WordPress has rolled out version 6.4.2, addressing a critical remote code execution (RCE) vulnerability. Discovered by the project’s security team, the vulnerability could potentially be exploited by threat actors to execute arbitrary PHP code on vulnerable websites. WordPress, a widely used open-source content management system, currently powers over 800 million sites, constituting approximately 45% of the total websites on the internet.
WordPress RCE Vulnerability Fixed
The WordPress security team advises administrators to update to version 6.4.2 promptly, even though the RCE vulnerability isn’t directly exploitable in the core. Manual verification of completed updates is recommended to ensure the patch’s successful installation.
In light of the vulnerability, security companies, including Wordfence and Patchstack, offer guidance to users and developers. Wordfence advises users to manually check and update their WordPress sites to the latest version. Additionally, developers are encouraged to replace function calls to “unserialize()” with alternatives such as JSON encoding/decoding using ‘json_encode’ and ‘json_decode’ PHP functions.
WordPress Vulnerability Analysis
The security team identified a Property Oriented Programming (POP) chain vulnerability introduced in WordPress core 6.4. This vulnerability, rooted in the “WP_HTML_Token” class, surfaced in an effort to enhance HTML parsing within the block editor. While not directly exploitable in the core, the security team emphasizes the potential for high severity when combined with specific plugins, particularly in multisite installations.
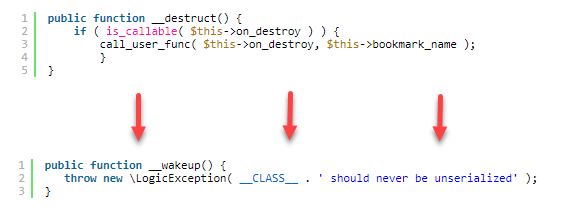
A POP chain relies on an attacker controlling all properties of a deserialized object, achievable through PHP’s “unserialize()” function. Also, the vulnerability exposes the possibility of hijacking the application’s flow by manipulating values sent to magic methods like “__wakeup()”. To exploit this flaw, a PHP object injection vulnerability on the target site is required. It could exist in a plugin or theme add-on.
The new ”__wakeup” method ensures that any serialized object with the WP_HTML_Token class throws an error as soon as it is unserialized. This prevents the ” __destruct” function from executing:
Recommendations
WordPress users are urged to remain vigilant, implement recommended mitigation measures, and follow official channels for the latest updates.
It is highly recommended that you manually check if your site has been updated to WordPress 6.4.2. Even though most sites should automatically update. Also, it is crucial to secure your WordPress site in today’s threat landscape. To protect your digital assets and yourself, staying informed about the latest security updates and best practices is essential.