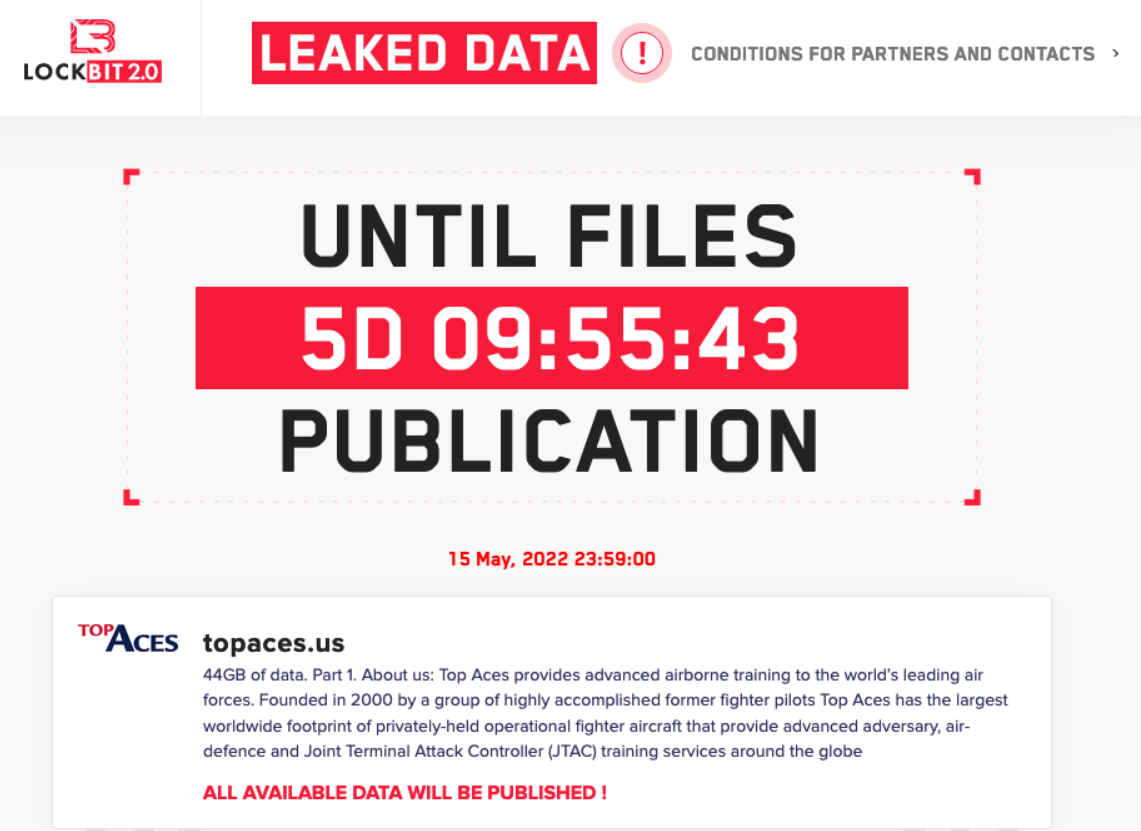
Canadian defense contractor Top Aces Inc became the victim of a ransomware attack. LockBit group, an infamous ransomware gang known for its strict principles, already claimed responsibility. They boasted of it by posting the logotype of this company on their Darknet site.
More details about the Top Aces company
Top Aces Inc is a defense contractor based in Montreal, Quebec. It provides Canadian Airborne Training Services (CATS) with the world’s largest fleet of upgraded fighter jets for Red Air threat replication, JTAC training, munitions drop training, gunnery training airborne and towing maritime targets for the Canadian and German armed forces. The company has an obsolete, but still ready-to-use fleet that fits well for training.
In addition, Top Aces provides electronic warfare training to the Royal Canadian Air Force (RCAF) under the CATS contract, including advanced radar testing in near-combat conditions. Since 2017, Top Aces has also been participating in the training of the Australian Defense Forces, and since 2019 – the US Air Force. The contract with the latter includes training in defense against Russian weapons as a separate item. Possibly, that fact was one of the reasons for the attack – due to the current geopolitical situation.
