Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search engine results. Ads up there are called to make it easier to find users interested in specific queries, but it ended up being yet another object of hackers’ exploitation. Let’s see why these links appear, how dangerous they are, and how you can protect yourself.
What is malvertising in Google Search?
First, let’s check out key definitions, as they may be unfamiliar to some users. Malvertising is a shortening from “malicious advertising”, which says for itself pretty well. Ads in Google Search, on the other hand, are trusted, as they carry the name of the biggest search engine. Days before, they proved to have a robust check-up mechanism that weeded out potentially harmful things from search results. Things have changed around the last few months, exactly, in November 2022. Malicious ads that tried to mimic downloading pages of legitimate tools filled the search results, often dumping the genuine page to the 4-5th position in results.
As Microsoft tightens loose ends and macro-based malware droppers become more difficult for Threat Actors to leverage – data traffickers are increasingly abusing SEO poisoning and/or malvertising.
Intel via @malwrhunterteam & @wdormann pic.twitter.com/iKy7yEN3g2
— vx-underground (@vxunderground) January 18, 2023
These links generally try to fake not only the header of a page but also the URL address. They include the name of a program, and a couple of keywords to look legitimate. Words may be added through a dash symbol, or as a second-level domain. The top-level domain, meanwhile, is usually something cheap, like .click or .top. Such TLDs cost around a dollar, and usually require no documents to register. More expensive domains, like a classic .com, may be used as well, so don’t accept them as a quality mark.
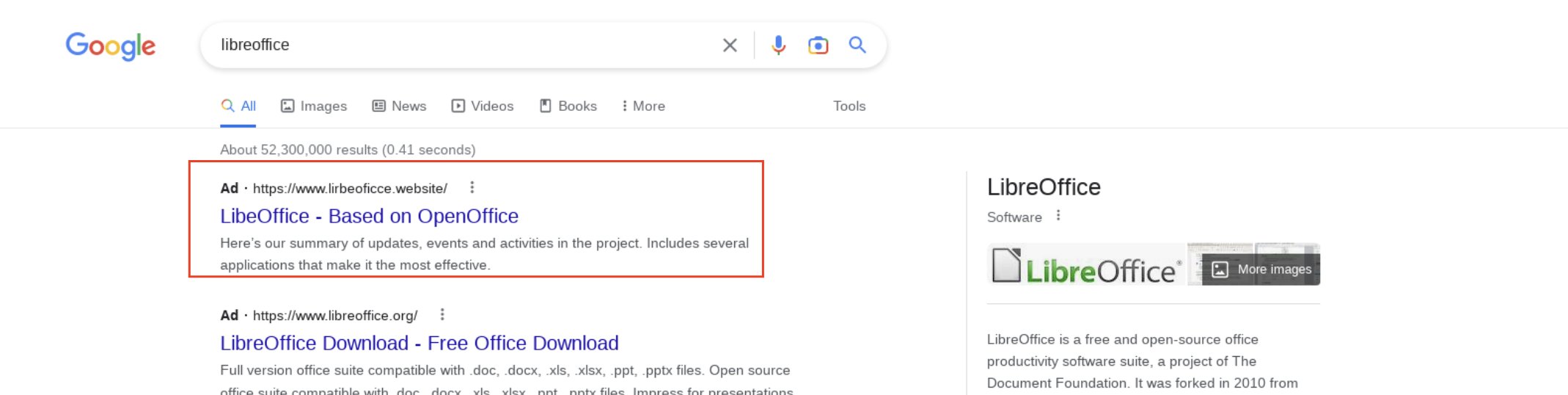
Some fake advertisements may include a so-called domain cloaking. The starting URL will be 100% legitimate, like youtube.com or twitter.com. Once you click, a cloaking mechanism will trigger, and throw you to a site that is completely different from the one you were seeing in the URL bar. This approach is more about tricking people into calling fake support or installing “a recommended security tool”.
Generally, malicious ads appear on search queries related to popular free programs. By now I found malicious ads for the following programs and software packages:
- Blender
- VLC Player
- Oracle VM VirtualBox
- Notepad ++
- LibreOffice
- Capcut
- OBS Studio
- CCleaner
- WinRAR
- Rufus
- Adobe products
- Zoom Video
- AMD and nVidia drivers
- Python libraries
Why do they appear?
First and foremost reason for the appearance of these ads is poor control of advertising content by Google. Sure, the company is not a vice squad, and should not retain the utterly high quality of advertising. But it is subpar for the image of such a company to allow purely fake ads to be posted, especially at top search result positions. Some time before, the same “pandemic” happened on YouTube. Massive amounts of copy-paste scam charity fund advertisements, giveaways, fake promotions of a new iPhone/Samsung with 80% discount – they were not just of low quality or unconvincing. All these things point to some serious problems within Google’s team that is in order for reviewing advertisements to post.
