Anonymous messaging app Signal becomes increasingly popular amongst regular users. Such a shift turned the attention of various cybercriminals to the app that was clean of scams beforehand. Due to certain specific features, Signal scams are different from what you may normally expect.
In this article, I will go through the most popular ones, and explain how to avoid becoming a victim of scams in Signal messenger.
Is Signal App Safe?
Signal is a pretty secure messaging app, thanks to its end-to-end encryption and strong commitment to user privacy. But like anything popular (or, in this case, quickly gaining popularity), Signal has caught the attention of cybercriminals who use it as a platform for doing their shady things. That eventually led to this messenger being stuffed with various scams.
Its anonymity and a wide range of privacy settings make it particularly hard to understand whether the person who contacted you is real. Contrary to other popular apps like WhatsApp or Facebook Messenger, there is little to way to link the identity of the user with any of the external resources. That opens the gate for an entire flood of impersonation scams. But, let’s get through all the types one by one.
Top 4 Signal Scams
Despite it being possible to run almost any type of scan in Signal, hackers typically opt for ones that contain elements of impersonation. The reason for this, aside from the messenger’s high anonymity, is lack of user knowledge on what scammer tricks they should expect. And below, you can see exactly them.
Fake Job Offers
Scammers often post fake remote job listings or reach out directly with what seems like an amazing opportunity. They’ll ask you to contact them on Signal for details, specifying only a phone number for contact information.
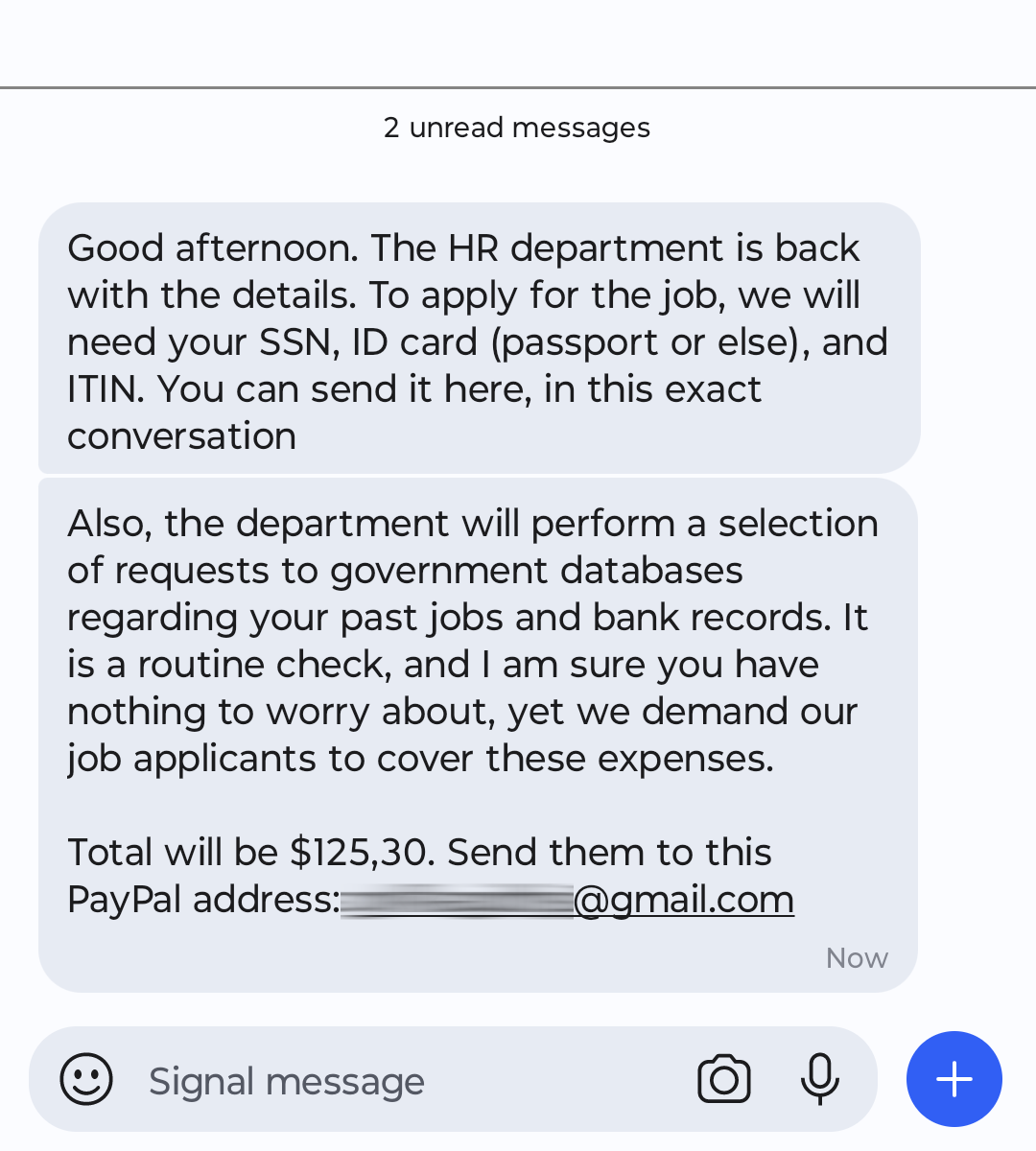
Once you comply, they might request upfront payments for things like training or background checks. Worse, they could ask for sensitive details, such as your Social Security number or banking information. This information can then be used for identity theft or fraud.
