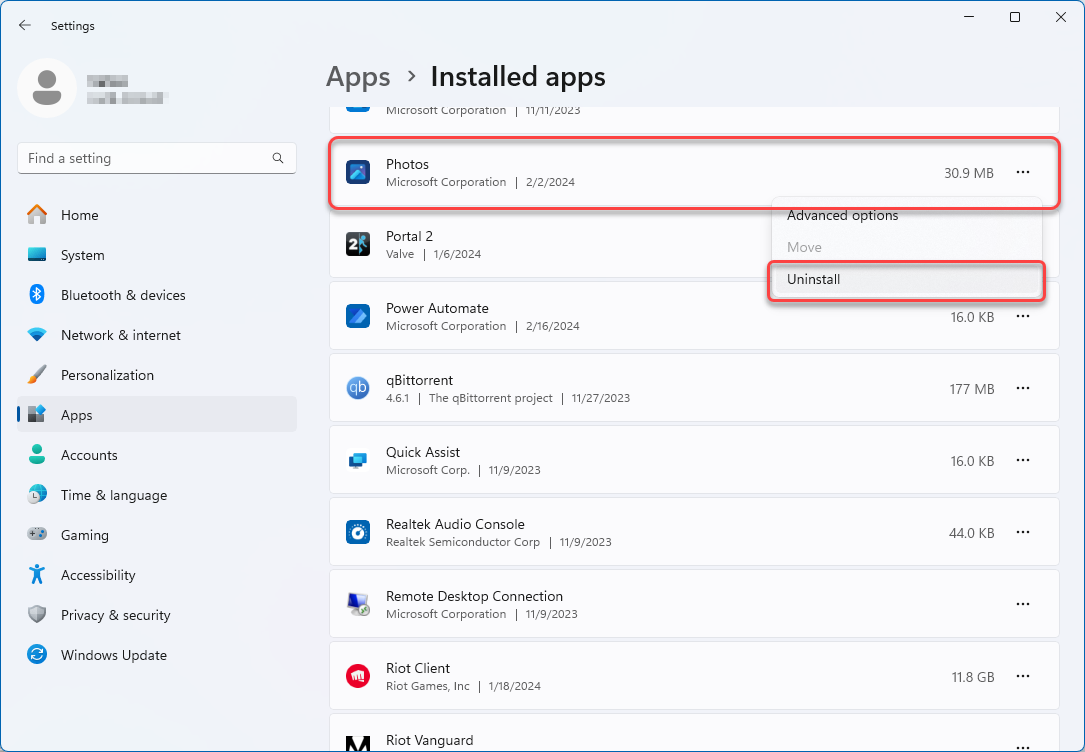
Reinstall the Photos app. Previously, a memory leak bug caused the excessive resource usage of Sihost. You can follow these steps if you encounter the same problem on your computer. First, uninstall the Photos app from your device. Then, open the Microsoft Store and download the app again. This should resolve the issue.
If the above steps do not solve the situation, I recommend running a malware scan on your system. To do this, download Gridinsoft Anti-Malware and run the scan.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.