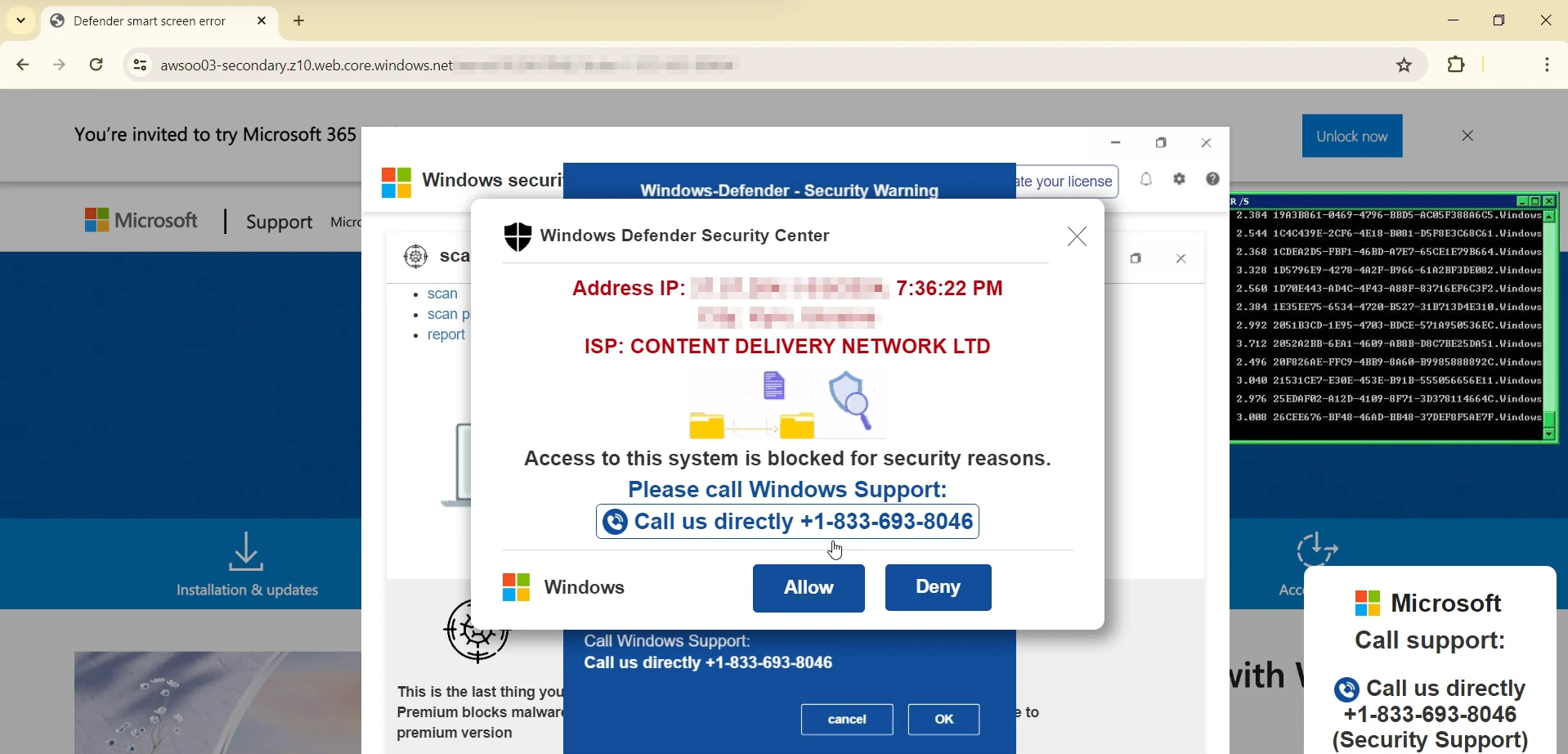
“Windows Defender Security Warning” is a scam website that falsely claims your PC is infected and urges you to contact Microsoft tech support. This scam is part of a larger scheme aimed at deploying unwanted software on users’ devices and extracting money for resolving nonexistent issues. It has been around for some time and targets users worldwide.
Tech support scams represent a particularly notorious type of online fraud, utilizing various tactics to coerce people into making a phone call to a fake support service. The Windows Defender Security Warning scam is one of the most enduring and widespread methods used in these schemes. In this article, I will describe what this scam is, how it operates, and how you can avoid falling victim to it in the future.
