3CX Phone System, a desktop app for business phone communication, fell victim to a supply chain attack. Recent updates deliver a forged version of the application that makes it possible to install stealer malware. The actual payload is getting delivered in a 3-stage manner, which makes it harder to track.
What is the 3CX Phone System?
3CX Phone System is a software phone communication program developed by an eponymous company. It provides VoIP communication with a connection to PSTN. All of the operations are served in the cloud, which makes it convenient for use even in small companies. As of the beginning of 2023, the company boasted 12+ million customers in over 600,000 companies around the world. The company provides services to the world’s most-known names, such as Toyota, BMW, Avira, McDonald’s, Boss, Hilton, and IKEA.
Being a company with such success and so notable clients is always a serious responsibility, both image- and cash-worthy. That requires corresponding attention to all the elements of your infrastructure and personnel – to avoid any risks related to security breaches. Supply chain management must be even more diligent in security questions, as consequently linked single-purpose elements are often prone to break. And that is what happened to 3CX.
What is the 3CX supply chain attack about?
Supply chain attacks suppose hacker integration at a certain stage of the supply chain. The researchers who examined the case yet did not find a certain place where the breach could have happened. From what is known now, it is clear that hackers managed to forge the installer and force it doing what they want. That clue points to the fact that crooks made their way to the installer’s source code, as it has no problems with certificates and signatures. The attack itself resembles the SolarWinds hack that happened back in 2020.
After launching the installer, an unsuspecting user will see the routine installation procedure. However, in the background, the binary file will connect to a GitHub repository to get an ICO file. That is actually a second-stage payload, which contains data encoded with base64. Short research shows that this data is a set of shell codes, which execution calls for the next step. They force the system to connect to the C2 and pull the third-stage payload.
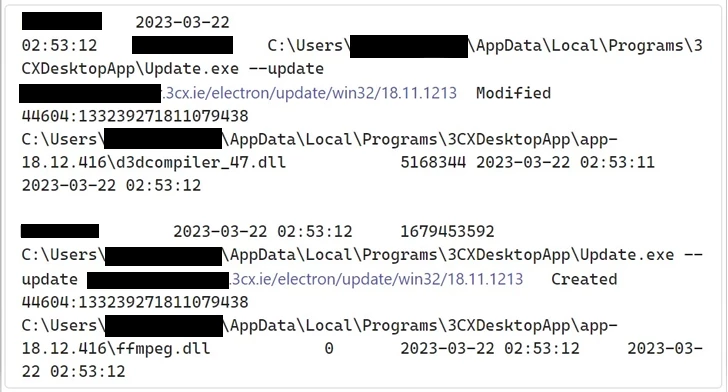
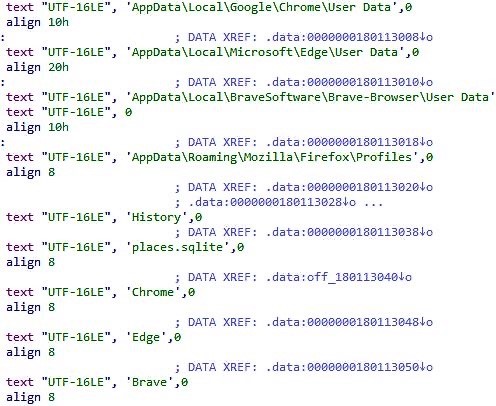
Third stage – the final one – is a DLL file, a classic form of the vast majority of modern malware. After retrieving the library, one of the shellcodes makes it run. It seems to be an infostealer that grabs web browser data from an infected system, particularly browsing history. Malware aims for a pretty short list of browsers – Chrome, Edge, Firefox and Brave. Such behaviour is different from common spyware and stealers, thus the malware is most likely a brand new one, possibly created specifically for this attack. Threat researchers from SentinelOne, who were the first to detect dubious activity, coined it SmoothOperator.
Is the 3CX attack dangerous?
As any other spyware attack, it is. Despite the less-than-usual amount of data collected by the detected stealer, the potential scale of this attack is tremendous. We already mentioned the number of 3CX users worldwide – and imagine how many potential victims may be among them. Yes, not all users have installed the infested update, and some of them were saved by anti-malware software. But it is possible that they are in the minority.
The NHS has issued a cyber alert with a "High" severity ranking warning about this active intrusion campaign, warning "legitimate versions of 3CX DesktopApp have been compromised and are being actively exploited."
Alert here: https://t.co/J3NTs6rMD5 https://t.co/M7yBauSlcy
— Alex Martin (@AlexMartin) March 30, 2023
Given that ignoring the updates is not a very good practice, the only way to protect against such a breach is by using a superb security tool. Its superiority should be defined not only by detection capabilities and amount of functions but also by the zero-trust policy. Regular anti-malware programs generally rely on the trustiness of a program, and will likely ignore malignant activity around a signed installation binary. Zero-trust one, on the other hand, treats any file as potentially hazardous and applies all kinds of checkups to ensure that it is secure.