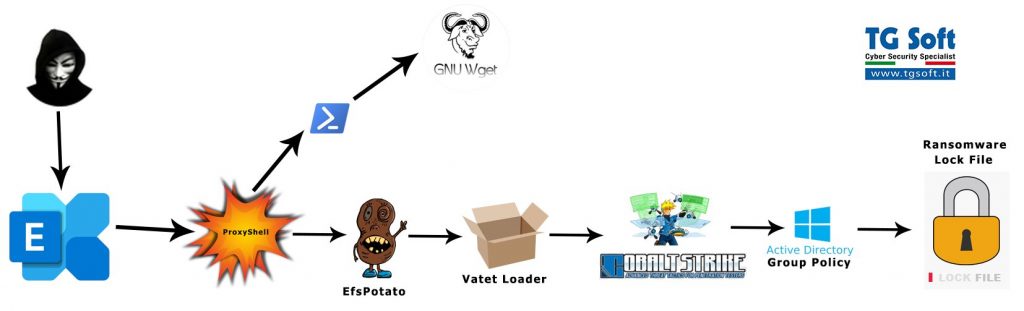
The new LockFile ransomware exploits recently discovered ProxyShell and PetitPotam vulnerabilities to increase its chances of hacking and encrypting corporate networks.
Experts from TG Soft and well-known information security researcher Kevin Beaumont reported about the new threat. They write that LockFile operators are using recently discovered vulnerabilities, collectively known as ProxyShell, to attack Microsoft Exchange servers, from where the attack eventually spreads to the internal networks of companies.
According to Symantec, after infiltrating the victim’s network, LockFile exploits another recent vulnerability, PetitPotam, to take control of the company’s domain controller, and then deploy payloads to encrypt the data on all available workstations.
Symantec writes that the hack group has already attacked at least ten organizations, most of which are located in the United States and Asia. Organizations from the following sectors have already become victims of hackers: financial services, manufacturing, mechanical engineering, law, business services, travel and tourism.
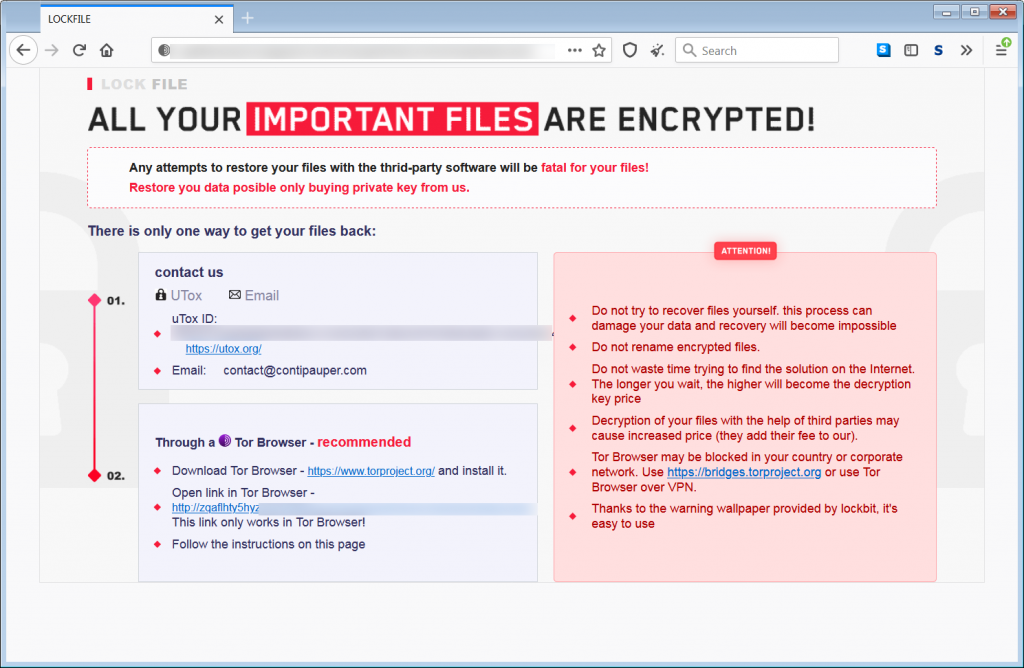
At the same time, experts note the similarity of the ransom notes that LockFile leaves behind with the notes that the LockBit ransomware used.
In addition, the hackers’ contact email hints at a possible connection with the Conti ransomware: contact @contipauper[.]com. Bleeping Computer recalls that recently one of Conti’s disgruntled partners has leaked manuals and technical manuals used by hackers to train their accomplices. Journalists believe that the appearance of LockFile may be associated with this person.
Let me also remind you that I recently talked about how Over 2000 Exchange Servers Hacked Using ProxyShell Exploit.