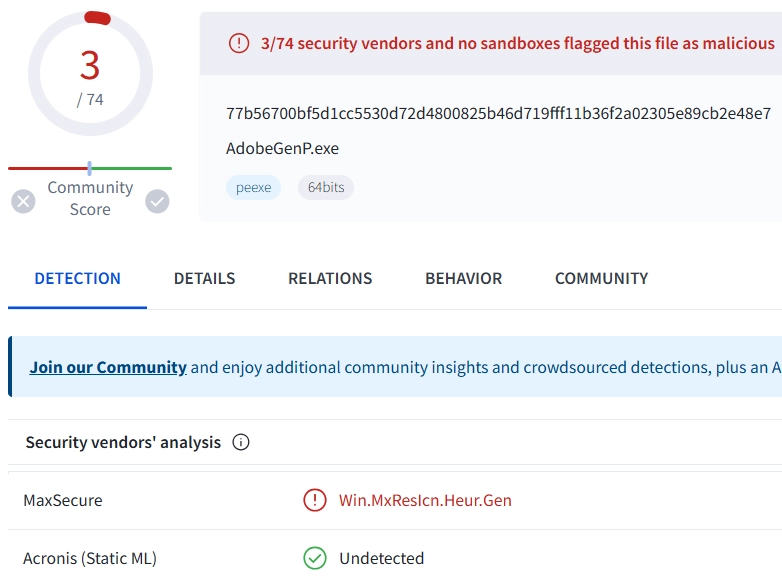
Antivirus engine of MaxSecure, a well-known cybersecurity vendor, currently shows massive amounts of false positive detection with the name Win.MxResIcn.Heur.Gen. It touches numerous legitimate and safe programs and is likely an outcome of the issues with the heuristic engine. The developer does not comment on the situation publicly, presumably communicating in support tickets.
Win.MxResIcn.Heur.Gen Detection Flags Legit Programs
The first public complaints about MaxSecure antivirus detecting safe programs as Win.MxResIcn.Heur.Gen appeared around June 14. A huge amount of similar reports followed up. Users say about quite a few programs of different types getting detected. Among them are Brave browser, Process Lasso tool, some mods for Roblox, and even GridinSoft Anti-Malware installer.
By design, Win.MxResIcn.Heur.Gen is a generic name for a detection made with heuristic detection system. That system is supposed to track the behavior of programs, seeking patterns typical for malicious programs. Considering the “true” detections, this specific name normally appears with spyware, backdoors, and remote-access trojans. I suppose it is about the networking activity patterns these malware types share.
However, despite how long heuristic detection systems have been around, they still require confirmation from other detection systems. These days, malware can intentionally mimic legitimate programs by using specific system calls, commands, and network requests, so it may be hard to distinguish between the two. Implementing a preventive rule (“whatever behaves like that is malicious”) may easily lead to a wave of false positives as we can see now.
What should I do?
If you see this detection on VirusTotal after uploading the file that you think is safe, you can just ignore it. It is doubtful that the heuristic engine of MaxSecure knows something that the other 70+ vendors don’t. Whether you feel like helping with fixing this up, consider reporting the issue to the antivirus support. Alternatively, you can report it to the developers of a detected program.
Things are different for the users who run MaxSecure in their systems. To get rid of the constant detection popping up, one needs to add each detected app to the whitelist. This may be tedious, especially when the program goes crazy and detects a good half of the software you have installed.
For that reason, disabling the security solution until the developers fix this issue may be a viable option. But to prevent leaving your system unprotected, I’d recommend installing GridinSoft Anti-Malware instead. This program will be a great substitute for the bugged antivirus, and with the free trial option, you will be able to test all the features of the program right from the start.
Thanks I have scoured the net for useful info on this and left a few comments on YouTube channels in the hope someone would give some feedback.