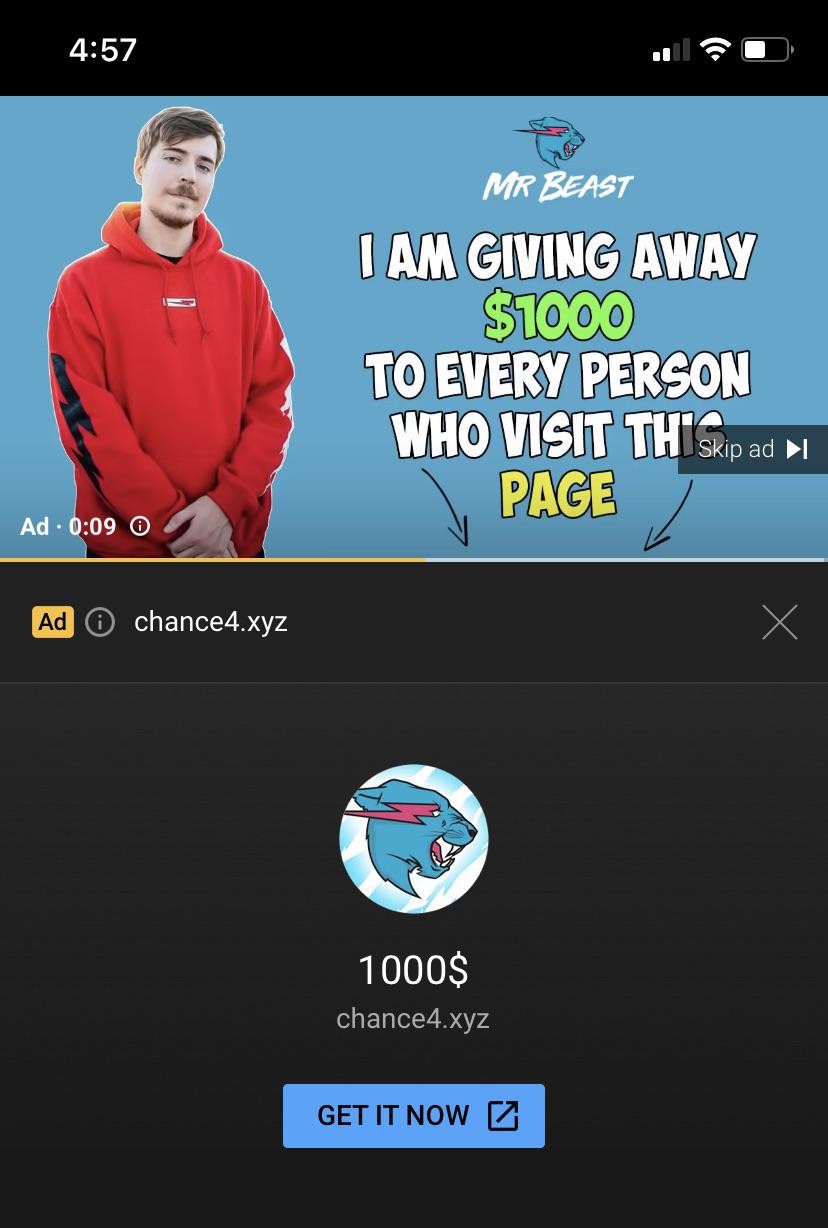
Another side of the coin is scoundrels who actually organise this mess. Most of the time, events of this sort are aimed at spreading malware. The more such methods are available, the more sustainable the hackers’ “business”. At the edge of 2022, Microsoft finally banned the execution of macros that come from the Internet. Macros are MS Office applets that allow dynamically-updated content to the documents. The breaches in the mechanism used to handle them are so easy to exploit that hackers were using it massively to drop the malware payload. After that ban, crooks started searching for another remedy for their shady deeds. And Google Search ads happened on their way.
Is Google Search malvertising dangerous?
Google has immense user coverage. With over 8 billion queries a day, it makes search results probably one of the biggest advertising networks under the sun. One malicious ad may be seen by millions, and thousands will click it. When there are at least 10 topics that contain malicious Google ads – things go worse by orders of magnitude.
Last night my entire digital livelihood was violated.
Every account connected to me both personally and professionally was hacked and used to hurt others.
Less importantly, I lost a life changing amount of my net worth
— Alex Finn (@AlexFinnX) January 15, 2023
Above you may see a sad story of a Twitter user with the nickname NFT God, who got some serious damage after being baited to download OBS Studio via such a fake link.
As research shows, most of the time malware that is delivered after following that link aims at stealing data. The file you are offered to download is not malware itself, it is a malignant script whose sole purpose is to contact the C&C server. It, in turn, sends malware to your device, using a connection that the script has established. Spyware that arrives in such a way will give no chance to your privacy. Ransomware is yet another malware type that may arrive through such an approach.
Other possible instances of Google Search malvertising contain tech support scam offers. That is the case when a group of rascals imposes legit tech support. They usually take the name of Microsoft, and the banners usually contain “urgent security note from Microsoft”. Such a note says your PC is either blocked or flooded with malware, and you need to contact their “support” urgently. The number posted on the banner leads you to a scam tech support that will force you to either give remote access to your PC or install a questionable program “to clean the system”.
How to protect me from Google Search malvertising?
Google used to pay a lot of attention to its ads. Possibly, it just has some problems with retaining concentration, thus the problem will be fixed pretty quickly. But it is always better to hope for the best and be ready for the worst.
- Avoid advertisements in Google Search. Even if you see them having a link to a legit site, it is not always representative of where it will send you. When the top search results consist generally of ads, scroll down to find the links to genuine pages.
- Use a different search engine. Being the biggest search engine does not always mean having outstanding search results. Some people prefer DuckDuckGo because of its claims about being free of tracking and telemetry. However, it may fit the case of fishy ads in Google Search as well. You are free to try any of the ones present on the market.
- Apply using decent anti-malware software. Only by having a tool that can effectively say if the file you’ve got from the Internet is clear or malicious will you be sure about your actions. Having one which is able to block access to malicious sites will seriously mitigate the problem. GridinSoft Anti-Malware is the one that can fulfill both needs – malware detection and network security. Constant database updates allow it to retain efficiency even against the latest threats.