Email spam is an annoying and unwanted mailing of many letters. This kind of letter comes from unknown sources and sometimes even carries malicious compositions. Often spam emails use the tactics of extortion and intimidation or carry misleading information. But worst of all, attackers can access your smartphone, PC, or other devices through spam email. In this article, you will find a guide on how to delete such annoying emails on Gmail, Yahoo & Outlook services and not receive them.
Ways to Get Rid of Spam Emails
Fortunately for the users, there are plenty of ways of getting rid of annoying messages. Depending on their number, you can try different practices and find the one that works best for your case. For example, simple reports of a couple of phony emails you’ve got over the last month may be enough to prevent their appearance. Popular email services usually keep an eye on users’ reports and will likely react to reports about the malevolent activity. Still, you may sometimes require a much more harsh approach.
1. Mark as spam
Email services such as Gmail, Yahoo & Outlook have special features for filtering unwanted emails. To do this, you need to mark emails as “spam”, after which they will go to the spam folder and will not disturb you in the common list of emails. If you receive such emails from the same sender in the future, it will automatically be sent to this folder.
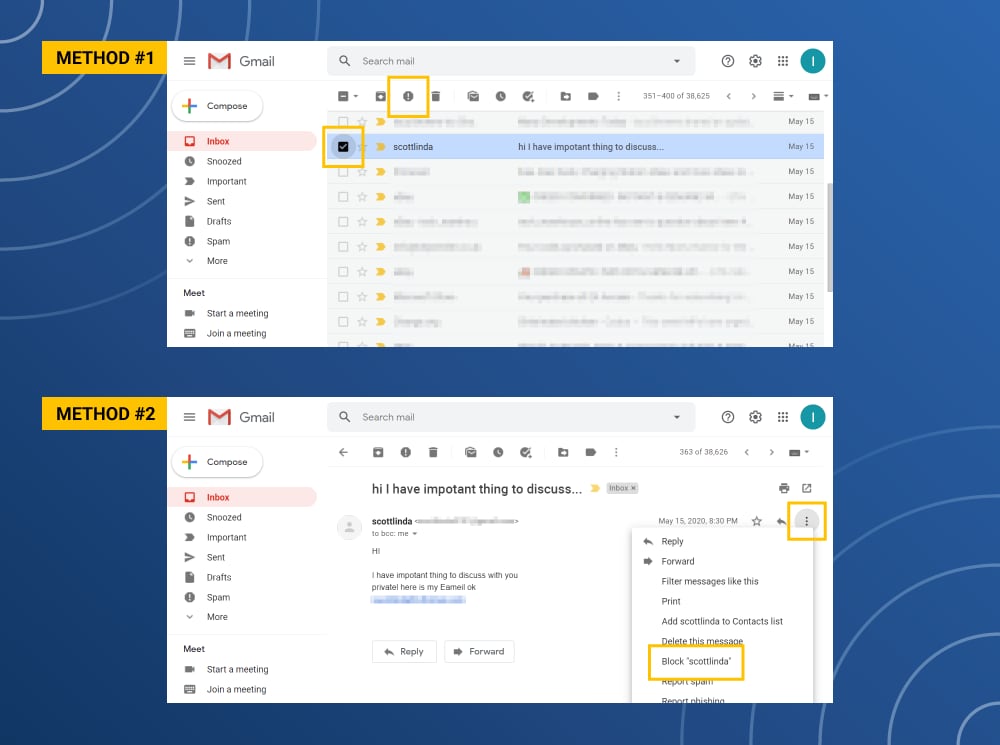
How to mark spam in Gmail
Tap on the square next to the email. After that tap the stop sign icon.
