Microsoft SmartScreen proved to be an effective way of approving the legitimacy of the application – by checking one’s certificate. With time, Microsoft did a lot of work making it more efficient and sustainable to hacking – but that never made even a single mechanism secure from zero-day breaches. A new vulnerability that allows bypassing SmartScreen protection is already in use and touches a huge number of users. How does that work and how to avoid problems? Let’s have a look.
What is Microsoft SmartScreen?
For those who are not familiar with the internal security mechanisms in Windows, Microsoft SmartScreen is a security utility that notifies the user whether the application it tries to run is dangerous. The key way it understands secureness is the application’s digital certificate. The latter should have a valid signature of a company or a developer. The certificate authority (CA) assures the one, so only legit ones will pass through.
Users may notice the SmartScreen work when they launch an app with no certificate, or when the one is outdated. A pop-up appears, warning the user that it may be dangerous to run that thing, and thus SmartScreen banned its immediate execution. Sure, it does not always work perfectly, blocking legit programs that have outdated certificates – that unfortunate occurrence may happen even with well-known developers. Nonetheless, hackers found a way to circumvent that mechanism and make the programs run regardless of the certificate.
New SmartScreen Exploitation Way
Threat actors never sleep, especially when companies whose products they used to exploit start putting spokes in the wheels. Recent changes in Microsoft policy regarding the execution of the files that arrived from the Internet made it troublesome to spread malware in the usual way. In particular, a huge volume of malware that cybercriminals generally delivered through vulnerable macros in MS Office ceased with this change. For that reason, they decided to approach hacking Windows security from a different angle.
The new breach is not having a whole lot of really new concepts. CVE-2023-24880 describes a way to seamlessly run the MSI file with a specifically smurfed signature. It does not feature a valid Authenticode signature, but the malformed one. Under that condition, the SmartScreen will return an error and allow the execution. But as it turns out, this exact spot crooks were exploiting earlier – but with the use of other file types. In November 2022, threat actors associated with Magniber ransomware were using JavaScript files with a signature spoofed in pretty much the same way. That vulnerability, in turn, received an index of CVE-2022-44698.
Explanation of SmartScreen Exploit
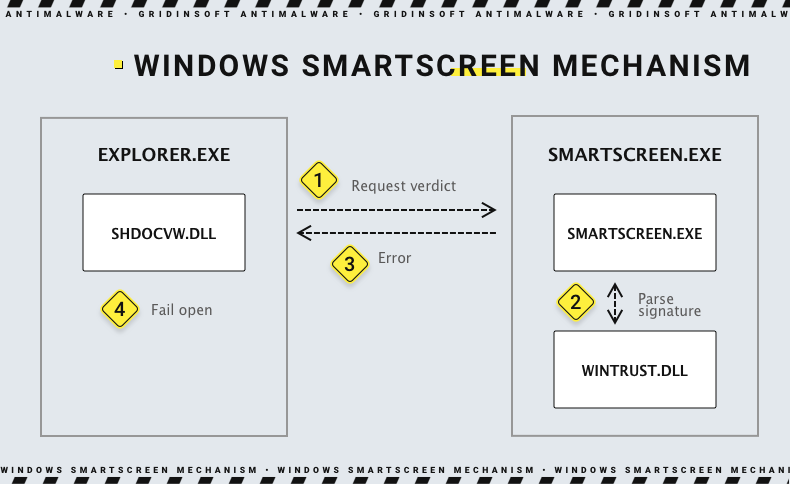
Under the cover, the mechanism of confusing the security mechanisms looks like the following. There are 3 elements in the system that are used to make sure if the program is legit and good to go without the SmartScreen warning. Those are shdocvw.dll, wintrust.dll – a library that helps the SmartScreen to make a decision, and the exact smartscreen.exe.
During the normal checkup, SmartScreen calls for wintrust.dll and requests it to parse the program signature. If everything is OK, the program starts without any warnings. When it’s not, a shdocvw.dll will display a warning window. While working with a specifically spoofed certificate, SmartScreen routinely asks wintrust.dll for verification. That request, however, returns a value that causes smartscreen.exe to send an error message to shdocvw.dll. The latter will fail to start in such conditions, making the program run with no restrictions.
The way they are spoofing certificates hides in the SignedData structure in the file sections. Among other things, it carries certificates that validate the signature and SignedInfo structure. All this info is required for the wintrust.dll to ensure the validity of the signature. To help it navigate through these sections, there is a CERT_CONTEXT structure pointer. Hackers force this pointer to gain a NULL value by giving it a signature that does not contain the SignerInfo serial number. The resulting E_INVALIDARG output goes to shdocvw.dll, making it fail as well. As we already mentioned, this mechanism is identical to the one used in CVE-2022-44698.
Is this vulnerability dangerous?
Obviously, this breach is the one to worry about. As crooks are looking for another way to run malware on the device without triggering alarms, it is obvious that such a thing will be put to use. And the same group of cyber burglars – Magniber – is already using it. They reportedly scored several victims in early spring 2023, using .msi files with a modified certificate. The group used to deploy ransomware to single-user systems since 2018, attacking mostly users from Thailand and South Korea. The signature thing of that ransomware is that a single sample will add a unique signature to the ciphered files. That being said, crooks generate a unique sample for each small group of victims, making the outbreaks hard to track. Another notable thing is the use of vulnerabilities to deploy malware – like the article subject.
Still, nothing stops other cybercriminals from using that breach. Microsoft already released a patch in their March 14 Patch Tuesday (KB5023706), but as it usually happens, users are not hastening to install it. Previous patches that fixed critical vulnerabilities, such as the infamous EternalBlue, for example, are still not installed massively enough to prevent this breach from successful exploitation. And the minor patch that closes not-that-widely-known vulnerability is even less likely to be installed in time.
How to stay secure?
Being secured against modern cyber threats should be a major concern for both home and corporate users. Some measures, especially in corporations, are about to be deployed globally and under the control of system administrators/cybersecurity teams. But there are enough places we can personally tie up the loose thing.
- Avoid launching the files from an untrustworthy source. Programs or files you got somewhere on the Internet, particularly from sites with pirated software or anonymous forums, should be treated with caution. If you cannot avoid interacting with it, try to check the downloaded item with anti-malware software, or using services like VirusTotal. But the best way to have less pain in the neck is to use only official sources.
- Be suspicious of any email you receive. One of the most popular sources of malicious files is spam emails. Sure enough, it may be challenging to distinguish the one, especially when hackers are doing their best to disguise it as legitimate. Still, checking some things, like the sender’s address, and appealing to common sense will make the task much easier.
- Update your software as often as possible. All the software vendors release minor updates not just to annoy you with the “update me” pop-up. Most often, such things contain bug fixes, and what is more important – vulnerability patches. There are several names which products should be taken care of especially well – Adobe, Microsoft, and Oracle. Yet other updates are not about to be ignored either.
- Use top-rated anti-malware software. It is always handy to have something that will solve certain problems for you. Instead of spending time and effort trying to figure out whether the file is malicious or not, you can ask a program to do it for you. Of course, not each one will fit to deal with the threats I was describing above. You need to pick the one which can boast of a multi-component scanning system and the ability to provide on-run protection. I’d recommend you to try out GridinSoft Anti-Malware – it can detect any threat, thanks to the neural network and perfect proactive detection system.