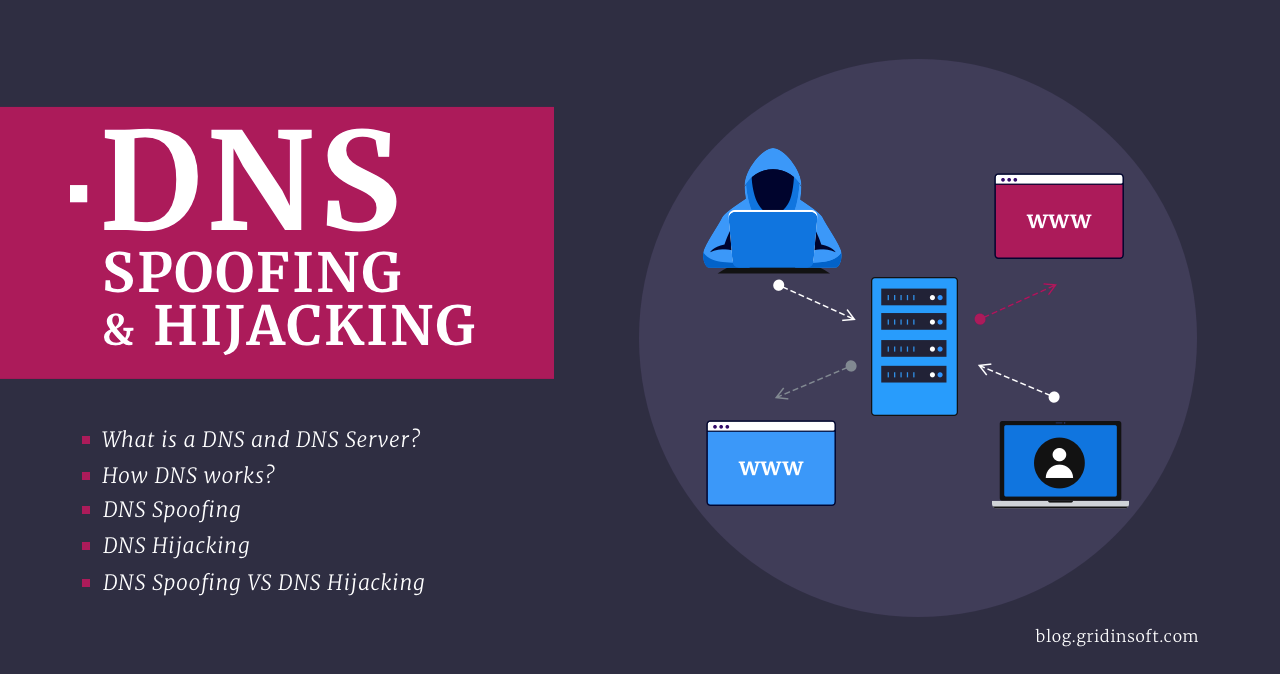
Domain name services are an essential part of our IP network. They are servers that take website names and map them to IP addresses. Suppose you can change the information on the DNS server. In that case, you could potentially send someone to an IP address that doesn’t necessarily match where they think they were… Continue reading DNS Spoofing VS DNS Hijacking
Results for "DNS"
DNS Cache Poisoning and DNS Spoofing
DNS poisoning and spoofing is a cyberattack that exploits vulnerabilities in DNS servers to redirect traffic from legitimate servers to fake ones. Once exposed to a fake page, you may be puzzled about how to fix the problem, even though you’re the only one who can do it. Therefore, you need to know precisely how… Continue reading DNS Cache Poisoning and DNS Spoofing
TOP DNS Attacks Types
What is a DNS (Domain Name Server) Attack? A DNS attack is the situation when an attacker either attempts to compromise a DNS network or uses its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can cause severe damage to an organization. DNS is the main form of communication. It receives domains… Continue reading TOP DNS Attacks Types
DNS Spoofing: Key Facts, Meaning
What is DNS Spoofing? DNS (Domain name server) spoofing or DNS cache poisoning is a type of cyberattack used by an attacker to direct the victim’s traffic to a malicious website (instead of a legal IP address). Attackers use DNS cache poisoning to redirect Internet traffic and steal sensitive information. For example, a hacker wants… Continue reading DNS Spoofing: Key Facts, Meaning
A DNS vulnerability in uClibc/uClibs-ng libraries jeopardizes IoT devices
A vulnerability has been discovered (CVE not yet issued) in uClibc and uClibc-ng C standard libraries. These libraries are vastly used in IoT devices. The newly found vulnerability makes it possible to place forged data into the DNS cache, allowing to set an arbitrary IP address in that cache with the subsequent rerouting of all… Continue reading A DNS vulnerability in uClibc/uClibs-ng libraries jeopardizes IoT devices
Avast experts accidentally got source code for GhostDNS exploit
