A new DarkGate malware deployment campaign has caught the attention of cybersecurity researchers. This was fueled by the developer’s decision to lease its product to a limited number of affiliates.
DarkGate Malware Activity Spikes as Developer Rents Out It
According to cybersecurity researchers, a new DarkGate malware campaign made a fuss. It spreads through phishing emails and uses stolen email threads to trick users into clicking on a hyperlink that downloads the malware. Initial analysis indicates that this malware sample is very similar to the DarkGate malware. The initial infection routine and observed C2 communication protocol were nearly identical to past analyses of the same malware family. However, further research has confirmed that this sample is part of the DarkGate malware family, based on embedded strings and functionality. In addition, the recent surge in DarkGate malware activity is likely because the developer has rented out the malware to a few affiliates.
DarkGate Loader Details
DarkGate is malware sold primarily on underground forums by an user nicknamed RastaFarEye. This malware is designed to avoid detection by security software, and it can establish persistence through Windows Registry modifications to gain elevated privileges. As for damage – it steals data from web browsers, Discord, FileZilla, and other software and connects to a command-and-control (C2) server to perform tasks. Moreover, the task may include file enumeration, data exfiltration, launching cryptocurrency miners, capturing screenshots remotely, and executing other commands.
Spreading
Traditionally, phishing attacks have been the primary delivery route for malware; this case is no exception. In addition, according to some reports, 79% of malware in Q2 2023 was delivered via phishing emails. However, specialists have identified two explicit DarkGate contamination scenarios. The first method involves using an infection pattern wherein an MSI installer file is the initial payload. Thus, victims of this infection receive this file by clicking on a link included in a phishing message. This link leads to a traffic distribution system (TDS). As a result, it redirects the victim to the final payload URL for the MSI download if the attacker’s requirements are met. Upon opening the downloaded MSI file, the DarkGate infection is triggered.
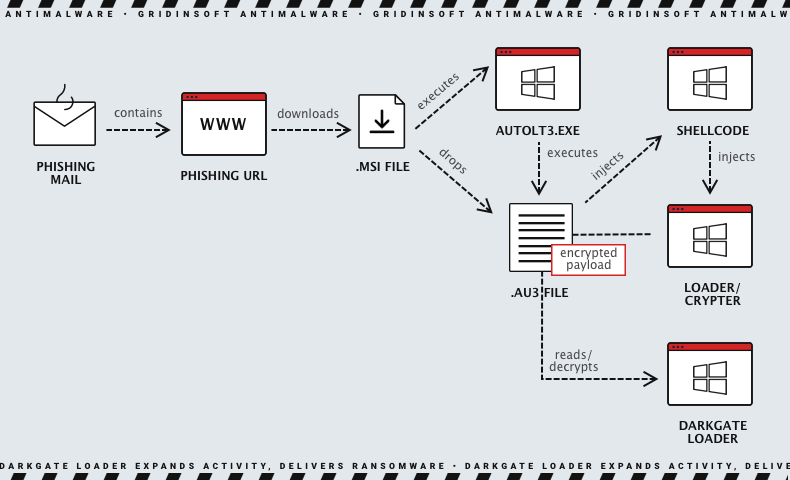
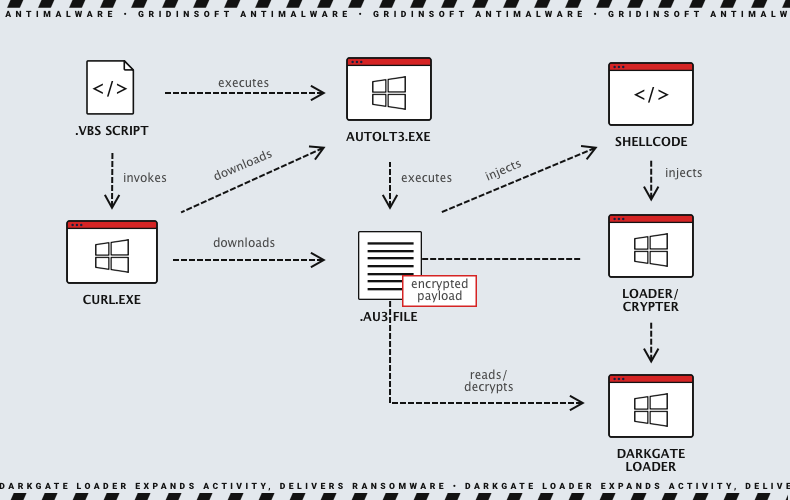
In addition, experts have discovered samples of another campaign with a Visual Basic script to deliver the initial payload. However, experts do not precisely understand how the initial load is delivered to the victim. The script is obfuscated and contains decoy/junk code. Later, it invokes the curl binary that comes pre-installed with Windows to download the AutoIt executable and script file from a server controlled by the attacker. After that, the infection chain follows the previously described campaign.
