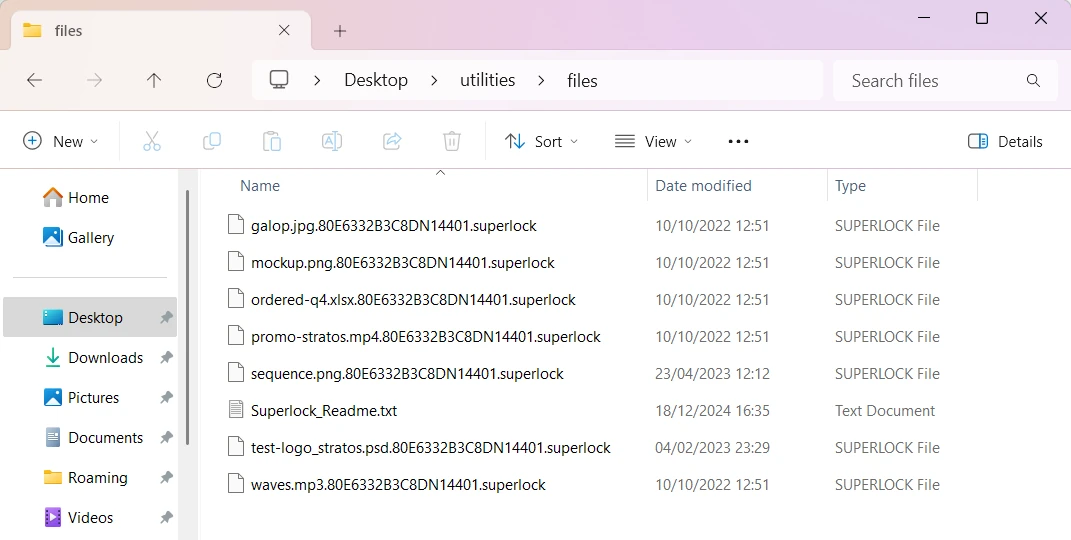
SUPERLOCK is a ransomware infection that aims at blocking access to the files and demanding a payment for getting them back. Users can distinguish the encrypted files by them containing an additional .superlock extension, and also a lengthy ID code. As the result, the file originally named document.docx starts looking like document.docx.80E6332B3C8DN14401.superlock
This malware is led by an elaborate network of cybercriminals, who develop and spread the malware, and then collect ransom payments. In every folder that contains the encrypted files, this virus leaves a text note titled “Superlock_Readme.txt”, which contains instructions on how to contact the criminals.
Ransomware Note Overview
Ransom note of the ransomware contains only basic information about what has happened and how the user can contact the hackers. It says nothing about the sum of the ransom payment, suggesting that it is to be discussed during the negotiations over the email that the fraudsters have specified, [email protected] or [email protected].
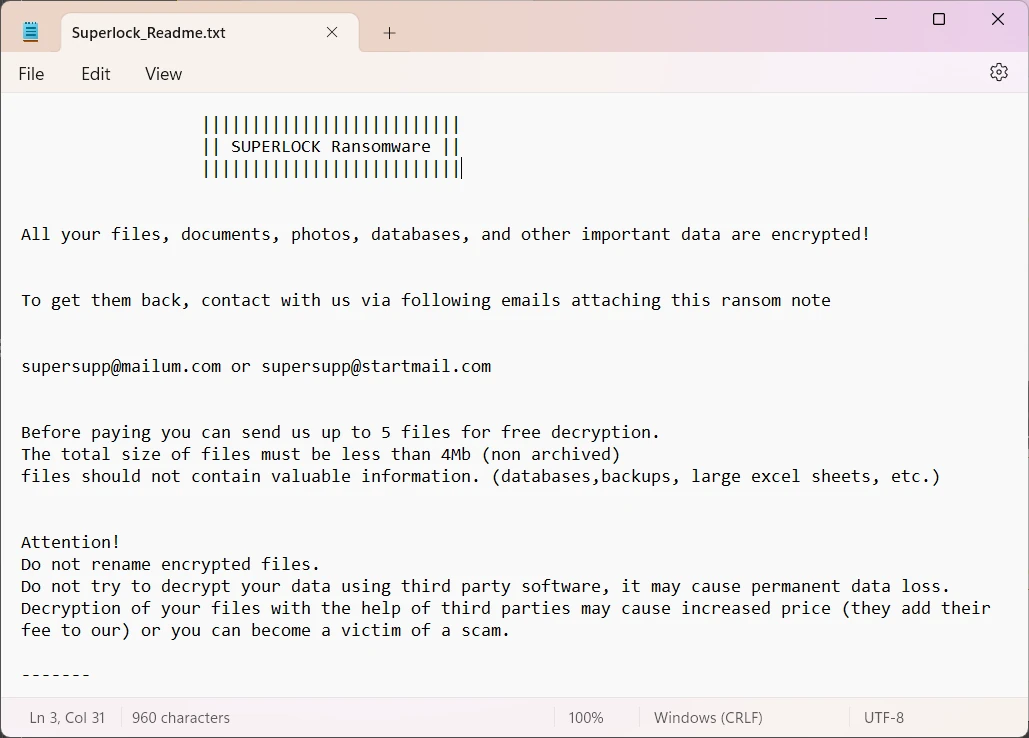
Aside from the contact info, the message also features victim ID, and a public key used in the process of encryption. This information is required for hackers to provide the user with the decryption key, and what they write is true – changing even a single symbol of it will make hacker services useless.