Avast analysts suddenly got the source codes for the GhostDNS exploit. The experts got access to the source thanks to an error from an unknown hacker. GhostDNS is a set of exploits for routers that uses CSRF queries to change DNS settings and then redirect users to phishing pages (where from victims are stolen credentials… Continue reading Avast experts accidentally got source code for GhostDNS exploit
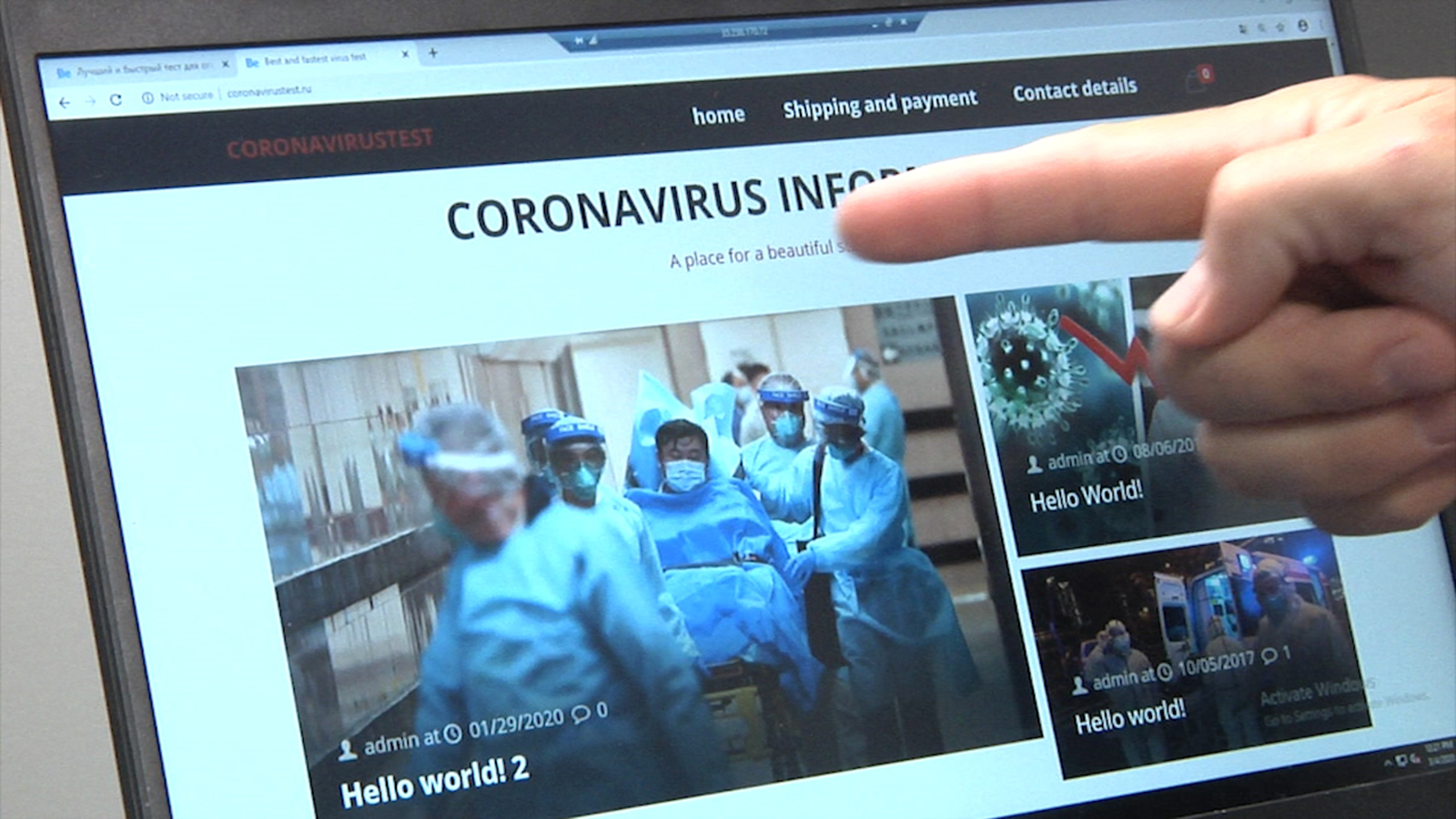
Hackers spoof DNS settings to distribute fake coronavirus applications
Journalists from Bleeping Computer investigated that hackers are replacing DNS settings for distributing fake applications. The reason for the investigation were complaints of users, which reported on the forums that they were obsessively offered to download a strange application, allegedly informing about COVID-19 and created by WHO. As it turned out, the routers of these… Continue reading Hackers spoof DNS settings to distribute fake coronavirus applications
BianLian Exploits TeamCity Vulnerability to Deploy Backdoors
BianLian, a group of cybercriminals known for their ransomware attacks, recently caught the attention of the information security community. By exploiting vulnerabilities in the JetBrains TeamCity platform, they managed to carry out multistage cyberattacks. Threat actors reportedly start their attack chain with a Golang-based backdoor, and work their way all the way to the ransomware… Continue reading BianLian Exploits TeamCity Vulnerability to Deploy Backdoors
9 PixieFail Vulnerabilities Discovered in TianoCore’s EDK II
A chain of 9 vulnerabilities in UEFI’s Preboot Execution Environment (PXE), dubbed PixieFail, was uncovered in a recent research. As the network boot process is a rather novice attack vector, only a few vulnerabilities received high severity status. Nonetheless, their sheer volume, along with the location in rather sensitive places, can create a mess if… Continue reading 9 PixieFail Vulnerabilities Discovered in TianoCore’s EDK II
PUABundler:Win32/CandyOpen Analysis & Removal Guide
PUABundler:Win32/CandyOpen is an unwanted program that acts as a browser hijacker and can download junk apps to your system. Specifically, it points at a thing known as OpenCandy adware, that is known for its indecent behavior. Let’s break it down and see what the PUABundler/Candyopen on a real-world example. What is PUABundler:Win32/CandyOpen? As I’ve said… Continue reading PUABundler:Win32/CandyOpen Analysis & Removal Guide