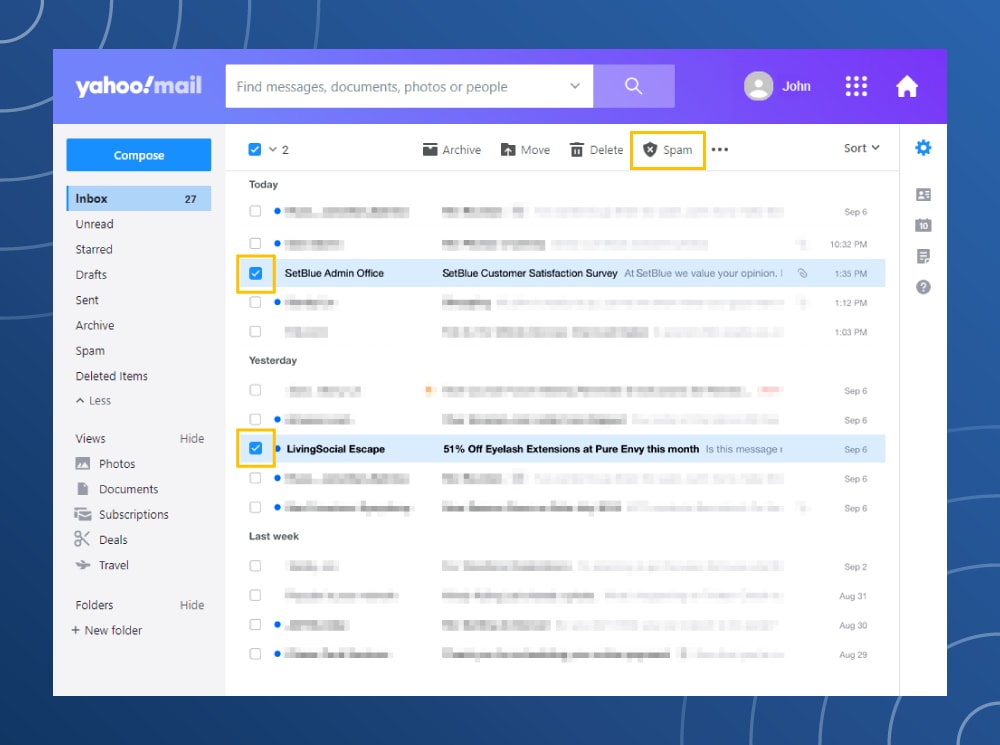
How to mark spam in Yahoo! Mail
Tap the box next to the email or on multiple emails. After that tap on the shield icon.
2. Delete spam emails
Spam email at first glance looks harmless. But there are a few nuances that you need to consider. First of all, if you notice that your mailbox is filled with letters from unknown sources, do not click on them. By clicking on these emails, you will inform the attacker that your email is active and will be subject to more spam. The harm is that you will start receiving even more spam emails. Only if you follow links or respond to spam – that’s when you can come across the distribution of malware and other things. The best thing you can do is simply remove spam emails and rid yourself of unnecessary content.
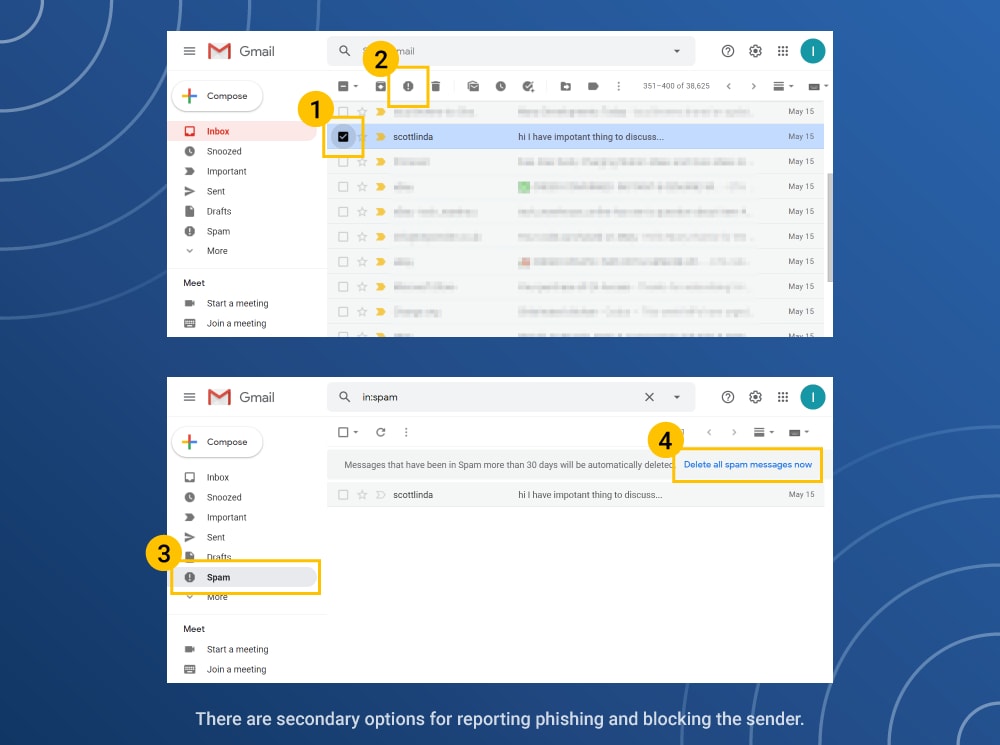
How to delete spam from Gmail
- Tap on the empty box to check out the message.