Top Aces Incorporated was attacked by LockBit Ransomware
Top Aces representatives confirmed the start of an investigation into the incident. Now the company has two days left to solve the problem of the ransom, otherwise, on May 15, 44 GB of exfiltrated data will please the intelligence of all countries. The latter fact worries not only the military, but researchers also express concerns. Among them was Emsisoft analyst Brett Callow, who expressed the growing danger of attacks on companies in the military-industrial complex. The latest of them include the incidents with Visser Precision (a supplier of parts for Lockheed Martin) and Westech International (military contractor in the field of nuclear technologies Minuteman III). Earlier this year, Hensoldt – a multinational military contractor – was attacked by Lorenz ransomware group.
“Even if the individuals behind the attack are simply for-profit cybercriminals, they may sell the data or make it otherwise available to third parties which could potentially include hostile governments” — Brett Callow on the cybersecurity incidents in military companies.
About LockBit ransomware
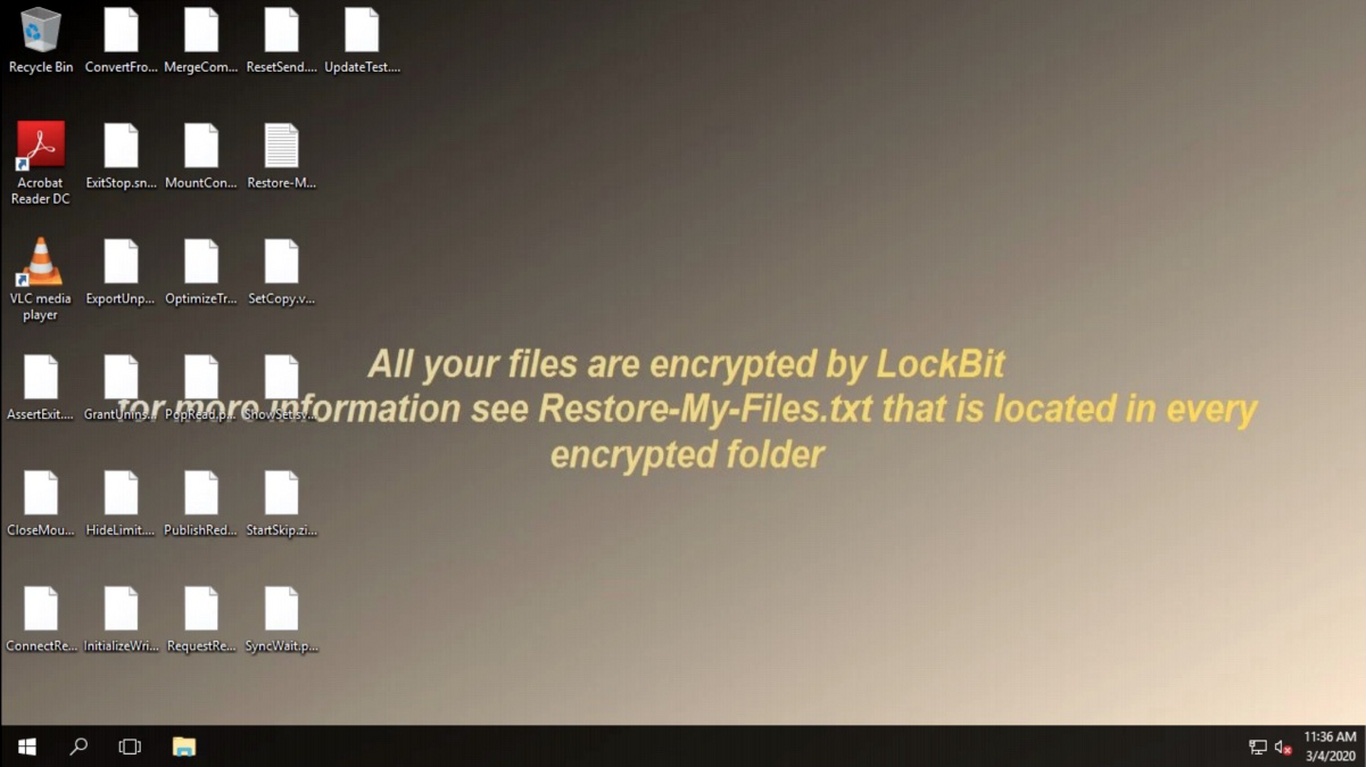
LockBit group is a ransomware gang with supposedly Russian origins. The several interviews that were published on YouTube were in Russian, and in these talks LockBit stands as one of the most moralistic ransomware groups. Despite it being a paradox – moralistic criminals – they really care about their image: there were no registered situations when victims were fooled. Still, being attacked by ransomware is not a pleasant case. Especially with such a superior one – LockBit is famous for one of the most advanced ransomware and stealer modules currently used.
