Today, a smartphone is much more than just a way to reach someone on the phone. Our smartphones contain valuable information, such as private photos, logins, and passwords for online banking. No wonder scammers are trying every way to gain access to our gadgets. Unfortunately, malware developers have mastered mobile platforms and continue to annoy users of mobile devices.
Distribution Methods
Although official app sources such as Google Play and the App Store are considered safe ways to install apps on a device, cybercriminals sometimes use them to spread malware. According to statistics, mobile attacks leveled off after declining in the second half of 2021 and stayed about the same throughout 2022. Nevertheless, fraudsters continue to use Google Play as a means to spread malware. For example, in 2022, Google Play detected several mobile Trojans that covertly signed up victims for paid services.
In addition to the previously known Joker and MobOk families, experts found a new family called Harly. It has been active since 2020, and by 2022 users downloaded Harly malware from Google Play 2.6 million times. In addition, in the past year, scammers distributed fraudulent apps that promised social payments or lucrative energy investments. Another source of malware is in-app ads. Thus, scammers spread a modified WhatsApp build with malicious code inside through advertisements in the Snaptube app and the Vidmate app store.
Some malicious applications masquerade as legitimate utilities. Thus, the Sharkbot banking Trojan downloader is disguised as a fake antivirus. However, this application requests permission to install additional packages and then downloads the files necessary for the Trojan to work on the victim’s device. Fortunately, the intelligence services worked very well to neutralize this threat. That helped Europol to shut down the servers of FluBot (aka Polph or Cabassous), the largest mobile botnet in recent times. However, some downloaders for other families of banking Trojans, such as Sharkbot, Anatsa, Coper, and Xenomorph, could still be found on Google Play.
Another popular vector of mobile malware infection in 2022 is mobile gaming. Attackers distribute malicious and unwanted software under the guise of pirated versions of games or game cheats. These are often Roblox, PUBG, Minecraft, Grand Theft Auto, and FIFA. The primary sources of such malware are unofficial channels, dubious websites, or groups on social networks.
Mobile cyberthreat statistics
According to the statistics, potentially unwanted software such as RiskTool topped the list for 2022. It took 27.39%, displacing adware, which took 24.05%. However, compared to last year, the share of RiskTool and adware decreased by 7.89% and 18.38%, respectively. In third place were other malicious programs, such as Trojans. Their share increased by 6.7 percentage points to 15.56%. As for the geography of mobile threats, the top 10 countries that were attacked by mobile malware are shown below:
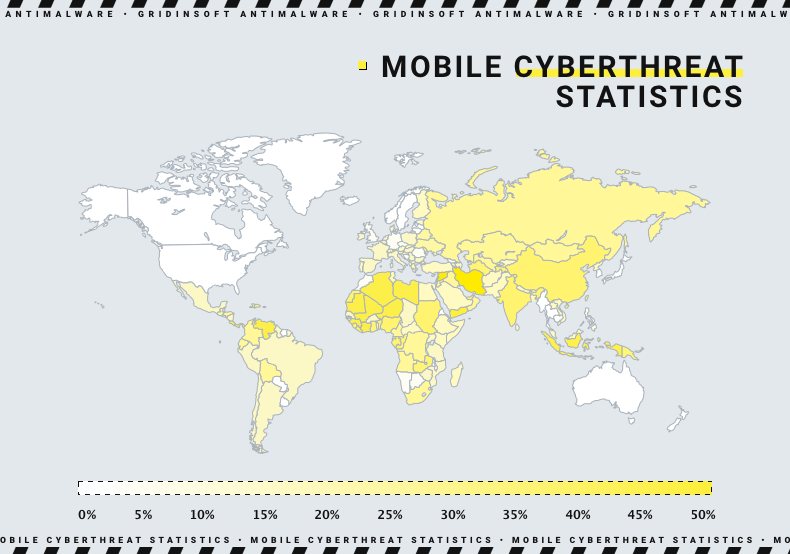
| 1 | China | 17.70 |
| 2 | Syria | 15.61 |
| 3 | Iran | 14.53 |
| 4 | Yemen | 14.39 |
| 5 | Iraq | 8.44 |
| 6 | Saudi Arabia | 6.78 |
| 7 | Kenya | 5.52 |
| 8 | Switzerland | 5.44 |
| 9 | Pakistan | 5.21 |
| 10 | Tanzania | 5.15 |
Chinese users were most affected by the Najin Trojan virus that abused SMS messages. Users from Syria and Iran were most affected by the modification of WhatsApp that contained the spyware module. Similar to previous years, most cyberattacks in 2022 were done through malware, accounting for 67.78%. Meanwhile, compared to 2021, adware infections increased from 16.92% to 26.91%, and RiskWare infections rose from 2.38% to 5.31%.
The most frequently detected mobile malware
Trojan malware bothered users the most. This type of malware was disguised as a legitimate program. It can send text messages, call specified numbers, show ads, and hide its icon on the device. Also, modifications of WhatsApp with a spyware module were quite common, as well as fake apps for supposedly receiving allowances and apps that sign the user up for paid SMS services.
RiskTool apps
The RiskTool family of apps makes payments by sending text messages without notifying the user. Usually, it is a cash transfer to other people or pay for a mobile subscription. Among RiskTool-type apps detected, SMSreg 36.47%, Dnotua 26.19%, and Robtes 24.41% ranked first.
Mobile adware
The Adlo family accounts for the most detected installers in 2022, accounting for 22.07%. These are primarily useless fake apps that download ads. In second place is the Ewind family at 16.46%. In third place is HiddenAd, which accounts for 15.02%.
Mobile banking Trojans
For the year 2022, experts detected 196,476 mobile banking Trojans installers. It’s the highest figure in the past six years and also 100% more than last year. The Bray Trojan family, which mainly attacked users in Japan, accounted for 66.40% of all detected banking Trojans. In second place is the Trojan.Fakecalls family with 8.27% and Bian Banker with 3.25%. Also, of all mobile banking Trojans active in 2022, one of the Bian sub specimen accounts for the largest share of attacked users, more than half in Spain. Saudi Arabia followed it, and Australia came in third place, with the majority of victims encountering Gustuff Banker.
Mobile Ransomware Trojans
Beginning in 2021 and continuing through 2022, mobile ransomware attacks declined. Trojan.pigetrl/lockscreen was the leader, accounting for 75.10% of all mobile ransomware. In addition, it was one of the top 20 most frequently detected types of mobile malware. In second place was trojan.locker/rkor. It can block the screen and demand that users pay a fine for illegal content they allegedly view. The most users attacked by mobile ransomware Trojans in 2022 were in China, Yemen, and Kazakhstan.
Although the number of attacks decreased in 2021, the number of attacks became stable in 2022. Unfortunately, cybercriminals are working to improve both malware functionality and distribution vectors, and malware is increasingly distributed through legitimate channels. Therefore, users need to be vigilant when installing apps and avoid clicking on ad banners even in legitimate apps, as sometimes the app developer does not know what the ads in their app contain.