- Tap on the stop sign in the top menu.
- Tap Report Spam in the dropdown menu.
- Tap on the “Delete All Spam Messages Now option.”
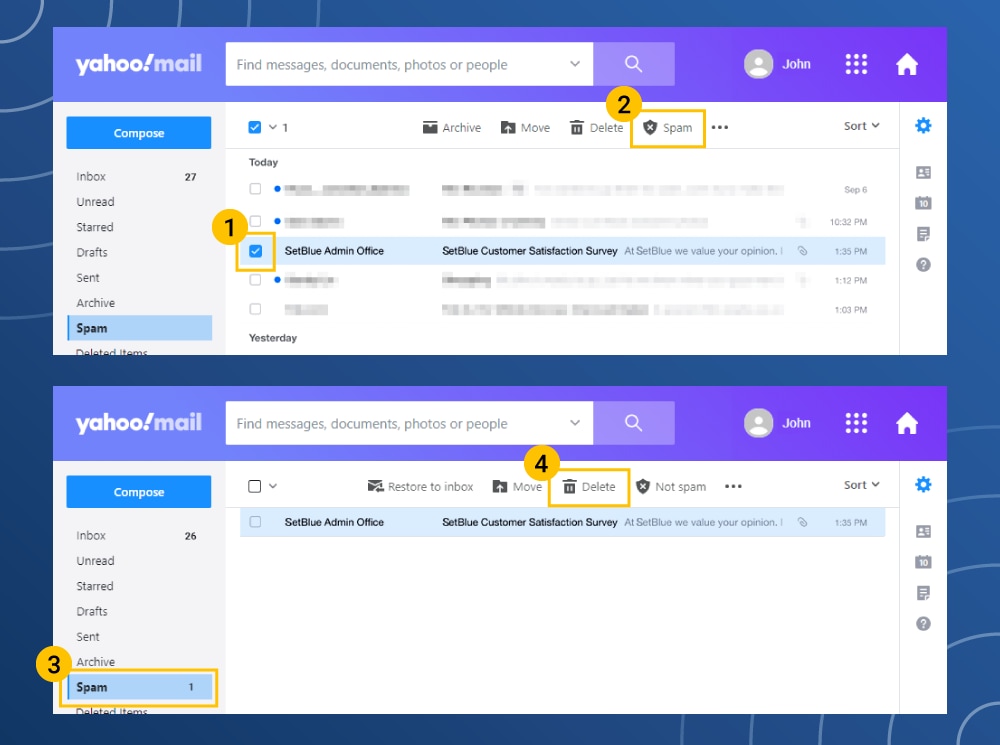
How to delete spam from Yahoo! Mail
- Firstly, check the box next to the email.
- In the above menu tap on the shield.
- Tap the Report Spam option.
- Go to the spam folder.
- Tap the Delete Emails option.