Key Action of DarkGate Loader
DarkGate is a modular loader that can deliver a variety of payloads, including ransomware, botnets, trojans, keyloggers, spyware, and dll files. In other words, DarkGate Loader is a versatile and dangerous malware that can be used to deliver a variety of payloads. The loader waits for commands from the command server. When C2 sends a message containing the IP address of a secondary server, DarkGate can get the payload.
The malware uses DLL file format to run stealthily by loading the library to the memory using the system process called rundll32.exe or injecting it into an application with a bad to no DLL checkup. As a result, the malware steals confidential data such as passwords and cookies from the victim’s system. It targets web browsers, email software, and applications like Discord or FileZilla. The malware uses legitimate freeware tools published by Nirsoft to extract information, and it can access the operating system, the logged-on user, the currently running programs, and other data sources. This information is sent to the C2 server and is available in the threat actor’s panel. Additionally, the malware can collect arbitrary files from the victim system when requested through the C2 channel.
Defense evasion
After initialization, the malware proceeds to a function identified as the “C2 main loop.” In this loop, the malware periodically checks the C2 server for new instructions, executes the received commands, and sends back the results to the C2 server. The C2 main loop contains over 100 orders, including information gathering, self-management, self-update, stealer, crypto miner, RAT, and file management. The malware contains multiple functions to evade typical analysis tools. If the corresponding features are enabled, and the sample detects an environment that matches one of the checks, it will terminate the process. Moreover, the malware looks for multiple well-known AV products and may alter its behavior depending on the result. The discovered AV product is communicated back to the C2 server. The malware may also masquerade its presence and inject itself into legitimate Windows processes based on the used configuration.
Malware As a Service
Initially, the malware was only used privately by the developer. But now, malware authors offer it as a subscription service, with prices ranging from $1,000 per day to $15,000 per month to $100,000 per year. Moreover, the author claims that the malware is the “ultimate tool for pentesters/redteamers” and boasts of “features that you won’t find anywhere.” By the way, earlier versions of DarkGate also included a ransomware module. In any case, introducing the MaaS program will likely increase DarkGate malware campaigns, making it an ongoing threat in the future.
How to protect against DarkGate Loader?
Here are some tips on how to protect against DarkGate Loader:
- Keep your software up to date. Software updates often include security patches that can help protect your devices from malware.
- Be careful about what websites you visit and what links you click on. Malware, like DarkGate Loader, can spread through malicious websites and links.
- Use a firewall to block unauthorized access to your devices. This can help prevent DarkGate Loader from infecting your devices.
- Back up your data regularly. This way, if your devices are infected with DarkGate Loader, you can always restore your data from a backup.
- Use a strong password manager to create and store strong passwords for your online accounts.
- Enable two-factor authentication (2FA) for your online accounts. This will add an extra layer of security to your accounts.
- Use an anti-malware solution with up-to-date signatures. It will help detect and remove DarkGate Loader if it does manage to infect your device.