McAfee pop-ups are deceptive push notifications that appear in your Windows notification tray. They often claim that your antivirus subscription is about to expire or that your system is infected with multiple viruses. These messages are scams designed to scare you into making unnecessary purchases. In this article, we’ll explain exactly how these pop-ups work and show you how to stop them.
What are McAfee Pop-ups? Is It Scam?
In their essence, McAfee pop-ups are notifications from malicious websites that aim at making a profit by showing ads. They abuse legitimate browser functionality of push notifications and stem from the permission to send them to the malignant site. You can encounter dozens of different variations of that scam, but this specific one aims specifically at the antivirus theme.

If you click on one of these pop-ups, you’ll be taken to a web page full of clickbait claims—usually saying that your computer is infected with malware or that your antivirus subscription has expired. These scare tactics are designed to make you follow their instructions and download the suggested antivirus software. However, despite using a well-known brand name, the site may actually give you an installer for a completely different program.
It’s also important to note that some McAfee pop-ups may direct you to official McAfee download or payment pages, rather than completely fake sites. While this reduces the likelihood of installing malicious or unwanted software, these tactics are still deceptive. In many cases, dishonest advertising affiliates use shady methods to earn commissions from legitimate vendors. Even if you’re taken to a genuine McAfee page initially, these pop-ups can still redirect you elsewhere later—making the entire approach both unethical and illegal.
Exclusions
In rare cases, these push notifications may actually come from a genuine McAfee browser plugin. Such alerts might inform you about expiring subscriptions, discounts, or other legitimate promotions. However, these instances are uncommon. In most cases, the pop-ups you see are actually malicious imitations designed to trick you into downloading unwanted software or paying for unnecessary services.
How to Stop McAfee Pop-ups on Chrome?
There are several ways to stop McAfee pop-ups, most of which involve adjusting your browser settings. While these steps aren’t difficult, you’ll need to know exactly what to change. Below, you’ll find a detailed guide that covers everything from removing unwanted permissions and extensions to scanning your system for malware and other suspicious activity.
Disable Notification Permissions
The primary reason these pop-ups appear is that you’ve accidentally allowed a questionable website to send notifications. Fortunately, revoking that permission isn’t too difficult. By adjusting your browser settings and removing this approval, you’ll take the most direct step toward stopping McAfee pop-ups for good.
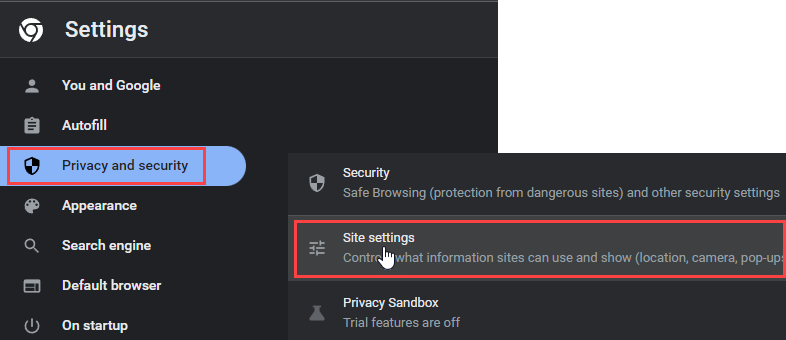
- Click the three vertical dots, then “Settings“. Go to “Privacy and security” ⇢ Site Settings. Alternatively, you can use the search bar to find this menu.
- Select the “Notifications” option. Here, scroll down to the list of sites that can send notifications. This is where the source of the problem resides.
- Delete all the sites from that list. If there are some that you recognize and are willing to keep receiving notifications from, feel free to keep them enabled.
Remove the McAfee Chrome extension
If you have the McAfee extension in your browser, and suspect it is exactly the reason for the notifications to appear, your way to fix the issue is to delete or stop this extension. Same as in the previous part, it only requires running through a bunch of browser settings.
- Launch the Chrome app. Click the three dots in the top right corner.
- Then select More Tools ⇢ Extensions. Here, turn off the McAfee Extensions button.
- Restart the Chrome app and make sure it’s not running. Or, click the “Remove” button on the McAfee extension to remove it from Chrome.
Can McAfee Antivirus Cause Pop-Ups?
McAfee is a well-known software provider that generally does not rely on intrusive pop-up tactics. While there is a McAfee browser extension that can display notifications, these are typically less aggressive and serve as a form of “safe” marketing. The main McAfee antivirus or VPN apps themselves do not generate pop-ups of this nature.
It’s also common for people who don’t even have McAfee products installed to receive these fake notifications. This is because the pop-ups are often triggered indiscriminately by other malicious sources. In many cases, the root cause is a harmful program running on your system.
How to Stop Fake McAfee Notifications
As mentioned, malware can force fake McAfee pop-ups and redirect you to misleading “Subscription Expired” pages. Adware and browser hijackers are notorious for doing this. They benefit by driving users to unwanted websites, and fake McAfee alerts are just one of their many tricks. To put an end to these scams, a thorough anti-malware scan is necessary to identify and remove the culprit.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.


Could not go on browser; screen filled with the popup.
Thank you very much for instructions on how to get rid of McAfee fake popups, I would have never figured that out for myself. And it was a great learning experience for other things I might run up against.
I’ve uninstalled the McAfee app along with all its additional software programs. I’ve also blocked pop-ups from the McAfee website in both Chrome and Explorer, turned off all notifications on both browsers and my PC, and even used McAfee’s software removal tool, but the pop-ups still persist. Despite trying every suggestion from Reddit threads and YouTube videos, nothing has worked. The pop-up keeps asking me to renew my subscription, and there’s no way to exit it. It appears in the middle of my screen, blocking everything, and I can’t move it. I have to click the renew button multiple times just to get to a screen with an “x” to close it. I’ve tried talking to the chatbot here, but it’s useless. When I call Microsoft tech support, I can’t reach a person – I’m constantly redirected to this website by the AI on the phone, which is absolutely no help.