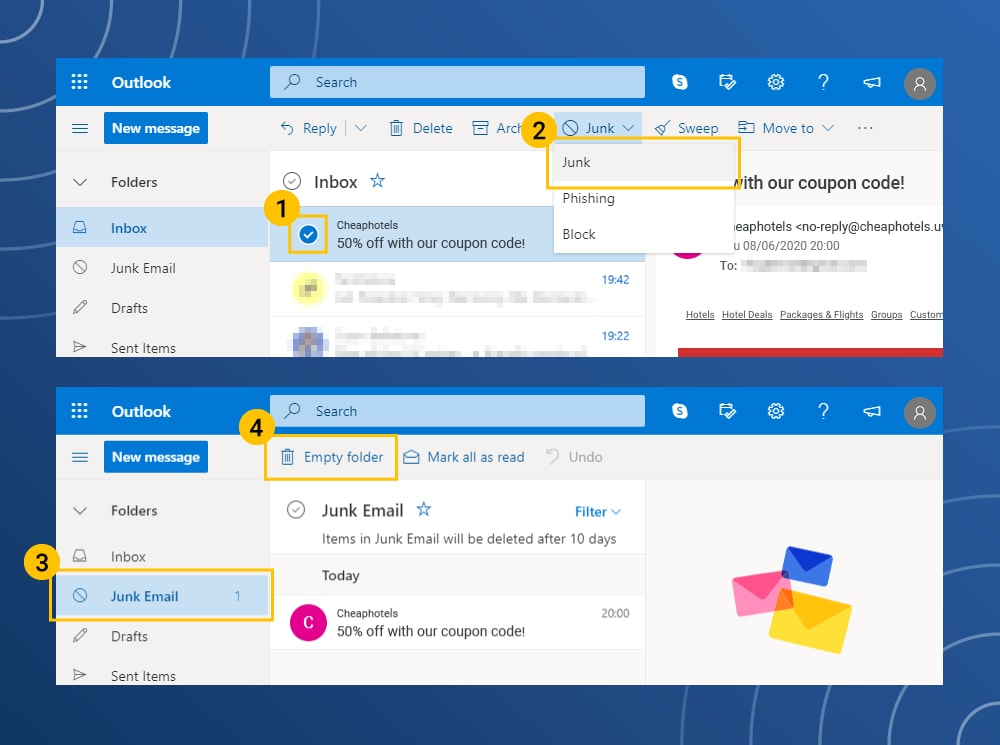
How to delete spam from Microsoft Outlook
- Tap the email in the inbox area.
- Tap on the Junk Mail option in the top menu.
- In the side menu click on the Junk Email tab.
- To empty the folder click the metal trash can.
3. Keep your email address private
Try to avoid sharing your email on different platforms to avoid receiving spam emails. If you don’t have to share your email address, you better keep it quiet. You can also change your account privacy settings. As in the following examples:
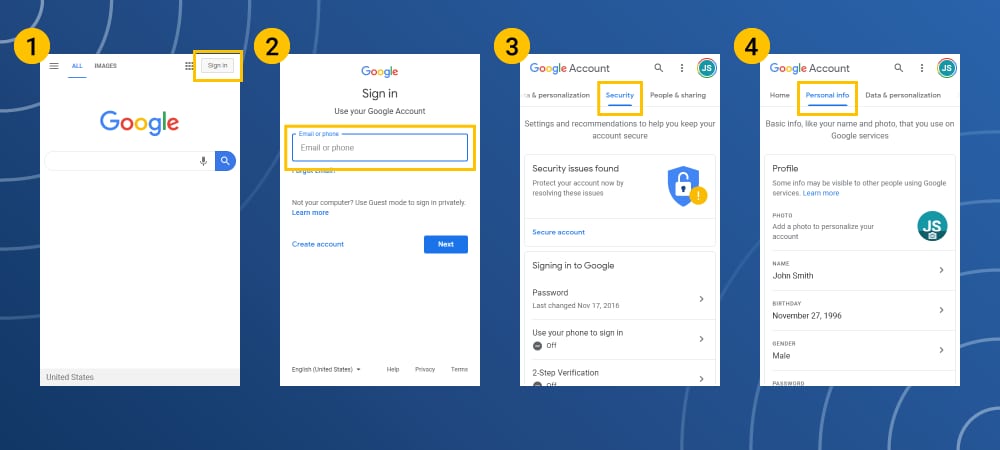
Google Privacy Settings
- Enter your Google account.
- Navigate to the Security Checkup option to see the devices, security events and other email addresses and devices connected to your Gmail account.
- Set up the toggle switches to turn features on or off.
- Do the same process for the Personal Information and Privacy settings.
