Opera GX is a special version of the Opera browser with extra features tailored for gamers. However, malicious, weaponized versions of the browser are circulating online, transforming this legitimate browser into a makeshift malware. In this post, I’ll explain how to tell the original Opera GX apart from modified versions and why these “alternative builds” can be dangerous.
Is Opera GX Malware?
First and foremost, Opera GX is a legitimate, secure browser, a product of Opera Software, headquartered in Norway. Its official website provides the latest safe version for download, and there is nothing wrong with it. This browser was originally created to improve the user experience for gamers. It attracts users with unique features unavailable in the classic Opera version and other browsers.
However, like many popular programs, Opera GX has become a disguise for malware distribution via modified versions found on untrustworthy sites. These versions appear similar to the legitimate one, but include malicious changes scripts that compromise user data and security. Hackers quite literally rewire the browser to act in a way they want.
Spreading approach for these altered versions is rather interesting. Users are lured to fake human verification pages, where they see an offer to run a script or download a file. In either case, the user ends up with the installation file of what looks like Opera GX. But in reality, they install malicious software with their own hands.
The other method involves installing this browser unknowingly as “recommended software,” often bundled with cracked games or programs. Handymen who create those cracked versions deceptively label OperaGX as “author recommended software”. Sometimes they feature normal versions of this browser; we described one of such cases in a dedicated article.
Malicious Activity
To understand what is wrong with the malicious version of Opera GX, let’s examine its behavior. Visually, the malicious installer is identical to the legitimate one, so users won’t notice any difference during installation or even after launch.

The main issue is that once installed, this impostor version of Opera GX begins functioning like spyware. It can read data from other browsers, including passwords, session tokens and cookies. Then, it transfers all the data to the command server – an action that was never present in the normal version.
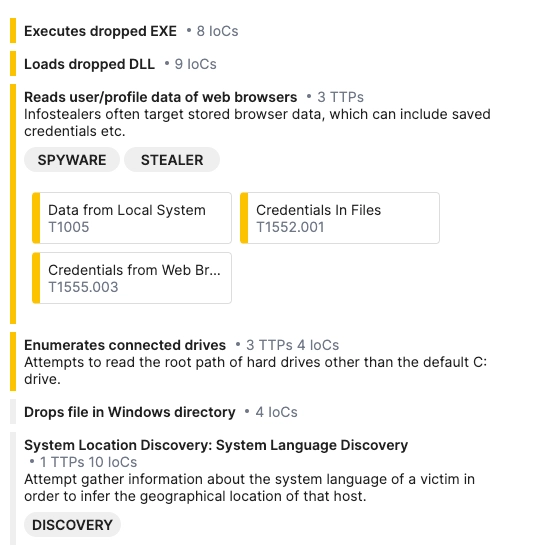
As shown, the most concerning actions occur in the background. Today, nearly all browsers can import data (like passwords) from other installed browsers, but they do so after installation and only with user consent. In our case it happens at the stage of program installation, even before the user sees the browser window for the first time. Such sensitive data may – and will – be used against the user in different attack scenarios.
How to detect and remove a malicious version of Opera GX?
Unfortunately, there is no way to visually determine if a file is malicious. If you downloaded the installer from the official website, it should be safe. However, if Opera GX came from an unknown source, or in a software bundle, that is a definite red flag.
To scan the system for fake software or outright malware, I recommend using GridinSoft Anti-Malware, which is effective in detecting even stealthy threats. To do so, follow the steps below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.