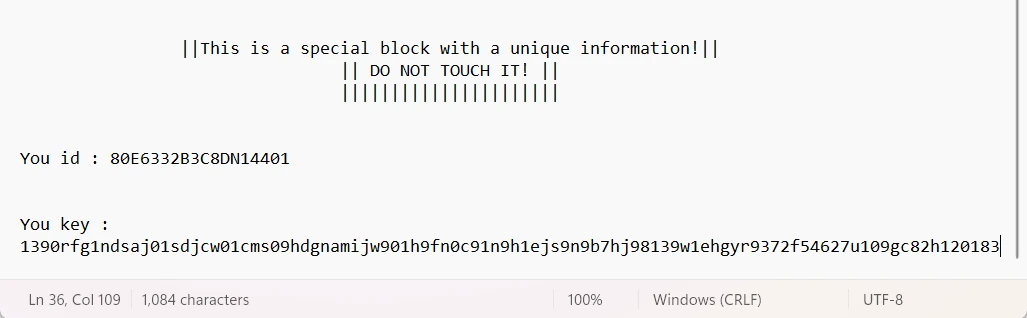
Cybercriminals also offer the victim to try decrypting up to 5 files for free – a generous step to prove they really have a working decryption tool. As the note specifies, the files should not be over 4 megabytes large, and not containing any sensitive information. Such a tactic encourages the victims to pay the hackers for the decryptor.
I would nonetheless emphasize that you should never pay the ransom. Paying the frauds motivates them to keep doing their malicious work, encrypting more and more machines. There are possibilities to get the files back for free, and without sponsoring the future ransomware attacks.
What is SUPERLOCK Virus?
SUPERLOCK is a ransomware-type infection, a type of malware that encrypts the files on the attacked computer and instructs the user on how to pay for getting the files back. It uses quite strong encryption mechanisms that makes the attempts of brute force decryption nearly useless. This, however, does not mean that you cannot recover your files – we will talk about this matter below.
Before the encryption, this virus also modifies a selection of system settings, primarily ones responsible for security and file protection. This is what allows the ransomware to stay undetected by built-in security solutions. To mark the encrypted files, the malware adds its extension to them, and also appends the user ID before it. You can see the example of a folder with encrypted files below.
Once the encryption is over, the malware remains active, which is a major issue. Users may think that the worst part is already over, and start using their system as usual or try recovering their files. But the malware will encrypt these newly introduced files, too. That is why one should remove the ransomware before moving on to recover the files.
How to Remove Ransomware?
To find and remove SUPERLOCK ransomware, I recommend using GridinSoft Anti-Malware. This program will quickly find and delete any malicious files, regardless of the changes they made to the system. Download it by clicking the banner below and run a Full scan – this way, the program will check the entirety of the system, down to the most remote folders and configuration files.
How to Decrypt & Recover Encrypted Superlock Files?
At the moment, there are no decryption tools available for this ransomware. Anyone who pretends to provide such services is either a scammer, or a representative of ransomware actors that tries to make the users pay more often. That is why you should avoid their services, regardless of how realistic their promises may sound. However, there are options that allow for recovering the files without the recovery.
One of the main hopes for people is ransomware activity getting disrupted by law enforcement and cybersecurity researchers. Through arrests of key members, the police can obtain decryption keys for the victims, which they will further make accessible for free. The researchers, on the other hand, may find a flaw in the encryption mechanism that the malware uses, and elaborate a decryptor tool which, once again, will remove the encryption for free. Patience is the key here.
Meanwhile, you can seek for the unencrypted versions of the files you need in various online places you may have uploaded them to. Even if you find an outdated version of your project, that will be much better than having nothing at all. Cloud storages, email messages and even social media may contain your files – do not ignore such an opportunity.
There is also a possibility of this malware using a specific file handling sequence that may allow file recovery tools to be useful for getting the files back to the pre-encryption state. You can try running any file recovery utility of your choice – they will fit equally well, with the general criteria being the support for recovering as many file formats as possible.