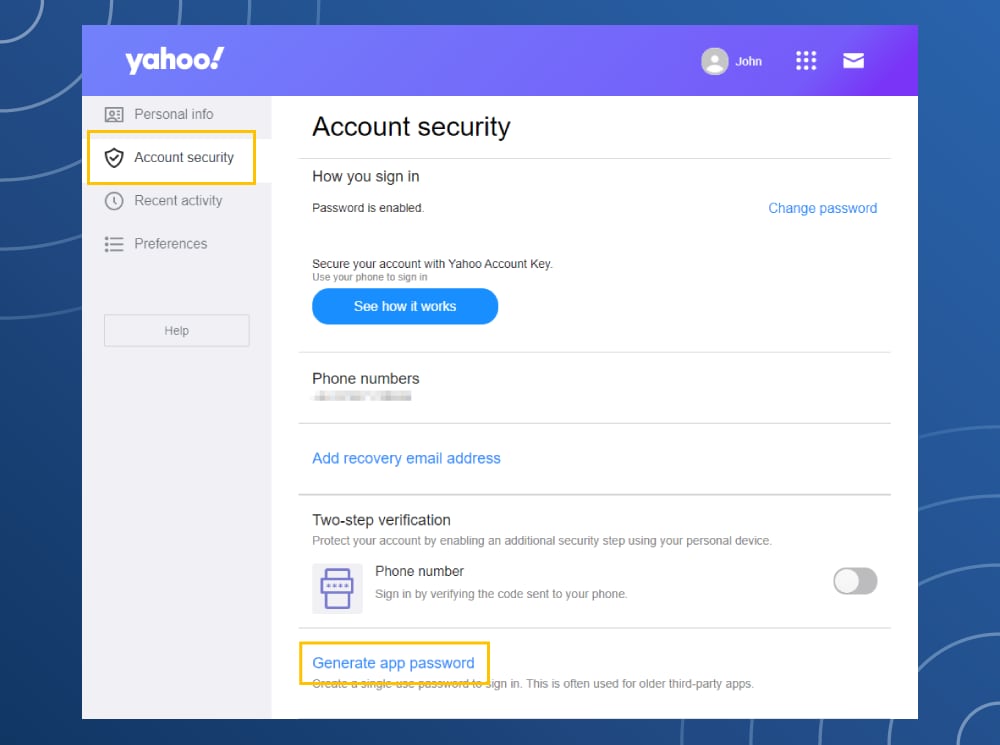
Yahoo! Mail privacy settings
- Log-in to your Yahoo! Mail Account.
- Click on the gear icon.
- Click the Account Information option.
- In the Account Security section, click on the Generate app password option.
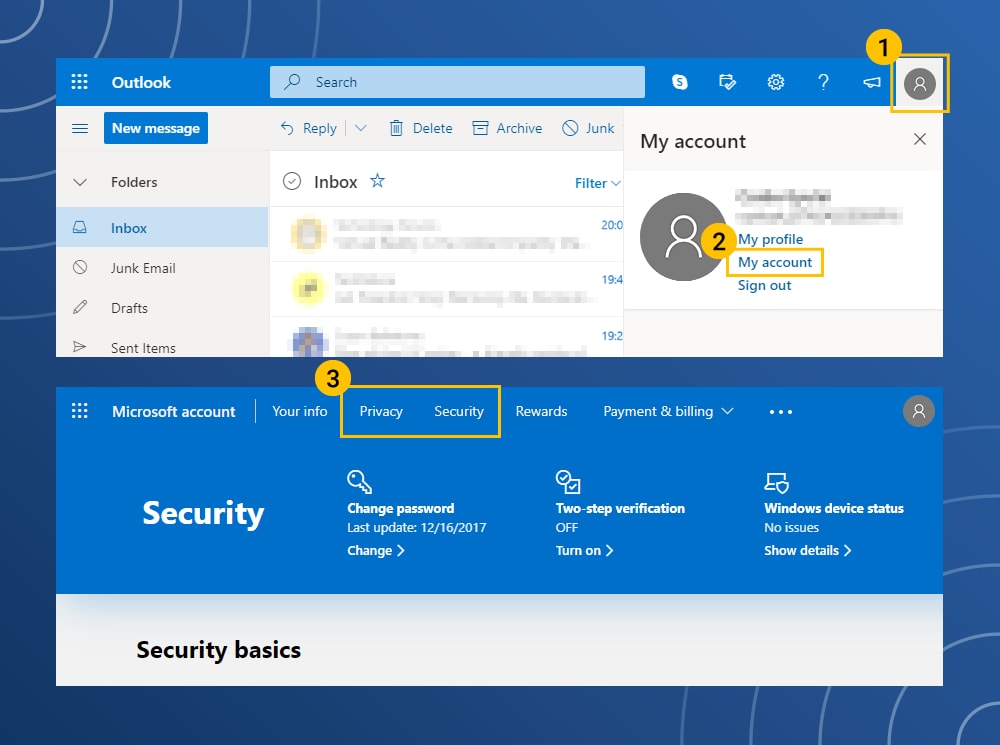
Microsoft Outlook privacy settings
- In the upper-right corner of the screen tap on your account icon.