Impersonation Scams
Due to the full-anonymous features of Signal, a scammer may pose as someone you know. By using familiar names and profile pictures, they make the profile look like one from a real person. Moreover, if the scammer knows certain facts from your life, they can even mimic your friend, colleague or relative in the conversation.
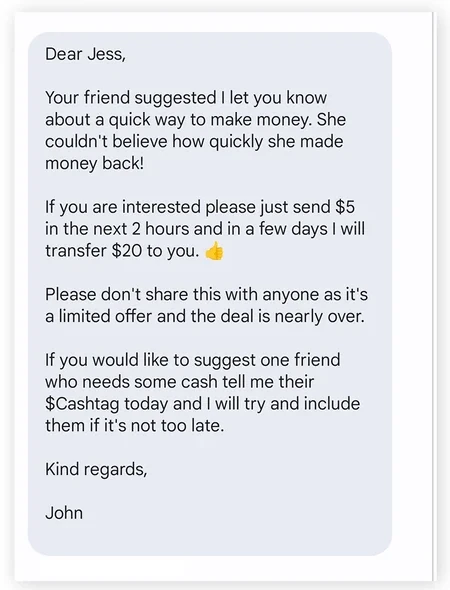
After establishing the initial trust, the scammer switches to the main action. It is either about asking you to lend them money, follow the link or share some sensitive information. As you may guess, none of these cases end up positively for the target user. Con actors may successfully do the trick several times to one person before they start to suspect something.
Romance Scams
Some fraudsters prey on emotions, pretending to be romantic interests. They might claim to live far away, often in another country, and start chatting regularly to build trust. Despite looking as a rather old kind of online scam, it is still quite widespread and keeps targeting all ages.
When the scammer senses your emotional investment, they start abusing it, bit by bit. This might involve a fabricated medical emergency or unexpected travel expenses that you should help them to pay off. Romantic feeling blur the rational thinking a lot, which can make the victim follow the scammers’ instructions for several times before understandign the fraud.
“Wrong Number” Scam
This scam all starts with an innocent-seeming text: “Hey, got my new phone!” or “Oops, wrong number.” If you reply, they’ll try to start a conversation, sharing personal stories or asking about your life. Such kindness may come naturally from some people, so the target may stick to the conversation.
Key acts of the scam may not appear instantly, as in this case, scammers build up the trust from scratch. At some point, the fraudster introduces a “problem” – like being in need for financial help – or pitch an “amazing investment opportunity”. With a few weeks spent in active conversations with the victim, the scammer sits tightly in their trust list, which allows for bigger sums or other uncommon requests.
Keeping Yourself Safe on Signal
Pecularity of the scams on both Signal and in any other messenger or social media is the fact of them being multi-directional. Users may struggle to think of each and every possibility when the fraudster approaches them, especially when they use a completely new angle for it. Nonetheless, a few basic pieces of advice will help to drastically reduce the probability of a successful attack.
First, be cautious about strangers reaching out romantically on Signal. It is better to stick to more traditional dating platforms or make acquaintances in real life than hope for love stories in an all-anonymous messenger. If a flirt is followed by the “send me money” request – cut the conversation short.
If your friend or a close one claims they need you to send them money urgently, but never contacted you on Signal before, calm down and pause. Call or text the real person directly from the other app/on the cell phone to confirm their story. If that is not an option, ask a question that only you and them would know the answer for before taking any action. Wrong answers or attempts to avoid the answer at all are definite signs of you facing an impersonation scammer and the reason to stop the conversation.
As for job offers, real employers won’t insist on using Signal to communicate, and they’ll never ask for money or personal details upfront. Research the company on their official website and check reviews to confirm legitimacy, and also request the confirmation of talking to the company representative.
Overall, avoid engaging with strangers who text you out of the blue. Politely point at them probably mistaking your number for someone else’s and ask to end the conversation. If the person insists and carries on with their topic, block them and delete the conversation. That will save your time and, potentially, quite a lot of money.