Journalists from Bleeping Computer investigated that hackers are replacing DNS settings for distributing fake applications.
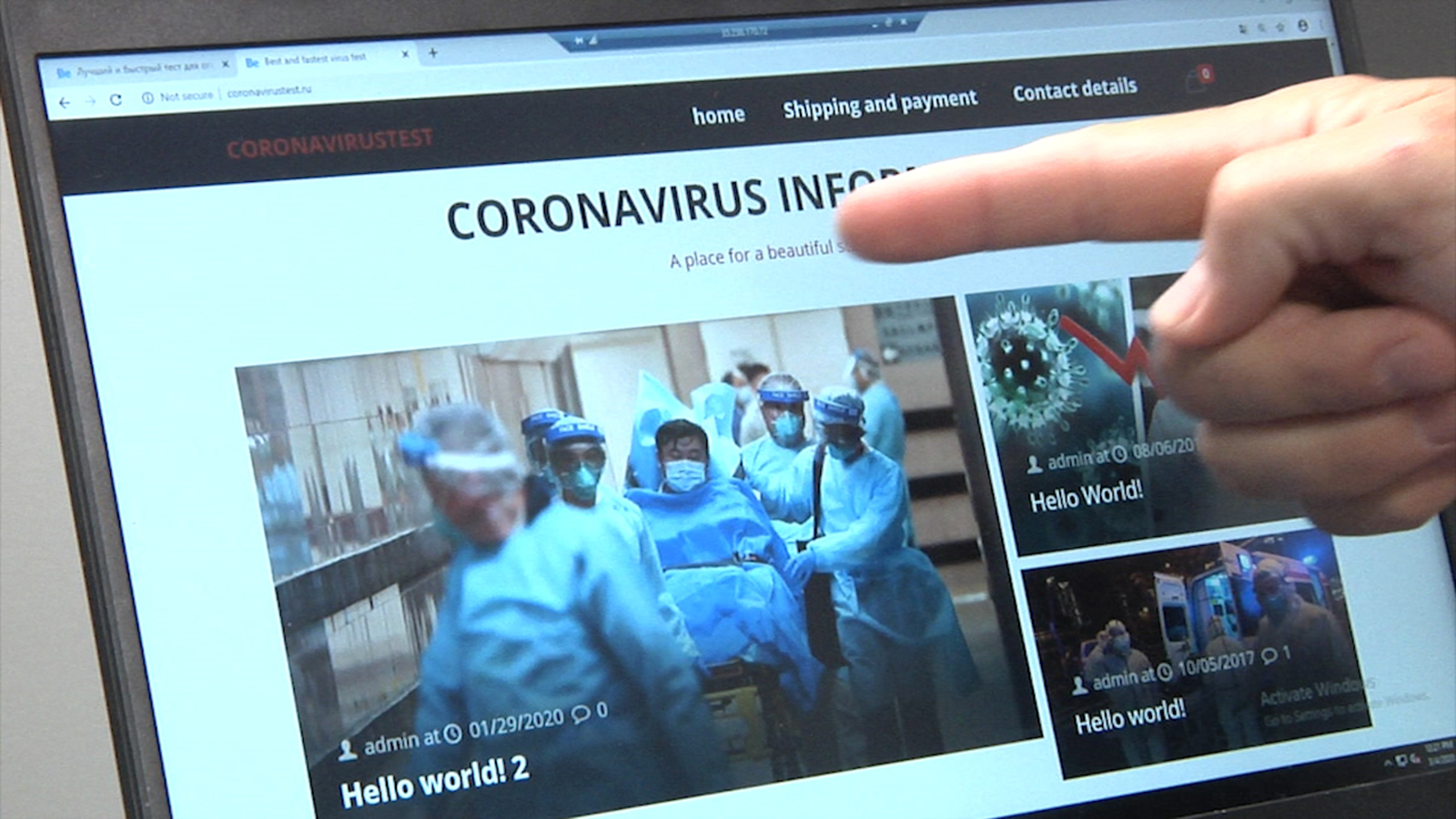
The reason for the investigation were complaints of users, which reported on the forums that they were obsessively offered to download a strange application, allegedly informing about COVID-19 and created by WHO.
As it turned out, the routers of these users were compromised, and under the mask of an application was distributed an infostiller. Only recently I wrote about phishing with letters supposedly from WHO, exploiting the theme of coronavirus, and this seems to be the next technological level from cybercriminals.
The publication says that in all cases, the victims were the owners of D-Link or Linksys routers, and unknown attackers changed the DNS settings on the devices.
“It is not yet clear exactly how the attackers gained access to the devices, but several victims admitted that they could access their routers remotely, and they used weak passwords. So it’s probably a matter of brute force and enumerating credentials from a list of known defaults,” – says Bleeping Computer.
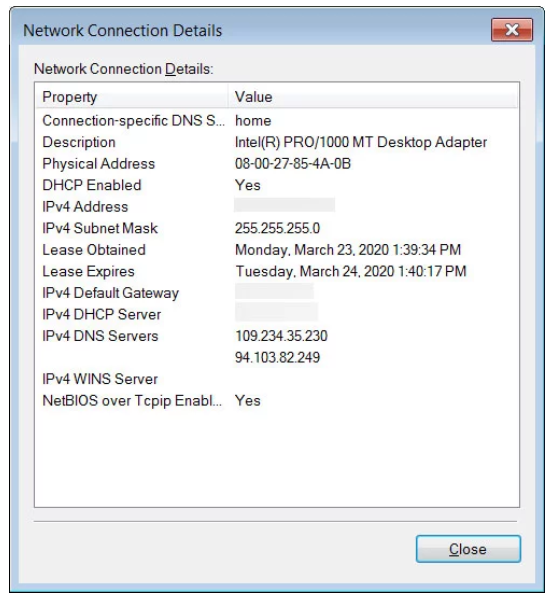
Having gained access to the device, attackers change the DNS server addresses to 109.234.35.230 and 94.103.82.249.
Researchers explain that when a computer connects to a network, Microsoft uses the Network Connectivity Status Indicator (NCSI) feature, which periodically checks to see if your Internet connection is active.
So, in Windows 10, one of these tests will be connecting to http://www.msftconnecttest.com/connecttest.txt and checking if the answer is “Microsoft Connect Test”. If it does, then the computer is connected to the Internet, and if not, Windows will warn that the Internet is not available.
If the user is working with a compromised router, then the malicious DNS servers force Windows, instead of connecting to the legitimate IP address of Microsoft 13.107.4.52, to connect to the intruders resource located at 176.113.81.159. As a result, instead of sending the aforementioned text file, the site displays a page asking the victim to download and install the fake application “Emergency – COVID-19 Informator” or “COVID-19 Inform App”, supposedly created by WHO.
If the user is caught by attackers, and downloads and installs this application, instead of information about the coronavirus, he received the Oski Trojan. This malware will try to collect and transmit the following information to the attackers (the list is incomplete):
- Cookies
- browser history;
- Billing information from the browser
- saved credentials;
- cryptocurrency wallet data;
- text files;
- autocomplete data for forms in the browser;
- DB 2FA Authy identifiers;
- screenshots of the desktop at the time of infection.