- In the menu list, tap My Account.
- Tap on the Privacy and Security options to change the settings.
4. Use a third-party spam filter
Each mailbox has its spam filter, but working with a third-party filter can provide additional protection. All emails will pass through these two filters. This way, you can provide adequate protection against malware and unwanted content. Finding an anti-spam filter that will work with your service provider is best.
5. Change your email address
If spam still comes to your email address after all the steps above, then the problem is the continuous leak of your personal info, in particular email address. In this case, you need to change your email address. To do this, see the following guide.
- Register a new account with your current email service.
- After that, notify your contacts from your new account that you’ve changed email addresses.
- Go to the Settings section and add the new email address to forward incoming emails from your old account. It is important to specify the emails you want to redirect the messages from. Otherwise, all the spam will appear in the new mailbox as well.
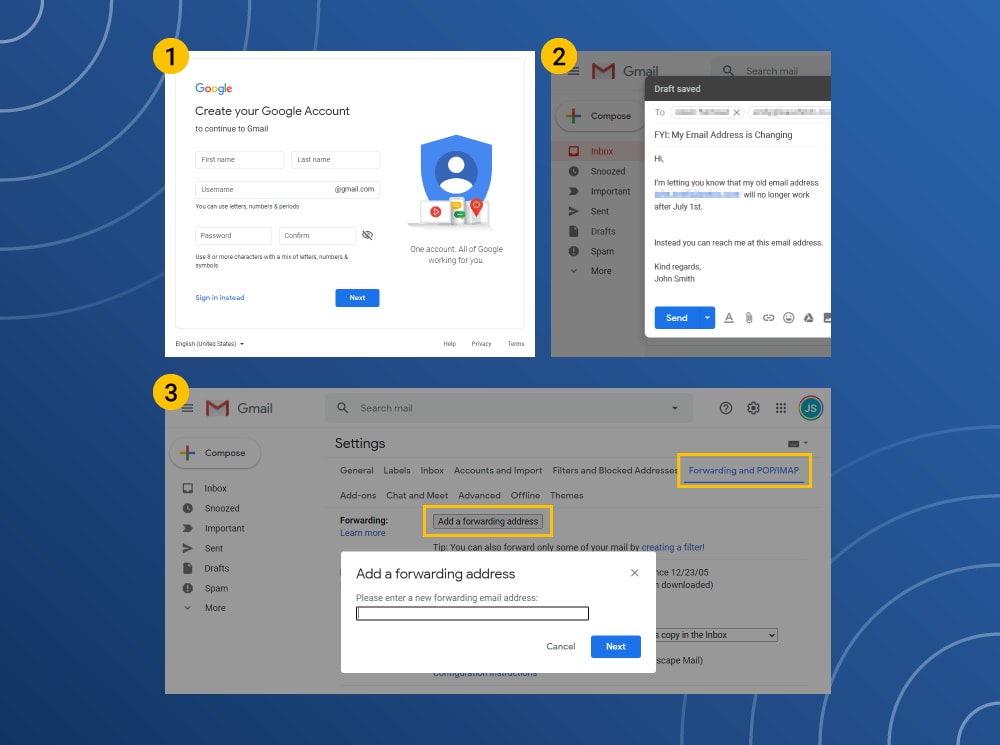
How to add a forwarding address
After you create a new email address, you will be able to receive emails from the old email address. To do this, you need to change your forwarding settings. By redirecting, you will be able to update your contact information in all accounts that are linked to your original account.