What is Windows Defender Security Warning?
As mentioned earlier, the Windows Defender Security Warning typically appears as a browser window after clicking a link on a certain website. It displays numerous smaller windows, which are actually non-interactive images. These fake alerts inform the user that their PC is blocked “for security reasons”. In the background, a robotic voice claims the following:
Clicking on any of the site elements – which in fairness may happen randomly – results in the website switching to a full screen, with no obvious way out. Escape button won’t work, and roaming the mouse around the screen won’t help out either. If the victim is not aware of combinations like Ctrl+F4, Alt+Tab or Ctrl+Shift+Esc, it may look like a trap. That, along with the sound alert, is what should push the user towards following the scam’s guidance and call the support.
As you can see, this is just a scam designed to capitalize on the fear of individuals who may have less knowledge about computer security or computers in general. However, let’s take a closer look at how this scam operates—there are quite a few interesting tactics involved.
Windows Defender Security Warning Mechanism Explained
The scam begins by luring users to the Windows Defender Security Warning page. To achieve this, scammers often purchase link placements on dubious websites, such as those hosting pirated movies. A user clicking on a play button or attempting to skip an ad in the video player may be redirected to the scam site.
The domains hosting this scam can vary widely, but they typically include some mention of Microsoft in the URL. In some egregious instances, fraudsters have even managed to secure hosting from Microsoft themselves. Below, you can find a list of sites used in this scam campaign:
| digitalcompletes[.]online | spicyhotrecipes[.]site | rickyhousing[.]xyz |
| gardenhub[.]site | morningh[.]shop | robortcleaning[.]site |
| jadeneal[.]autos | programmaticcrooks[.]online | elhiuwf[.]cf |
| hitorikawag[.]top | adultfriend[.]store | yeddt[.]jet |
| jonwirch[.]com | aweqaw12d[.]tk | helpadvance[.]ga |
| 333waxonet[.]ml | noblevox[.]com | risingsolutions[.]online |
| pixua[.]com | adultfriend[.]site | giveserendipity[.]website |
| connectflash[.]ml | ondigitalocean[.]app | dothrakiz[.]com |
| jbvhjcbjzvhxvhzcjgzvgcczgh29[.]ml | digitalflawless[.]ga | todogallina[.]es |
| markmoisturise[.]online | enterthecode[.]org | ebonygirlslive[.]com |
Once the user lands on the scam site, it typically goes fullscreen and starts playing the previously mentioned audio message. The main goal of this message is to coerce the victim into contacting “tech support” using the phone number displayed on the site, which is mentioned multiple times. The phone call marks the final phase of the scam.
The so-called support manager begins by instructing the user to download sketchy software purported to resolve the issue—without explaining how the software addresses identity compromise. Throughout the life of this scam, various fraudulent programs have been offered, including SystemKeeper, Driver Updater, and Wise System Mechanic. As expected, all these are pseudo-effective unwanted programs that further prompt users to pay for fixing a myriad of non-existent problems.
What is the purpose of all this, you might ask? Money is the short and universal answer. The fraudsters posing as tech support managers receive commissions for each user they persuade to download the software. Meanwhile, the developers of this software profit from users purchasing licenses. Considering how long this scam has been active, the monetary turnover is quite substantial.
How to Protect Against Windows Defender Security Warning Scam?
The primary advice for protecting against the Windows Defender Security Warning scam and similar schemes is to avoid websites that initiate these scams. As mentioned, the majority of redirects to scam websites originate from pages hosting pirated content. This should be another reason to steer clear of such sites, beyond the fact that content piracy is illegal. Additionally, pirated software or games pose a significant security risk.
Learn how genuine notifications from security software should look, and how they should not. Neither Microsoft Defender nor other antivirus/antimalware programs issue security notifications through web browsers. None of them will prompt you to call support while appearing to block your computer. And, importantly, no legitimate tech support from any security vendor will ever advise you to install questionable third-party software.
Use reliable antivirus software with network protection. To prevent scam pages from opening and to ensure your system remains secure regardless of any fake alerts, a robust antivirus solution is essential. GridinSoft Anti-Malware offers excellent malware removal capabilities and network protection, backed by a multi-component detection system and regular updates.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.