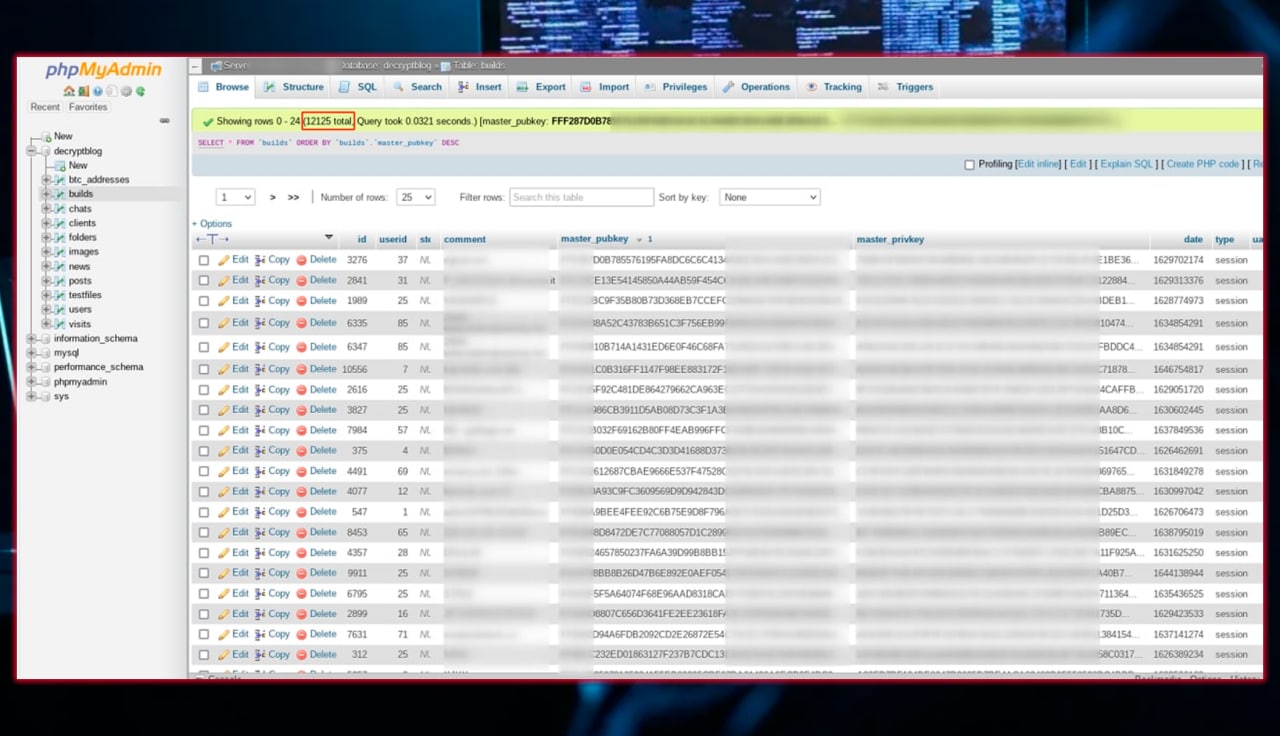
Let us once again emphasize the latent nature of the criminal ransomware industry. According to the recent leaks, the LockBit group recently exposed a screenshot of a panel showing 12,125 companies as victims. Meanwhile, only about 850 companies listed on their Darknet leaks site (DLS). In monetary terms, the aggregate income of the group can be: 12,125 x $100,000 (average ransom) = $1,212,500,000. Impressing sum, isn’t it? LockBit is one of the most wanted cybercrime groups; FBI hunts them for the last two years. However, while their contemporaries – REvil group – already had a meeting with men in uniform, LockBit manages to keep anonymity.