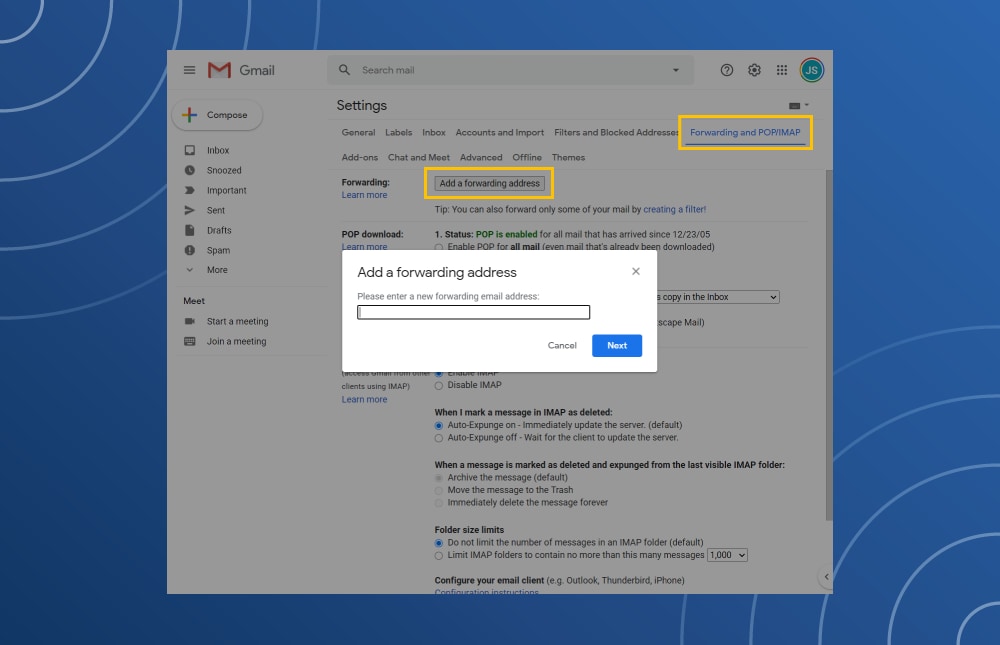
- In the old email account, navigate to the Settings option.
- Tap the Forwarding and POP/IMAP tab.
- Enter the new email address in the Add a forwarding address box.
- Tap “Next” to confirm the process.
Common spam email security threats
In addition to being annoying and time-consuming, spam emails can compromise users’ digital security. Attachments that are attached to spam emails often carry a virus or malware. Here is a list of the most common ones.
Trojan Virus
Trojans are malware disguised as legitimate apps. Get on the user’s PC they can by downloading free apps or come through attachments in email. Trojan installs malicious code, usually spyware or coin miners, via a link attached to an email. Thus, the attacker manages to control the user’s computer, steal data and block many programs. From this point of view, remember that clicking on all composed spam emails is dangerous.
Phishing and vishing
Phishing emails are one of the most common attacks in this case. Since, in letters of this kind, the attacker imitates the messages of legitimate companies and firms, trying to extract the necessary information for him. In the Phishing email, it is suggested to go to the attached link and confirm your data or credit card details. It’s a scheme to steal sensitive data.
Vishing is also used to steal data only through calls. Intruders call users and, during the conversation, extort card numbers, personal data, addresses, insurance numbers, etc. To avoid falling victim to Phishing and Vishing, check the legality of the companies that call or write to you. Also, try to answer only those calls in your phone book.
Zombie Computer Virus
Zombies are a type of malware that can spread via spam email. This program turns the user’s computer into a server through which it sends spam to other users. You won’t be able to see the moment when this malware will be on your computer, but slow PC operation will be the first sign that it is. Moreover, an infected computer can attack web pages. To avoid this, you should not click on the attached links in spam emails.
How to stay free of spam emails?
You can take all the steps mentioned above only if you are a victim of spam mailing. If you only know about it and do not want to face such a problem directly, then take the recommended precautions. Use the spam filters we mentioned earlier. Do not spread your email address on different platforms and sites. Also, try not to click on pop-ups and banners that carry annoying and malicious content. Finally, be careful when visiting untested and unprotected sites, and especially leaving there your main email address. If you need to browse such pages time to time, that will be a great solution to create a separate email address that will take all the potential spam.