Recent research uncovers a new anti-EDR utility in the arsenal of malware actors, nicknamed EDRKillShifter. Its main known user to the moment is the RansomHub ransomware gang. Though, it is likely for other threat actors to adopt this tool, as similar utilities have immense popularity among cybercriminals nowadays.
EDRKillShifter Used in Ransomware Attacks
Research team from Sophos did a tremendous job analyzing the new toolkit. Being an element of targeted ransomware attacks, EDRKillShifter employs a lot of detection evasion techniques, as its usage is meant to be among the first attack steps. It is also worth noting that the tool is written in Golang, which appears to be a new trend among malware creators. And it adds for detection evasion, too, thanks to the availability of obfuscation utilities for this specific language.
One of the notable users of this anti-EDR tool is the RansomHub ransomware gang. Appeared in late February 2024, it quickly gained traction, attacking companies in Europe and the US. Nowadays, they are among the most active ransomware groups, claiming attacks on over 80 companies. Similar tools are also used by the LockBit ransomware group, namely the AuKill malware.
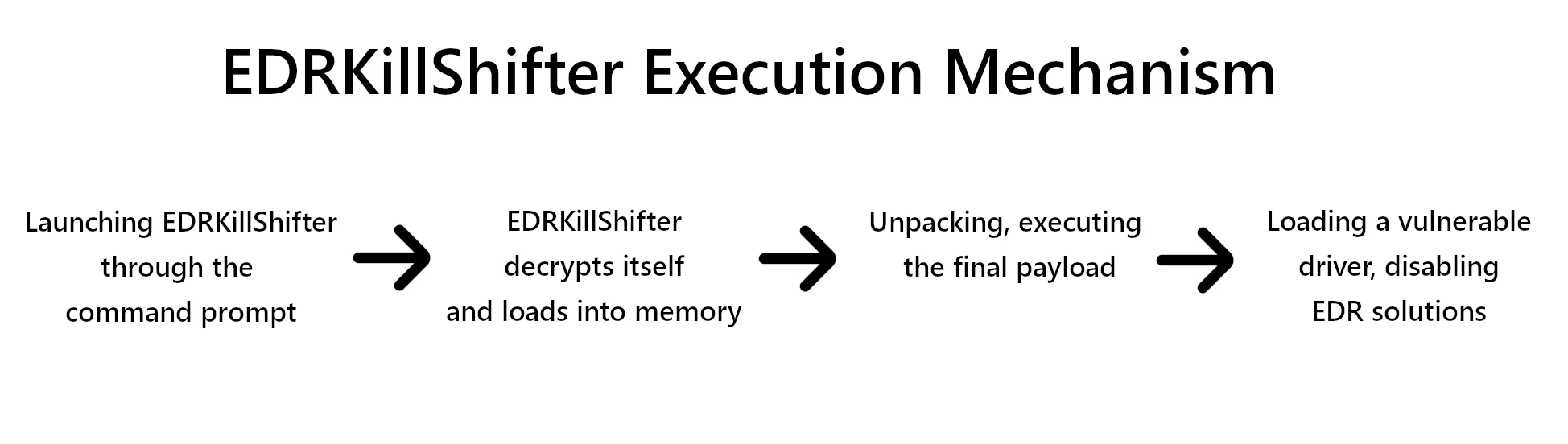
The execution of EDRKillShifter happens in three stages. First one requires direct interaction from adversaries: one should type the correct password when running the malware through the command line. Further steps happen automatically: malicious toolkit decrypts its resources and loads itself into the system memory. After that, the main course of the attack kicks in.
Key trick that this malicious toolkit pulls out is loading the vulnerable driver (BYOVD), which eventually does the main job of disabling EDRs. For this purpose, cybercriminals opt for a legitimate driver that has a known vulnerability. All the signatures and recognition of the latter allow the threat actors to do the trick under the nose of a still-working security solution. The driver allows the EDRKillShifter to methodically go through all the processes running in the environment, disabling ones that match with the hardcoded list.
How effective is EDRKillShifter?
Anti-EDR tools show a rather high efficiency in cyberattacks, and their growing popularity among threat actors confirms this. Disabling the security tool effectively unleashes adversaries in any further actions. EDRKillShifter is also rather hard to detect by itself, due to the obfuscation and BYOVD tactics it uses. Researchers also note that the list of EDR solutions that the toolkit may target is easy to expand. Since it is a hardcoded list, hackers simply add new or substitute older ones – is as easy as it sounds.
Fair enough, it is not the final payload, but it is what makes the deployment of one possible. Security analysts agree on the fact that such attack vectors will expand in future, with even more tricks and possibilities. Fortunately, BYOVD is not a new tactic and security vendors already have ways to detect the abuse.
Darknet Infrastructure of EDR Killer Tools
One more noteworthy thing about EDRKillShifter is the infrastructure built around this and similar toolkits. Obfuscation services and loaders for malware payloads were always a profitable Darknet business. And it applies to this anti-EDR solution, too: the loader that executes the first attack stage appears to be made by a different threat actor. Obfuscation is likely done by the third-party actor, too.
From a certain point of view, this may look like an unnecessary complication and extra costs of the attack. On the other hand, having a whole bunch of elements made by different cybercriminals makes it harder to detect and trace. And this is worth much more than a fee that the ransomware actors pay for all these operations.