There is a special trap on the Internet for people, who type the website address into the browser’s address bar, instead of using search. Yes, few people do so in the times of auto-fill, but there are still some romantic souls out there. The trap is called typosquatting, and you can guess what it means from what it sounds.
Typosquatting is a way to benefit from users making typos while entering the website address by hand. How anyone would pull that over, what is the possible win, examples, and nuances of this fraudulent practice is coming up in this article.
What is Typosquatting?
Typosquatting starts with crooks having a ready domain which is a misspelling of a well-known high-traffic website. Like real squatters occupy abandoned buildings without paying for them, typosquatters take Internet domains paying very little for it compared to the possible gain. The benefit comes from harnessing the natural traffic (flowing to the exploited website) or making a typo-based domain a part of a more complex phishing campaign.
A related term to typosquatting is cybersquatting. The relation between these two is such that the former is the special case of the latter. Cybersquatting is any usage of domain names in bad faith, not necessarily related to address misspelling. At the dawn of the domain name system, there were many cases of unprecedented, thus hard to solve, disputes between companies and cybersquatters.
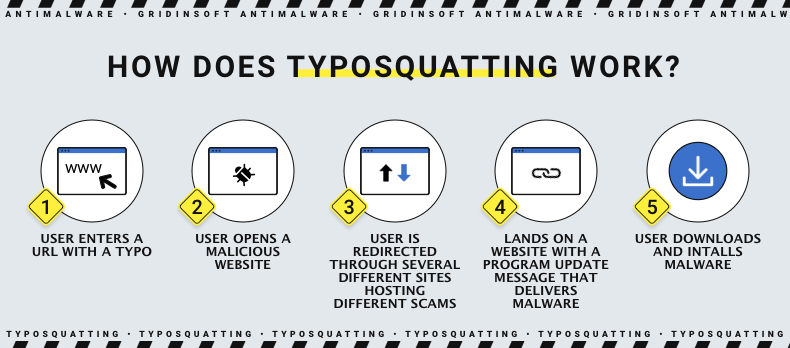
Typosquatting algorithm work
How Does Typosquatting Work?
In order to make their schemes work, frauds need their victims to end up on the spoof instead of a brand website. The error mechanisms that lead users to a trap may vary, and each is reflected in a certain type of domain name concocting.
Typos:
What could be more trivial than a typo? The age of automatic form filling doesn’t stop many of us from quick keyboard access to their most visited websites. And that is understandable, especially when the address is simple and the site is frequently visited. If only it insured the absence of typos!
Spelling mistakes:
Not knowing how to spell a word correctly is not a typo. But that doesn’t stop crooks from landing their victims on pages specially crafted for spelling mistakes of known addresses. Brand owners often buy wrong-spelled domain names in advance, second-guessing the intentions of cybersquatters. Then they set all misspelled addresses to redirect users to the actual brand website.
Top-level domains:
The most Internetish typo-involving fraud schemes are the ones that mess with top-level domain names. TDLs are the website address endings that indicate the country to which the domain refers (.uk, .fr, .us, .io, etc.) or the type of an organization (.com, .org, .gov, etc.) If a TDL is not a part of a website name easily recognizable by ear, the frauds can easily take advantage of users here. Who remembers was it .com or .org after all?
Also, one particular top-level domain is a typosquatters’ hotspot. It is the Colombian national domain .co, which is a common typo of .com – the most used TDL.
Hyphens:
This kind of cybersquatting is more of a spoofing inventory for a phishing attack than typosquatting per se. People don’t randomly or automatically use hyphens, and users are likely to double-check the spelling when they are unsure where to place the symbol. But if the crooks manage to lure someone onto a fake webpage, an incorrectly hyphenated address might serve them as a perfect disguise that wouldn’t trigger suspicion. Who would ever notice an extra hyphen in an address like “johndoe-online-store.com?”
NOTE: Maze ransomware attack is very common in 2022, you should be careful and know the tips on how to prevent.
How to Make Typos Benefit
It is reasonable to ask: ok, someone has accidentally ended up on a squatted webpage. Then what? It turns out that there are many ways to monetize the typos and misspellings.
- Squatters might sell the “surrounding” domains to the owner of a brand whose name the typo-domains exploit. Companies often do so in advance, purchasing the address they want plus the potential misspelled addresses. To early-squat domains related to a brand name means to give credence to that name. It is almost like buying company shares. Naturally, such domains’ prices grow in correspondence with the capitalization of the enterprise.
- The owners of a misspelled address can earn from advertising. Just as simple as that: users who make a typo visit the wrong website where they are being shown some advertisements. The banners might even be catchy enough to hold the gaze for a few seconds. Quite a harmless kind of typosquatting, let us admit that.
- Traffic redirection is another way to profit from typosquatting. The schemers can redirect traffic to the competitors of the brand users attempted to access or the brand itself. Why would they do that, you might ask. The point is to redirect users via a reference link issued by the brand website affiliate program. Then squatters will be paid for each redirected user.
- So-called drive-by malware installation is one of the typosquatter’s darkest practices. They fit their webpages with malicious scripts that start downloading unwanted items on the victim’s device as soon as the latter accidentally steps on the trap site. They can install relatively harmless adware but also full-fledged malware. A decent antivirus program will protect users from accessing such dangerous pages, but no security software leaves web roamers unprotected.
- Phishing campaigns are the no-malware hacking operations powered by social engineering. Hackers deceive users via fraud mailings or otherwise and lure them to spoofed websites. Then, the victims are asked to input their actual account passwords under the pretext of, let us say, regular password change. Unaware users share their most sensitive data with the thieves, who use a misspelled website address to lull their vigilance.
NOTE: Also, read about the most dangerous types of phishing attacks in 2022 that everyone should definitely watch out for.
Examples Of Typosquatting
There were so many happenings of typosquatting that collecting them all is a hopeless cause. These are just several examples of real-world cases.
- Since 2006, the website goggle.com (a typo of google.com) acted as a fraudulent website until 2011, when it started redirecting users to the Google website. However, later, by 2018, it became unsafe again, redirecting to adware pages. Later on, it became recognized by security systems as overtly dangerous.
- One of the most zealous European companies to fight typosquatting is DanishLEGO. The firm spent half a million dollars on UDRP litigations, and the total number of cases amounted to 309.
- Air France company had typosquatting freeloaders right under its nose – the website arifrance.com directed accidental visitors to a travel discount portal. The gap was eventually closed.
- Political typosquatting is a widespread thing. A 2019 report claims that there were 550 typosquatting sites related to the
- A tech support scam campaign used to typosquat Microsoft’s official website with a microaoft.com fake that looked just like the Microsoft site but with the addition of warning messages. They suggested the users consult with the support service of the corporation by phone. The telephone numbers belonged to scammers, of course.
How Not to Become a Victim of Typosquatting in 2022
The first rule is universal against phishing, spoofing, and most types of hacking. Be extremely cautious when dealing with unexpected emails and messages of unclear origin. Never open or download attachments of such letters, nor click on links featured in them. Try to contact the sender via a different channel and ask for confirmation of the letter’s content. If you trust the sender, double-check the links – the first and second domain names (google.com, for example) must match the respective names in the address the link claims to direct to. The Internet can be a dangerous place full of scams and fraud.
Install an effective security program and avoid surfing the web without defense. GridinSoft Anti-Malware is a state-of-the-art solution that meets the requirements of today’s worst cybersecurity challenges. Besides removing infecting agents immediately, it protects your very browsing. The program won’t let you visit a dangerous webpage until you confirm your intention of doing so. Therefore, be attentive and vigilant when you do it, and be aware of the threats.